http://defensetech.org/2014/10/22/navy-stands-up-cyber-security-task-force/#more-23941The US Navy has established a special new unit designed to protect computer networks and improve cyber security across the service called Task Force Cyber Awakening, or TFCA, service officials said.
Created in August of this year, TFCA is a 100-person force dedicated to establishing protocols, identifying vulnerabilities, increasing cyber awareness and shoring up security and access with the Navy’s computer networks, service leaders explained.
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
Monikohan valtio saa nysvätä jenkkien datoja ilman ilmoituksia sun muita? Britit ja Iipot ovat erikoisessa asemassa siinä suhteessa.
http://www.nationaljournal.com/tech...to-access-u-s-data-without-a-warrant-20141028British authorities are capable of tapping into bulk communications data collected by other countries’ intelligence services—including the National Security Agency—without a warrant, according to secret government documents released Tuesday.
The agreement between the NSA and Britain’s spy agency, known as Government Communications Headquarters or GCHQ, potentially puts the Internet and phone data of Americans in the hands of another country without legal oversight when obtaining a warrant is “not technically feasible.”
The data, once obtained, can be kept for up to two years, according to internal policies disclosed by the British government. GCHQ was forced to reveal that it can request and receive vast quantities of raw, unanalyzed data collected from foreign governments it partners with during legal proceedings in a closed court hearing in a case brought by various international human-rights organizations, including Privacy International, Liberty U.K., and Amnesty International. The suit challenges certain aspects of GCHQ’s surveillance practices.
It is well known that the NSA and GCHQ closely share intelligence data with one another, as part of a long-standing surveillance partnership. Some details of the agencies’ spy pact were exposed by former NSA contractor Edward Snowden last year, including the existence of GCHQ’s Tempora program, which taps into fiber-optic cables to scoop up online and telephone traffic across the Web for up to 30 days.
But this is the first time the British government has disclosed that it does not require a warrant to access data collected and maintained by its American counterparts. The revelation appears to counter statements made by an oversight committee of the British Parliament in July of last year that “in each case where GCHQ sought information from the U.S., a warrant for interception, signed by a minister, was already in place.”
http://www.dslreports.com/shownews/...gainst-Verizon-For-Its-Stealth-Cookies-131186A few weeks ago I noted how security researchers had discovered that Verizon has been injecting a unique new 'stealth cookie' identifier into all user traffic that tracks user online behavior, even if the consumer opts out. Using a unique Identifier Header, or UIDH, Verizon's ham-fisted system broadcasts your identity all across the web — and remains intact and open to third-party abuse — even if you opt-out of Verizon's behavioral ad programs. Now the Electronic Frontier Foundation has filed a complaint with the FCC and has strongly indicated that they're considering legal action against Verizon for violating consumer privacy laws.
https://www.eff.org/deeplinks/2014/11/starttls-downgrade-attacksRecently, Verizon was caught tampering with its customer's web requests to inject a tracking super-cookie. Another network-tampering threat to user safety has come to light from other providers: email encryption downgrade attacks. In recent months, researchers have reported ISPs in the US and Thailand intercepting their customers' data to strip a security flag—called STARTTLS—from email traffic. The STARTTLS flag is an essential security and privacy protection used by an email server to request encryption when talking to another server or client.1
By stripping out this flag, these ISPs prevent the email servers from successfully encrypting their conversation, and by default the servers will proceed to send email unencrypted. Some firewalls, including Cisco's PIX/ASA firewall do this in order to monitor for spam originating from within their network and prevent it from being sent. Unfortunately, this causes collateral damage: the sending server will proceed to transmit plaintext email over the public Internet, where it is subject to eavesdropping and interception.
Kenenköhän käskyllä tämä tehtiin? Toimitusjohtajan?
http://www.theregister.co.uk/2014/11/12/stuxnet_patient_zero/Malware researchers have named five Iranian companies infected with Stuxnet , identifying one as 'patient zero' from which the worm leaked to the world after causing havoc in the Natanz uranium plant.
