Korsumajuri
Kapteeni
tuplat
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
 Uskomatonta.
Uskomatonta.Tarkoitan tilannetta jossa Ylen pääuutiset muuttuu PravdaPrimetimeksi minun voimatta vaikuttaa asiaanSe suoltaa sitä jo nyt.
http://www.theregister.co.uk/2016/08/15/air_gap_breached_by_disk_drive_noise/Researchers from Israel's Ben-Gurion University of the Negev Cyber Security Research Center have found a way to exfiltrate information from a PC using the noise created by hard disk drives.
In work detailed here (PDF) at ArXiv, the researchers explain how they've created malware that “can generate acoustic emissions at specific audio frequencies by controlling the movements of the HDD's actuator arm.”
Acoustic attacks on air-gapped computers are nothing new: researchers have found ways to use speakers and microphones to exfiltrate data. Other work has even used a PC's fan to exfiltrate data, either with fan noise or by vibrating a PC's chassis. Security wonks have cottoned on to that and decently air-gapped machines now omit fans, speakers and microphones. Paranoid users will deploy such machines alongside electro-magnetic defences so that computers' and monitors' fugitive emissions can't be read.
Just how attackers can install malware on such machines isn't addressed in the paper. But as Stuxnet shows, where there's a will …
So let's just assume that someone manages to get this malware, dubbed “DiskFiltration”, onto a machine. The authors of the paper envisage that the malware will be coded to seek out data like passwords, encryption keys or key-logging data. When it finds the data it wants, the malware will instruct a disk's actuator arm to perform fake “seek” operations that produce “noise patterns at a certain frequency range.”
Many hard disks now include a feature called automatic acoustic management (AAM) that deliberately dampen seek noise to prevent attacks like these. The researchers say their tests were run with AAM on its default settings.
Once the disk-swinging malware is running a nearby smartphone or other recording device will then listen in to those frequencies and should be able to transcribe the binary output at “180 bits/minute (10,800 bits/hour) and a distance of up to two meters (six feet).”
You're not going to download a movie at that speed, but for a password or key you don't need to.
The good news is that there are simple countermeasures that can stop this attack. The first is to use solid state disks. Another is to tweak AAM settings. Or you could ban smartphones from getting anywhere near air-gapped PCs, which is standard practice in lots of secure areas
...
– Mistä luulette, että MEFin tukikohdan suurin elektomagneettinen merkki oli lähtöisin? Majoitusalueelta. Miksikö? Siksi, koska kaikilla oli puhelimet päällä. Täytyykö meidän kerätä heiltä puhelimet pois? Neller kysyy.
...
http://www.politico.com/story/2016/08/palantir-defense-contracts-lobbyists-226969When a little-known Silicon Valley software startup began vying for national security contracts, it went up against an entrenched bureaucracy and opposition from major contractors skilled in the Washington game.
But quickly, Palantir began pulling pages from the defense industry’s own playbook — bulking up on lobbyists, challenging the Pentagon’s contracting rules and getting members of Congress to sprinkle favorable language into defense legislation. Seven years later, the secretive firm has landed $1.2 billion worth of federal business, and critics say the legislative favors it has secured will give it a leg up on billions more.
Representatives of the firm — founded by venture capitalist and prominent Donald Trump supporter Peter Thiel — insist it remains an outsider in a Washington culture deeply wedded to the status quo.
But a review of public documents and interviews with key players shows the company is no stranger to Beltway politics and influence. Its lobbying expenditures more than tripled to more than $1 million in a few short years as it enlisted lawmakers such as Republican Sens. John McCain of Arizona and Tom Cotton of Arkansas to help it compete against established players like Raytheon and Northrop Grumman. Now, about 40 percent of Palantir’s business comes from government clients, and it appears to be winning a fight with the Army over a $3 billion program to build a new battlefield intelligence network.
…
Thiel, the co-founder of PayPal, got the Central Intelligence Agency to invest $2 million through In-Q-Tel, the agency’s venture capital arm. That granted Palantir access to the inner workings of government contracting — and it quickly learned how the game is played.
http://yle.fi/uutiset/kiina_taistel...an_ensimmaisella_kvanttisatelliitilla/9097990Kiina on laukaissut avaruuteen maailman ensimmäisen kvanttisatelliitin, valtiollinen uutistoimisto Xinhua kertoi tiistaina.
Kiinalaistutkijat lähettävät satelliitin kautta koeviestejä Pekingin ja Luoteis-Kiinassa sijaitsevan Ürümqin kaupungin välillä. Tarkoituksena on kehittää maailmanlaajuinen viestintäverkosto, jota ei voi murtaa tai salakuunnella hakkerien perinteisin keinoin.
Kvanttiviestinnässä käytetään atomia pienempiä valohiukkasia, fotoneja, välittämään viesti kahden pisteen välillä. Jos tällainen viesti koetetaan siepata tai viestiä yritetään salakuunnella, lähettäjä saa siitä tiedon ja viesti muuttuu tai tuhoutuu.
Kiina panostaa avaruusohjelmaan
Tutkijat ovat aiemmin onnistuneet lähettämään kvanttiviestejä maan pinnalla suhteellisen lyhyiden etäisyyksien päähän. Satelliitteihin perustuva järjestelmä mahdollistaisi sen, että kvanttisalattuja viestejä voitaisiin lähettää nopeasti kauas.
Xinhuan mukaan viestinnän onnistuminen vaatii, että satelliitti on tismalleen oikeassa asennossa maan pinnalla oleviin vastaanottoasemiin nähden.
– Se on kuin heittäisi kolikon 100 kilometriä merenpinnan yläpuolella lentävästä lentokoneesta täsmälleen pyörivän säästöpossun reikään, projektin johtaja Wang Jianyu kuvaili Xinhualle.
Kiina on käyttänyt viime vuosina huomattavan paljon rahaa salatun viestinnän kehittämiseen. Kiinan mukaan sen avaruusohjelma on rauhanomainen. Yhdysvaltain puolustusministeriö on syyttänyt Kiinaa siitä, että sen tarkoituksena on estää muita käyttämästä avaruudessa olevia laitteitaan mahdollisten kriisien aikana.
Lähteet:
AP, AFP, Reuters
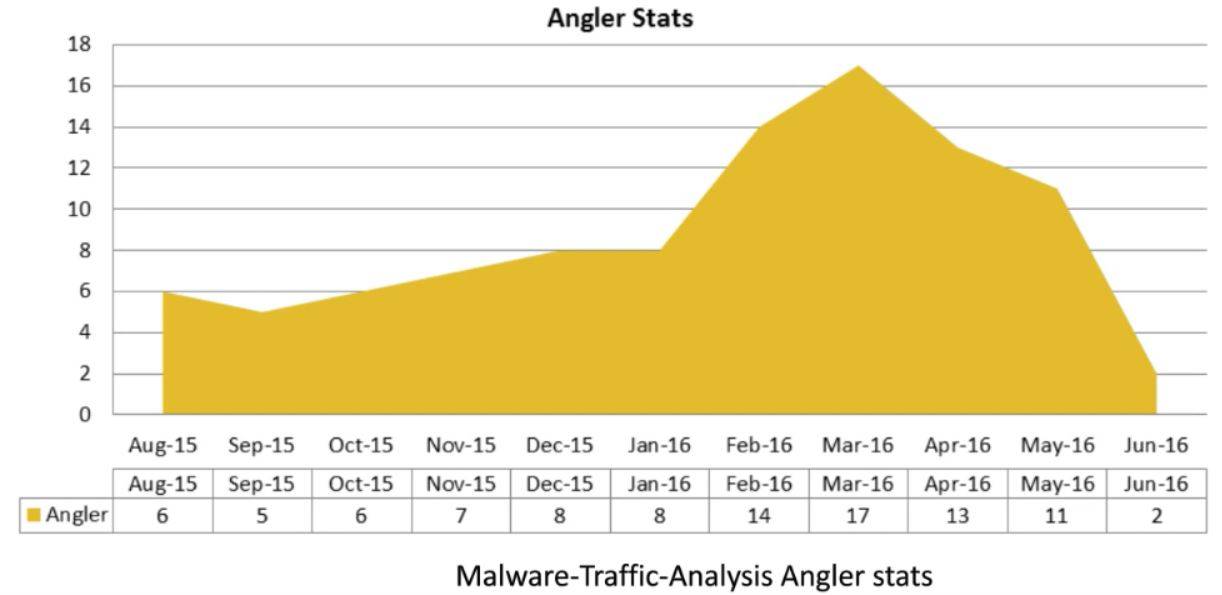
http://www.theregister.co.uk/2016/08/16/angler_8734564567/The Angler exploit kit has all-but vanished and whoever knows why isn't talking.