Joint research by Kaspersky Lab and Symantec found the organisations, contractors to Natanz, were targeted between June 2009 and March 2010 and suffered 12,000 infections from 3280 Stuxnet samples.
The two companies' latest findings, also published in Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon do not agree with accounts in a New York Times article that Stuxnet was delivered straight to Natanz from where it escaped into the wild to be picked up by researchers and re-purposed by malware writers.
Researchers were able to glean the new information published in January and updated with victims' names today because Stuxnet code retained information about the targets it infected, creating new executables for each.
"Stuxnet remains one of the most interesting pieces of malware ever created," Kaspersky analysts wrote. "The targeting of certain high profile companies was the solution" to infect Natanz.
Symantec reverse engineer (@Liam O Murchu) said it was confident Stuxnet leaked from the initial targets.
"Based on the analysis of the bread crumb log files, every Stuxnet sample we have ever seen originated outside of Natanz," O'Murchu said.
"... every sample can be traced back to specific companies involved in industrial control systems-type work."
The companies included Behpajooh identified as patient zero from where the worm leaked to the world; Foolad Technic Engineering Co which developed blueprints for Iran's industrial control systems; the sanctioned Neda Industrial Group; Control-Gostar Jahed Company, and Kala Electric a sanctioned firm that developed centrifuges.
The sophisticated malware was widely thought to be the work of the US and Israel created under Operation Olympic Games launched by the Bush Administration and continued under President Obama.
It contained four zero day vulnerabilities, making it both expensive in terms of the research typically required to discover the flaws, and highly targeted having been designed to target the specific systems used in the Natanz facility. ®
http://www.lewrockwell.com/2014/11/simon-black/brazil-builds-a-fiber-optic-network/November 11, 2014Santiago, Chile
This past week Brazil announced that it will be building a 3,500-mile fiber-optic cable to Portugal in order to avoid the grip of the NSA.
What’s more, they announced that not a penny of the $185 million expected to be spent on the project will go to American firms, simply because they don’t want to take any chances that the US government will tap the system.
It’s incredible how far now individuals, corporations, and even governments are willing to go to protect themselves from the government of the Land of the Free.
The German government, especially upset by the discovery of US spying within its borders, has come up with a range of unique methods to block out prying ears.
They have even gone so far as to play classical music loudly over official meetings so as to obfuscate the conversation for any outside listeners.
They’ve also seriously contemplated the idea of returning back to typewriters to eliminate the possibilities of computer surveillance.
More practically, the government of Brazil has banned the use of Microsoft technologies in all government offices, something that was also done in China earlier this year.
The Red, White, and Blue Scare has now replaced the Red Scare of the Cold War era. And it comes at serious cost.
From Brazil’s rejection of American IT products alone, it is estimated that American firms will lose out on over $35 billion in revenue over the next two years.
Tietenkään jenkit anna tämän mennä läpi.
http://www.wired.com/2014/11/usa-freedom-act-fails-in-senate/Senate lawmakers working to reform NSA surveillance were struck a fatal blow tonight when a critical bill that would have curbed some of the spy agency’s controversial activity failed to obtain enough votes.
In one of their last acts before the year sunsets, pro-reform Senators attempted to advance the USA FREEDOM Act but failed by just two votes to obtain the 60 votes needed to move the bill forward.
Democrats, who maintain the majority in the Senate, were eager to push the bill through during the end-of-year session before Republicans assume the majority position next year. Civil liberties groups, which support reforms currently laid out in the bill, considered tonight’s vote the last-gasp chance for the bill to move forward before some of its staunchest supporters hand over seats lost in the November elections.
The bill would have put an end to the government’s controversial bulk collection of phone records from U.S. telecoms—a program first uncovered by USA Today in 2006 but re-exposed in 2013 in leaks by NSA whistleblower Edward Snowden. The bill would instead have kept records in the hands of telecoms and forced the NSA to obtain court orders from the Foreign Intelligence Surveillance Court to gain access to them. It would also have required the agency to use specific search terms to narrow its access to only relevant records.
Additionally, the bill would have allowed service providers more transparency in disclosing to the public the number and types of requests they receive from the government for customer data. The government in turn would have had to be more transparent about the number of Americans caught up in its data searches. The NSA has said in the past that it has no idea how many Americans are caught up in national security collection efforts that target foreign suspects.
OldSkool
Kapteeni
Eipä näytä vielä olevan muualla, joten laitan tänne. Jonne tämä kuuluukin, nimittäin regin on ilmeisesti ihan Vakoilusofta:
http://www.bbc.com/news/technology-30171614 kirjoittaa että
Regin-niminen haittaohjelma on Symantecin mukaan kiertänyt maailmaa jo kuusi vuotta ja vakoillut niin valtiollisia kuin yksityisiäkin toimijoita.
Regin kykenee muun muassa ottamaan ruutukaappauksia, varastamaan salasanoja ja palauttamaan jo poistettuja tiedostoja.
Regin, new computer spyware, discovered by Symantec
http://www.bbc.com/news/technology-30171614 kirjoittaa että
Regin-niminen haittaohjelma on Symantecin mukaan kiertänyt maailmaa jo kuusi vuotta ja vakoillut niin valtiollisia kuin yksityisiäkin toimijoita.
Regin kykenee muun muassa ottamaan ruutukaappauksia, varastamaan salasanoja ja palauttamaan jo poistettuja tiedostoja.
Regin, new computer spyware, discovered by Symantec
A leading computer security company says it has discovered one of the most sophisticated pieces of malicious software ever seen.
Symantec says the bug, named Regin, was probably created by a government and has been used for six years against a range of targets around the world.
Once installed on a computer, it can do things like capture screenshots, steal passwords or recover deleted files.
Experts say computers in Russia, Saudi Arabia and Ireland have been hit most.
It has been used to spy on government organisations, businesses and private individuals, they say.
Researchers say the sophistication of the software indicates that it is a cyber-espionage tool developed by a nation state.
They also said it likely took months, if not years, to develop and its creators have gone to great lengths to cover its tracks.
Sian John, a security strategist at Symantec, said: "It looks like it comes from a Western organisation. It's the level of skill and expertise, the length of time over which it was developed."
Symantec has drawn parallels with Stuxnet, a computer worm thought to have been developed by the US and Israel to target Iran's nuclear program.
That was designed to damage equipment, whereas Regin's purpose appears to be to collect information.
Tässä parempi kuvaus.
http://www.theregister.co.uk/2014/11/24/regin/A highly advanced malware instance said to be as sophisticated as the famous Stuxnet and Duqu has has been detected attacking the top end of town. "Regin" has security researchers opining it may be nastier than both.
The "Regin" malware is thought to be developed by a nation-state because of the financial clout needed to produce code of this complexity. The malware targets organisations in the telecommunications, energy and health sectors.
Symantec malware reversers found attackers have foisted Regin on targets using mixed attack vectors including one unconfirmed zero-day in Yahoo! Messenger.
"Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen," Symantec's researchers wrote.
"Customisable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organisations, infrastructure operators, businesses, researchers, and private individuals.
"It is likely that its development took months, if not years, to complete and its authors have gone to great lengths to cover its tracks. Its capabilities and the level of resources behind Regin indicate that it is one of the main cyber espionage tools used by a nation state."