Angler was the most powerful and sought-after exploit kit on the market boasting rapid integration of new vulnerabilities that made it able to employ zero day attacks on Flash, Java, and Silverlight. It also employed a battery of complex obfuscation tricks including file-less infection and bypassing of Microsoft's lauded EMET security tool.
At its then peak, the authors were responsible for a whopping 40 percent of all exploit kit infections having compromised nearly 100,000 websites and tens of millions of users, generating some US$34 million annually.
Two years earlier the malware was responsible for a mere 17 per cent of infections.
But since June Angler has hardly been sighted.
The intelligence community has its theories: perhaps its authors were arrested right in a covert operation staged by Europol. Or maybe Russian agents bagged and blackmailed them, maybe even dropping one or two into the Black Sea, goes another.
https://cybersecpolitics.blogspot.co.uk/2016/08/why-eqgrp-leak-is-russia.htmlFirst off, it's not a "hack" of a command and control box that resulted in this leak. Assuming it's real (I cannot confirm or deny anything here - largely because I don't know), it's almost certainly human intelligence - someone walked out of a secure area with a USB key. So let's go down the list of factors that make it "Almost Certainly Russia".
- Timing: Seems almost certain to be related to the DNC hacks. High level US political officals seemed quite upset about the DNC hacks, which no doubt resulted in a covert response, which this is then likely a counter-response to. As Snowden put it: Somebody is sending a message that they know about USG efforts to influence elections and governments via cyber.
- Mention of corruption and elections in the text of the release feels classicly Russian
- Ability to keep something this big quiet for three years (leak is just post-Snowden) is probably limited to only those with operational security expertise or desire to leverage those bugs for themselves
- Information results from HUMINT, not simple hack of a C2 box as suggested (not that even that would be easy). Level of difficulty: Very Experienced Nation State.
- Alternate possibility: someone was sitting on a redirector box and the most incompetent person on Earth uploaded this ops disk to it to make their lives easy. Still means someone was hiding on this box who knows what they're doing in an unusually skilled way.
- No team of "hackers" would want to piss off Equation Group this much. That's the kind of cojones that only come from having a nation state protecting you.
- Wikileaks also has the data (they claim)
"Conventional Wisdom from Russian Intel!"
https://securelist.com/blog/incidents/75812/the-equation-giveaway/August 13, 2016 saw the beginning of a truly bizarre episode. A new identity going under the name ‘ShadowBrokers’ came onto the scene claiming to possess files belonging to the apex predator of the APT world, the Equation Group [PDF]. In their initial leak, the ShadowBrokers claimed the archive was related to the Equation group, however, they didn’t provide any technical details on the connections.
Along with some non-native rants against ‘Wealthy Elites’, the ShadowBrokers provided links to two PGP-encrypted archives. The first was provided for free as a presumptive show of good faith, the second remains encrypted at the time of writing. The passphrase is being ‘auctioned’, but having set the price at 1 million BTC (or 1/15th of the total amount of bitcoin in circulation), we consider this to be optimistic at best, if not ridiculous at face value.
The first archive contains close to 300MBs of firewall exploits, tools, and scripts under cryptonyms like BANANAUSURPER, BLATSTING, and BUZZDIRECTION. Most files are at least three years old, with change entries pointing to August 2013 the newest timestamp dating to October 2013.
As researchers continue to feast on the release, some have already begun to test the functional capabilities of the exploits with good results.
Having originally uncovered the Equation group in February 2015, we’ve taken a look at the newly released files to check for any connections with the known toolsets used by Equation, such as EQUATIONDRUG, DOUBLEFANTASY, GRAYFISH and FANNY.