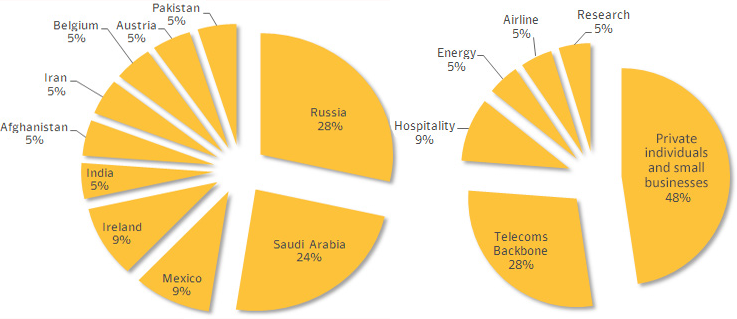
Regin's targets. Source: Symantec
The security firm did not name a nation as the source of Regin, but is willing to say most of its victims were from Russia and Saudi Arabia and were targeted between 2008 and 2011 with a since decommissioned version of the malware that re-surfaced after 2013.
Regin's rampage. Source: Symantec
About half of those targeted were private individuals and small business, and a quarter telco backbone operators. Hospitality, energy, airline and research organisations round out the remainder in about equal measure.
Russia and Saudi Arabia soaked up half of the total attacks, followed by Mexico and Ireland at nine percent apiece.
"Its design makes it highly suited for persistent, long term surveillance operations against targets," the researchers wrote.
The highly-complex malware was comparable only to Stuxnet and Duqu, researchers said in the report Regin: Top-tier espionage tool and many of its elements were undiscovered.
Regin can install many highly customised payloads including remote access trojans to swipe keystrokes and screenshots, tools to nab information on processes and memory utilisation, and others to recover deleted files.
Specialist modules were found monitoring Microsoft Internet Information Services network traffic, parsing mail from Exchange databases, and collecting administration traffic for mobile base station controllers.
Regin's talented authors encrypted data blobs after the stage one vector. The stage zero dropper probably responsible for setting extended attributes and registry keys that held encoded data of subsequent stages was not found.
Researchers found some 64 bit versions that were different from the 32 bit variant in the use of file names and modifications to stage one as a kernel mode driver. Stages three and five of 64 bit versions were not found. ®
OldSkool
Kapteeni
Huhuja ... lihavoin kiinnostavimmat väitteet .http://www.digitoday.fi/tietoturva/...tti-leukoja-lehti-nimeaa-tekijat/201416284/66 kirjoittaa 24.11.2014 22:40 että
Jos tuo on totta niin Iso-Britannia on lojaalimpi USA.n tarpeille kuin EU:n yhteistyölle. Ei tuo nyt ihan yllätys ole.
Edith: muotoilua ja loppukommentti.
Lähteenä on käytetty https://firstlook.org/theintercept/2014/11/24/secret-regin-malware-belgacom-nsa-gchq/The Interceptin mukaan Regin-vakooja on Yhdysvaltain tekemä. Kehittämiseen osallistui kuitenkin myös toinen valtio, eikä se tällä kertaa ollut Israel.
Tietoturvayhtiö Symantec toi äskettäin julki poikkeuksellisen hienostuneen vakoojaohjelman Reginin, jota on jo verrattu muun muassa Yhdysvaltain ja Israelin tekemään Stuxnet-kyberaseeseen.
The Intercept -lehti kirjoittaa omien tutkimustensa ja turvallisuusalan lähteidensä perusteella, että Reginin tekivät Yhdysvallat ja EU-maa Iso-Britannia. Varsinkin jälkimmäinen on merkittävä paljastus tai ainakin väite, sillä lehden mukaan Reginillä tehtiin muun muassa Edward Snowdenin raportoima isku belgialaista teleyhtiötä Belgacomia vastaan.
Reginiä väitetään käytetyn muutenkin EU:n vastaiseen vakoiluun, ja haittaohjelmaa on löydetty EU:n tietojärjestelmistä, joita Yhdysvaltain NSA on vakoillut.
Veikkailu Reginin alkuperästä alkoi tietenkin heti Symantecin raportin jälkeen. Kiinaa on ennen The Interceptin artikkelia pidetty yhtenä mahdollisena tekijänä.