While we cannot surmise the attacker’s identity or motivation nor where or how this pilfered trove came to be, we can state that several hundred tools from the leak share a strong connection with our previous findings from the Equation group.
http://arstechnica.com/tech-policy/...nsa-spying-tools-is-tied-to-russian-dnc-hack/Two former employees of the National Security Agency—including exiled whistleblower Edward Snowden—are speculating that Monday's leak of what are now confirmed to be advanced hacking tools belonging to the US government is connected to the separate high-profile hacks and subsequent leaks of two Democratic groups.
https://www.wired.com/2016/08/shadow-brokers-mess-happens-nsa-hoards-zero-days/When the NSA discovers a new method of hacking into a piece of software or hardware, it faces a dilemma. Report the security flaw it exploits to the product’s manufacturer so it gets fixed, or keep that vulnerability secret—what’s known in the security industry as a “zero day”—and use it to hack its targets, gathering valuable intelligence. Now a case of data apparently stolen from an NSA hacking team seems to show the risks that result when the agency chooses offense over defense: Its secret hacking tools can fall into unknown hands.
On Wednesday, networking equipment firms Cisco and Fortinet warned customers about vulnerabilities revealed in data posted to the web days earlier by an anonymous group calling itself Shadow Brokers. The group claimed it obtained the data by hacking of an elite espionage team known as Equation Group and linked to the NSA. Shadow Brokers described its haul as a cache of encrypted “cyberweapons” that it would auction to the highest bidder. The data dump also contained an unencrypted sample with 300 megabytes of information including hacking software—known as “exploits”—designed to target networking appliances from Cisco, Fortinet, Juniper and TopSec.1
Based on Fortinet and Cisco’s urgent warnings in response to the exploits’ leak, it appears that some of those exploits had in fact been secret zero-day flaws. That raises the likelihood that the data was in fact stolen from NSA hackers—a view increasingly held by security experts analyzing the data.
More broadly, it also raises new questions about the NSA practice of keeping zero days secret rather than reporting them to affected companies. “There’s always that delicate balance: how do they accomplish their mission, hack their adversaries, and still protect the rest of us?” asks Jeremiah Grossman, a prolific web security researcher and chief of security strategy at the firm SentinelOne. “The longer you haven’t reported it, the higher the likelihood it will eventually leak.”
Though the stolen cache of data contained dozens of exploits, many matching previously known NSA hacking techniques referred to in documents leaked by Edward Snowden, Cisco has only warned customers about two of them, and issued a patch for the more serious of the two that would allow attackers in some circumstances to take control of its network security appliances. Fortinet warned customers that another of those leaked exploits affected versions of its security equipment sold before 2012, and recommended they update their software.
A Cisco spokesperson confirmed that the NSA hadn’t previously reported the vulnerability the company is now patching. Given that the data stolen by Shadow Brokers appears to be three years old, that could mean the NSA may have used the hacking technique in secret for years—and possibly allowed it to fall into the hands of its adversaries for just as long.
https://www.newscientist.com/articl...uards-to-stalk-the-internet-fighting-hackers/The Grand Cyber Challenge at the Black Hat cybersecurity conference in Las Vegas pitted artificial intelligences against each other, while their human creators sat back and watched. Fighting for a $4 million prize pot from the US Defense Advanced Research Projects Agency (DARPA), each AI tried to hack its opponents’ computer systems. They sought weak spots and figured out how to exploit them while defending their own computers.
The sophistication of the artificial hackers impressed many of those present. “This really caught me by surprise,” says Matt Devost of cybersecurity firm FusionX in Washington DC. It could transform the security scene in the next 10 years, he says.
The aim of the competition was to encourage the development of automated systems that can defend the internet against hackers. The winner, called Mayhem, was created by ForAllSecure in Pittsburgh, Pennsylvania. It’s the first time this kind of software has been shown to work, says the firm’s CEO David Brumley, who is also a cybersecurity researcher at Carnegie Mellon University.
The world of connected devices is becoming too complex for humans to defend on their own. So people like Brumley are developing tools that scan the internet for vulnerable devices and assist in securing them.
“You can make autonomous defence entities,” says Devost. “You might unleash one of these and its sole job is just roving around, probing your networks, finding vulnerabilities and patching them.”
ForAllSecure has started probing the Linux operating system, which is used by many of the computers that run the internet. The firm plans to release its software online and have it score the security of the systems it encounters. “The turning point is that we can now start inspecting every piece of software autonomously,” says Brumley.