Jotkut epäilivät Reginistä jopa Venäjää, mutta tässä ei äkkiseltään näyttänyt olevan paljoa järkeä, sillä Venäjä oli Symantecin mukaan kärsinyt haittaohjelmasta eniten.
Belgacomin tartunnan siivoamiseen palkattiin Fox IT -niminen yritys, jonka asiantuntijalla Ronald Prinsillä ei ole epäselvyyttä Reginin alkuperästä.
– Analysoituani tämän haittaohjelman ja katsottuani Snowdenin [aiemmin julkaistut] asiakirjat, olen vakuuttunut, että Reginiä käyttävät brittiläiset ja amerikkalaiset tiedustelupalvelut, Prins lausui The Interceptille.
Jos tuo on totta niin Iso-Britannia on lojaalimpi USA.n tarpeille kuin EU:n yhteistyölle. Ei tuo nyt ihan yllätys ole.
Edith: muotoilua ja loppukommentti.
http://electrospaces.blogspot.co.nz/2014/11/incenser-or-how-nsa-and-gchq-are.htmlRecently disclosed documents show that the NSA’s fourth-largest cable tapping program, codenamed INCENSER, pulls its data from just one single source: a submarine fiber optic cable linking Asia with Europe.
Until now, it was only known that INCENSER was a sub-program of WINDSTOP and that it collected some 14 billion pieces of internet data a month. The latest revelations now say that these data were collected with the help of the British company Cable & Wireless (codenamed GERONTIC, now part of Vodafone) at a location in Cornwall in the UK, codenamed NIGELLA.
For the first time, this gives us a view on the whole interception chain, from the parent program all the way down to the physical interception facility. Here we will piece together what is known about these different stages and programs from recent and earlier publications.
https://firstlook.org/theintercept/2014/12/13/belgacom-hack-gchq-inside-story/When the incoming emails stopped arriving, it seemed innocuous at first. But it would eventually become clear that this was no routine technical problem. Inside a row of gray office buildings in Brussels, a major hacking attack was in progress. And the perpetrators were British government spies.
It was in the summer of 2012 that the anomalies were initially detected by employees at Belgium’s largest telecommunications provider, Belgacom. But it wasn’t until a year later, in June 2013, that the company’s security experts were able to figure out what was going on. The computer systems of Belgacom had been infected with a highly sophisticated malware, and it was disguising itself as legitimate Microsoft software while quietly stealing data.
Last year, documents from National Security Agency whistleblower Edward Snowden confirmed that British surveillance agency Government Communications Headquarters was behind the attack, codenamed Operation Socialist. And in November, The Intercept revealed that the malware found on Belgacom’s systems was one of the most advanced spy tools ever identified by security researchers, who named it “Regin.”
The full story about GCHQ’s infiltration of Belgacom, however, has never been told. Key details about the attack have remained shrouded in mystery—and the scope of the attack unclear.
veffeade
Eversti
Niin siis heikoin lenkki on itseasiassa nuo tukiasemat. Käytetty tekniikka on kaikkien tiedossa joten ei ihme että tälläisia saadaan pystyy ilman että vakoiltava piiiiittttkääään aikaan havaitsee mitään: Toimivat sivussa kuin mikä tahansa tukiasema; normikäyttäjä ei huomaa mitään paitsi että kaikki liikenne menee jokos NSA:lle tai sitten Putilille (FSB?)...3G-verkossa sekä puhelin että tukiasema tunnistavat toisensa. Jos puhelin on niin paska ja tyhmä, ettei varoita jos tunnistus menee pieleen, niin...
http://www.iltalehti.fi/ulkomaat/201412130065106_ul.shtml
Käsittääkseni tämän mahdollistaa se, jotta liikenne päätelaitteesta on salattu tukiasemaan asti, mutta siitä eteenpäin selkokielistä?...