The idea is to give consumers an idea of how safe a device is before buying it, letting them avoid a baby monitor that is found to be vulnerable to hackers, for example. “All these devices have not been looked at in depth,” he says. “If you go to Amazon and buy a router, there’s a huge chance that it has major vulnerabilities.”
But there’s a flip side. “You now also have the potential for creating autonomous attackers,” says Devost. “Launch one of these and you can automate something like the 2014 Sony hack.”
Devost is not the only one with concerns. Shortly after the Las Vegas competition, digital-rights group the Electronic Frontier Foundation (EFF) in San Francisco published an article on its website praising DARPA’s initiative, but calling for researchers to come together to discuss how to keep such systems from going rogue and doing catastrophic damage.
Software like Mayhem could be used to take control of connected devices in far greater numbers than human hackers could by themselves, opening up new kinds of attack. By hijacking smart thermostats, for example, cybercriminals could hold electricity providers to ransom by threatening to crank up the air conditioning and crash the grid.
The EFF wants researchers to work through the risks of building software that can probe and attack on its own. The issues are similar to those faced when working with highly infectious diseases. Just as modifying and studying the H5N1 flu virus in a lab lets us prepare for an epidemic, for example, it also opens the door for that research to be used to spread disease.
In a talk at Black Hat, Devost joked that the competition heralded the launch of Skynet, the malevolent AI in the Terminator films. “Everyone laughed,” he says. “The humans were applauding their own demise!”
https://www.newscientist.com/articl...tailor-clickbait-to-you-for-phishing-attacks/Careful of that clickbait. Phishing, where cybercriminals try to trick people into clicking links to malware or sites that steal your personal information, is common on social networks like Twitter. Now a machine learning system that reads our past tweets to craft personalised traps could make clicking links that show up in your feed even riskier.
Crafting a successful phishing campaign isn’t easy. Throw garbage at people and they probably won’t click – and Twitter will ban you. So some criminals take the trouble to tailor their phishing tweets to specific individuals by hand – known as spearphishing.
For example, @NatWest_HelpTC is a scam account that responds to anyone tweeting a customer service question at NatWest’s real Twitter account. The imposters direct users to a fake NatWest site in an attempt to harvest bank login details. A NatWest spokesperson told New Scientist that attacks like this have plagued them – and other companies – for a while now.
Ehkäpä samalla tavoin tarvittaisiin AI "uhreja", eli ei tekoälyä vaan tekohölmöyttä teeskentelemään vedätettävää ihmistä ja tuhlaamaan näiden huijareiden ja bottien aikaa ja resursseja.

http://www.spacewar.com/reports/Secret_data_leak_hits_French_submarine_maker_report_999.htmlFrench defence contractor DCNS has been hit by a massive leak of secret data on its submarines likely to alarm India, Malaysia and Chile which use the boats, The Australian newspaper reported Wednesday.
The 22,400 leaked pages, which the daily said it had seen, detail the combat capability of the Scorpene-class DCNS submarine designed for the Indian navy, variants of which are used by Malaysia and Chile.
Brazil is also due to deploy the vessels from 2018.
Australia in April awarded DCNS an Aus$50 billion (US$38 billion) contract to design and build its next generation of submarines.
Prime Minister Malcolm Turnbull sought to play down the impact of the leak, saying in Canberra that while it was "of concern", the Scorpene was a different model to the subs Australia is buying.
"The submarine we are building or will be building with the French is called the Barracuda, quite, completely different submarine to the Scorpene they are building for India," he told Channel Seven.
"We have the highest security protections on all of our defence information, whether it is in partnership with other countries or entirely within Australia."
The leaked documents were marked "Restricted Scorpene India" and gave the combat capabilities of India's new submarine fleet, The Australian said.
They also included thousands of pages on the submarine sensors and thousands more on its communication and navigation systems as well as nearly 500 pages on the torpedo launch system alone.
Indian Defence Minister Manohar Parrikar ordered a probe into the newspaper report, saying the documents could have been obtained through hacking.
"I have asked the navy chief to investigate the matter and find what has been leaked and how much of it is about us," Parrikar told reporters in India.
"What I understand is there is a hacking," he said without giving details.
DCNS told AFP it was aware of the articles published in the Australian press and "national security authorities" had launched an inquiry into the matter, without giving details.
"This inquiry will determine the precise nature of the documents which have been leaked, the potential damage to our customers as well as those responsible."
The Australian said DCNS implied that the leak may have come from India rather than France.
The daily, however, said the data was thought to have been removed from France in 2011 by a former French naval officer who at the time was a subcontractor for DCNS.
The data is believed to have passed through firms in Southeast Asia before eventually being mailed to a company in Australia, the newspaper said.
Australian Defence Industry Minister Christopher Pyne said in a statement the leak "has no bearing on the Australian government's future submarine programme".
Pyne said the programme "operates under stringent security requirements that govern the manner in which all information and technical data is managed now and into the future".
Australia awarded its submarine contract to DCNS but the secret combat system for the 12 Shortfin Barracudas is being supplied by the United States.
The submarines are a scaled-down conventionally powered version of France's 4,700-tonne Barracuda.
http://www.theregister.co.uk/2016/0...o_sweet32_captures_collisions_in_old_ciphers/Researchers with France's INRIA are warning that 64-bit ciphers – which endure in TLS configurations and OpenVPN – need to go for the walk behind the shed.
The research institute's Karthikeyan Bhargavan and Gaëtan Leurent have demonstrated that a man-in-the-middle on a long-lived encrypted session can gather enough data for a “birthday attack” on Blowfish and triple DES encryption. They dubbed the attack “Sweet32”.
Sophos' Paul Ducklin has a handy explanation of why it matters here.
The trick to Sweet32, the Duck writes, is the attackers worked out that with a big enough traffic sample, any repeated crypto block gives them a start towards breaking the encryption – and collisions are manageably common with a 64-bit block cipher like Blowfish or Triple-DES.
They call it a “birthday attack” because it works on a similar principle to what's known as the “birthday paradox” – the counter-intuitive statistic that with 23 random people in a room, there's a 50 per cent chance that two of them will share a birthday.
In the case of Sweet32 (the 32 being 50 per cent of the 64 bits in a cipher), the “magic number” is pretty big: the authors write that 785 GB of captured traffic will, under the right conditions, yield up the encrypted HTTP cookie and let them decrypt Blowfish- or Triple-DES-encrypted traffic.
If you do it right, and here begins the TL;dr part.
To launch the attack, you need to:
Decryption is still the hard part: the researchers note that it's far from an instant process:
- Get a victim to visit a malicious site (site A) – one that they have to log into. The victim's login sets an HTTP cookie the browser uses for future requests;
- Pass the victim on to Site B, which generates millions of JavaScript requests to Site A, using the login cookie given to the victim;
- Keep the connection alive long enough to store 785 GB of encrypted data blocks, and look for a collision;
- Decrypt the login cookie.
On Firefox Developer Edition 47.0a2, with a few dozen workers running in parallel, we can send up to 2,000 requests per second in a single TLS connection. In our experiment, we were lucky to detect the first collision after only 25 minutes (220.1 requests), and we verified that the collision revealed [the plaintext we were after …The full attack should require 236.6 blocks (785 GB) to recover a two-block cookie, which should take 38 hours in our setting. Experimentally, we have recovered a two-block cookie from an HTTPS trace of only 610 GB, captured in 30.5 hours.
As they note, however, long-lived encrypted connections exist in at least one real-world setting: VPN sessions.
“Our attacks impact a majority of OpenVPN connections and an estimated 0.6% of HTTPS connections to popular websites. We expect that our attacks also impact a number of SSH and IPsec connections, but we do not have concrete measurements for these protocols” (emphasis added).
For users, that means switching from 64-bit ciphers to 128-bit ciphers; or if you can't get the server to switch, set up your client to force frequent re-keying.
Browser makers, TLS library authors and OpenVPN have been notified and are working on patches.

http://www.theregister.co.uk/2016/0...ty_after_stealing_29_million_us_credit_cards/The son of a Russian member of parliament has been found guilty of stealing and selling millions of US credit card numbers using point of sales malware.
Roman Seleznev, 32, is the son of ultra-nationalist Liberal Democratic Party MP Valery Seleznev. He was arrested in 2014 while attempting to board a plane in the Maldives, sparking anger from Russian authorities.