Tässä jotain asian tiimoilta...
http://www.netlab.tkk.fi/opetus/s38118/s99/htyo/41/murtaminen.shtml
Hesari kuljeskeli Helsingissä saman Cryptophonen kanssa, joka antoi vinkin Norjassa valetukiasemista.
Epäilyttävää verkkotoimintaa havaittiin mm. Kulosaaressa lähetystöalueella.
http://www.hs.fi/kotimaa/a1418737230344?jako=166aef1eb83942dc8667989c30aec87d
Epäilyttävää verkkotoimintaa havaittiin mm. Kulosaaressa lähetystöalueella.
http://www.hs.fi/kotimaa/a1418737230344?jako=166aef1eb83942dc8667989c30aec87d
"Helsingin Sanomien käyttämät laitteet havaitsivat verkkohäiriöitä ainakin Tehtaankadun loppupäässä ja Kulosaaren lähetystöalueella."
Ei hirveästi yllätä. Mutta mikä yllättää on että luuri ei osaa kertoa käyttäjälleen, että mistä on kyse vaikka softassa olisi mahdollisuus antaa käyttäjälleen ilmoitus mitä luotain havaitsi muuten kuin värejä käyttämällä.
Ei hirveästi yllätä. Mutta mikä yllättää on että luuri ei osaa kertoa käyttäjälleen, että mistä on kyse vaikka softassa olisi mahdollisuus antaa käyttäjälleen ilmoitus mitä luotain havaitsi muuten kuin värejä käyttämällä.
Itseä mietityttää oliko Soneran valtakunnallisen verkon virhetilanne (ja inhimillinen virhe) tahallisesti järjestelty, jotta näitä vieraan tahon valeasemia saataisiin paikallistettua? Ainakin ajoitus on sopiva ja varmasti tuossa katkon aikana voitaisiin kuunnella mistä säteilee 

Itseä mietityttää oliko Soneran valtakunnallisen verkon virhetilanne (ja inhimillinen virhe) tahallisesti järjestelty, jotta näitä vieraan tahon valeasemia saataisiin paikallistettua?
En usko että oli tahallisesti järjestetty, henkilökohtaisesti kun on tiedossa heidän töppäilyjään ja siitä miten he valehtelevat viimeiseen asti (yksityiselle henkilölle ja isoille liikeasiakkaille) ennenkuin kylmä totuus pakottaa heidät myöntämään virheensä.
Jos Sonera olisi tarjonnut tälläistä selitystä, niin olisin voinut uskosa sillä SS7:n ongelmat vaikuttavat hyvin moneen asiaan puhelinverkoissa.
http://www.washingtonpost.com/blogs...isten-to-your-cell-calls-and-read-your-texts/German researchers have discovered security flaws that could let hackers, spies and criminals listen to private phone calls and intercept text messages on a potentially massive scale – even when cellular networks are using the most advanced encryption now available.
The flaws, to be reported at a hacker conference in Hamburg this month, are the latest evidence of widespread insecurity on SS7, the global network that allows the world’s cellular carriers to route calls, texts and other services to each other. Experts say it’s increasingly clear that SS7, first designed in the 1980s, is riddled with serious vulnerabilities that undermine the privacy of the world’s billions of cellular customers.
The flaws discovered by the German researchers are actually functions built into SS7 for other purposes – such as keeping calls connected as users speed down highways, switching from cell tower to cell tower – that hackers can repurpose for surveillance because of the lax security on the network.
Those skilled at the myriad functions built into SS7 can locate callers anywhere in the world, listen to calls as they happen or record hundreds of encrypted calls and texts at a time for later decryption. There also is potential to defraud users and cellular carriers by using SS7 functions, the researchers say.