Seleznev said at the time the arrest was a "monstrous lie and a provocative act".
Roman Seleznev was convicted in a Washington court on Thursday, on 10 counts of wire fraud, nine of obtaining information from a protected computer, nine of possession of 15 unauthorised devices, eight of intentional damage to a protected computer, and two of aggravated identity theft.
He faces a minimum of four years and a maximum of 34 years in prison when he is sentenced 2 December.
Seleznev, who used the handle Track2, scanned for vulnerable retailers across Washington and infected point of sales terminals with malware, prosecutors said.
He stole some 2.9 million credit cards, according to prosecutors, wreaking some US$169 million in damages across 3700 financial institutions.
Prosecutors said his laptop contained some 1.7 million stolen credit card numbers
http://arstechnica.co.uk/security/2...o-keys-by-corrupting-data-in-computer-memory/The world has seen the most unsettling attack yet resulting from the so-called Rowhammer exploit, which flips individual bits in computer memory. It's a technique that's so surgical and controlled that it allows one machine to effectively steal the cryptographic keys of another machine hosted in the same cloud environment
Until now, Rowhammer has been a somewhat clumsy and unpredictable attack tool because it was hard to control exactly where data-corrupting bit flips happened. While previous research demonstrated that it could be used to elevate user privileges and break security sandboxes, most people studying Rowhammer said there was little immediate danger of it being exploited maliciously to hijack the security of computers that use vulnerable chips. The odds of crucial data being stored in a susceptible memory location made such hacks largely a matter of chance that was stacked against the attacker. In effect, Rowhammer was more a glitch than an exploit.
Now, computer scientists have developed a significantly more refined Rowhammer technique they call Flip Feng Shui. It manipulates deduplication operations that many cloud hosts use to save memory resources by sharing identical chunks of data used by two or more virtual machines. Just as traditional Feng Shui aims to create alignment or harmony in a home or office, Flip Feng Shui can massage physical memory in a way that causes crypto keys and other sensitive data to be stored in locations known to be susceptible to Rowhammer.
http://www.theregister.co.uk/2016/09/06/obama_says_usa_has_worlds_biggest_and_best_cyber_arsenal/United States president Barack Obama says the nation he leads has the world's foremost digital arsenal.
Speaking at a press conference after meeting Russian president Vladimir Putin at the G20 summit in China, Obama said “We have had problems with cyber intrusions from Russia in the past, from other countries in the past.”
He went on to say “we are moving into a new area where a number of countries have significant capacities. And frankly we have more capacity than any other country, both offensively and defensively.” Which rather contradicts recent analysis of the USA's zero-day trove as rather small. Or means other nations have tiny zero-day hoards.
Back to Obama's speech, which continued "But our goal is not, in the cyber arena, to suddenly duplicate a cycle of escalation that we saw when it comes to other arms races in the past,” Obama added. Instead, he hopes “to start instituting some norms so that everyone is acting responsibly.”
He favours that approach because “We are going to have enough problems in cyberspace with non-state actors who are engaging in theft and using the internet for all sorts of illicit practices.” The president therefore said “protecting our critical infrastructure and making sure that our financial systems are sound” are going to be priorities.
“What we cannot do is have a situation in which this becomes the wild, wild west where countries that have significant cyber capacity start engaging in competition, unhealthy competition or conflict, through these means, when wisely we put in place some norms when it comes to using other weapons.”
Obama said such norms have “been a topic of convo with president Putin as it has been with other countries,” then concluded by saying “We have started to get some willingness with a lot of countries around the world to adopt these norms but we have got to make sure we are observing them.”
One example of Obama's hoped for world cyber order could be the US/China no hack pact signed in 2015, but quickly called into question. Other no hack pacts cover Germany and China, China and the UK and the USA and Australia.
Critics say such pacts look great on paper, but exempt businesses and therefore lack teeth because China operates a great many state-owned enterprises with security functions. The USA even runs a venture capital company, In-Q-Tel, established by the US Central Intelligence Agency (CIA) specifically to to find useful tech for the intelligence community.
Absent any detail from Obama on the new world cyber order he's imagined, it looks like there are loopholes a-plenty allowing online operations to carry on even while pacts apply. ®