These vulnerabilities continue to exist even as cellular carriers invest billions of dollars to upgrade to advanced 3G technology aimed, in part, at securing communications against unauthorized eavesdropping. But even as individual carriers harden their systems, they still must communicate with each other over SS7, leaving them open to any of thousands of companies worldwide with access to the network. That means that a single carrier in Congo or Kazakhstan, for example, could be used to hack into cellular networks in the United States, Europe or anywhere else.
“It’s like you secure the front door of the house, but the back door is wide open,” said Tobias Engel, one of the German researchers.
http://www.theregister.co.uk/2014/1...nely_spying_where_they_shouldnt_for_12_years/Slipping out unpleasant news at awkward times is a well-known PR practice – but the NSA has excelled itself by publishing on Christmas Eve internal reports detailing its unlawful surveillance.
The agency dumped the docs online shortly after lunchtime on December 24, when most journalists are either heading home to their families or already drunk.
The quarterly reports were created for the President’s Intelligence Oversight Board (PIOB), and cover the spying powerhouse's conduct from the final quarter of 2001 to the first half of last year.
The files have been heavily censored, but still manage to show that, either by accident or design, NSA staff routinely engaged in illegal surveillance with almost no comeback from management.
Take, for example, the case of a female analyst who used the NSA's vast databases to conduct a little research on her husband. The report covering the first quarter of 2012 states that she accessed her hubby's personal telephone records to look for possible "targets," over a period of three years, and when found out was "advised to cease her activities."
In the same quarter, a spot check discovered three analysts without proper clearance were snooping through data collected under the Foreign Intelligence Surveillance Act. Follow-up checks found another nine analysts who were doing the same thing, and all had their access to that data revoked.
A report from 2003 found that at Edward Snowden's old office, the Kunia Regional Security Operations Center, a contractor working as a systems administrator used the account of an accredited analyst to conduct their own research. When this was discovered, the contractor got a briefing on proper security procedures, the report states.
Judging from the hundreds of reports of mistakes being made, the NSA should perhaps spend a little less time and money breaking into the computer systems of friendly powers, and a lot more training its staff.
Page after page of reports detail how someone accessed the wrong data by mistake, or inadvertently, or even a couple of cases of analysts ending up searching for their own data in the NSA's files. Emails containing raw signals intelligence were also sent out to people without clearance, who were then asked to delete the data and, presumably, try to forget they'd seen it.
Not that it matters that much; as long as the NSA continues to file the reports with PIOB, it is fulfilling its regulatory requirements by law. But it doesn't have to tell the public, which provides its tax-funded activities, however – that takes a lawsuit.
Which is why we have the documents now. The civil liberties body ACLU sued the NSA for the right to see the reports, and the courts sided with the group. The organization was only able to file the request thanks to knowing specifically what to ask for, thanks to internal documents leaked to the world by Edward Snowden. ®
Security researcher Mikko Hyppönen from F-Secure told the newspaper Helsingin Sanomat and Finland's MTV news that rumours have been circulating for several months about the Lizard Squad group of hackers who say they disrupted the two computer games console networks on Christmas Day. He confirmed that at least one of them is a Finn. One of the hackers, in a Skype interview from Finland by Britain's Sky News, said that the attack was carried out for amusement and to expose security flaws in the networks. Hyppönen told Helsingin Sanomat and MTV that his company has been aware of the hacker group for several months. 'According to our information, the group has members in the United States, Canada, England and at least one member in Finland,' he told MTV. The nationalities of other members that participated in the Christmas attack have not been confirmed. Hyppönen noted that these kinds of groups come and go, and that their members are usually young.
Henkilökohtaisesti pitää sanoa, että olen nähnyt asian kummaltakin puolelta ja Hyppönen on oikeassa, se mikä syöksi Sonyn alas on toistuva ilmiö meidän globaalissa kultuurissa missä lahjakkaita nuoria löytyy tupien perältä ihan riittävästi, mutta vain harvat etenevät tähän bisnekseen toisten pestautuessa firmojen palvelukseen.