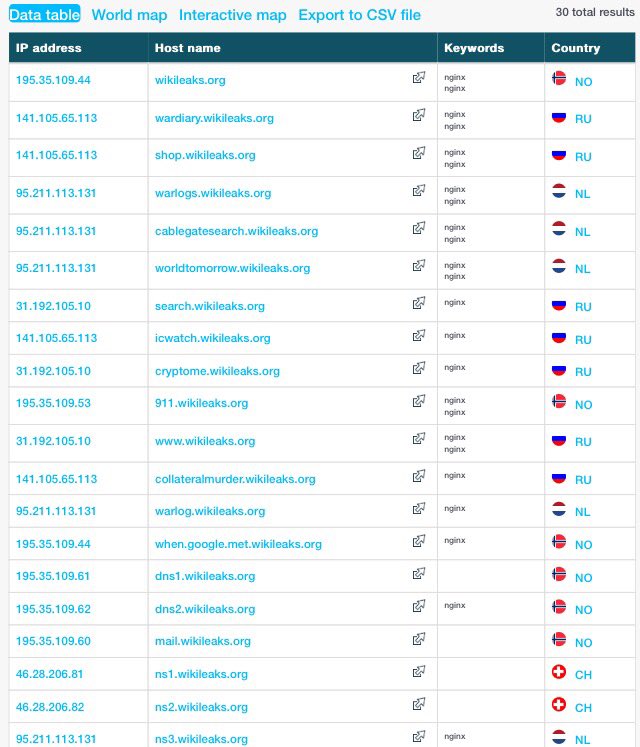
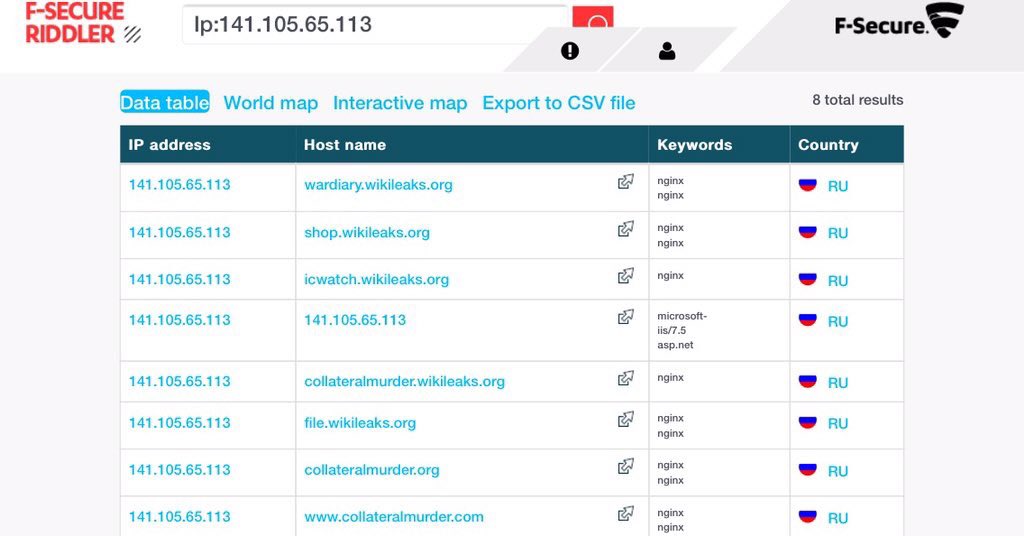
http://www.theregister.co.uk/2016/10/21/britain_investing_cyber_warfare_offensive_capability/Britain is splurging £265m on military cyber security – and that includes offensive capabilities, according to Defence Secretary Sir Michael Fallon.
Speaking at the Royal United Services Institute yesterday, Sir Michael said the investment into the Cyber Vulnerability Investigations programme would “help us protect against these threats”.
“The average cost of the most severe online security breaches for bigger companies starts at almost £1.5m, up £600,000 from 2014,” said Sir Michael, adding: “It’s only a matter of time before we have to deal with a major attack on UK interests.”
So far Britain has managed to avoid the sort of targeted large-scale hacks that have seen big US tech companies such as Yahoo! see 500 million user accounts compromised, or the Target hack which saw millions of credit card and debit card details as well as names and addresses leaked into the hands of cyber-criminals.
It seems, from Sir Michael's speech, that Blighty is gearing up to proactively attack any cyber-villains with designs on British internet infrastructure.
Lauding various government security initiatives, including the National Cyber Security Centre in Victoria, London, the Defence Secretary said: “This cannot just be about our defence. It must be about our offence too. It is important that our adversaries know there is a price to pay if they use cyber weapons against us, and that we have the capability to project power in cyberspace as elsewhere.”
Given that most large-scale hacks tend to be backed by states such as China and Russia, it seems that Sir Michael's speech is a public shot across their bows, warning them not to target Blighty – while simultaneously urging NATO to treat the Article 5 collective defence provisions as applying to cyberspace.
Originally, Article 5 of the Washington Treaty, which founded NATO, was intended to ensure that any westward expansion of the Soviet Union would trigger World War Three by dragging Britain and America in, thereby keeping the Soviets and the Eastern Bloc's expansionist aims firmly under control.
It is unlikely that many countries would take Article 5 seriously in the context of cyberspace, given that many NATO member states effectively ignore the treaty requirement for them to spend two per cent of GDP on military spending. ®
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
Hei,
Havaintoja omasta mikrokosmoksesta:
- Minulla on kaksi Axis IP kameraa, jotka on kytketty jo pari vuotta sitten DynDNS palveluun ja myös rekisteröity valmistajan sivuille. Suosittu kamera käsittääkseni globaalisti.
- Avasin tuossa huvikseni kamerat ja kummankin modulin on valmistanut Kiinalainen XiongMai
- Kameroissa on default asetuksena uPNP päällä, eli jos tuota ei muuta, kamera avaa portin reitittimeen http:tä ja Telnettiä varten
- Kolmisen viikkoa sitten omaan palomuuriin alkoi tulla jatkuvasti suuri määrä Telnet ja SSL yhteydenavausyrityksiä. About 3000 päivässä (!!!). Niin poikkeuksellisen suuri määrä verrattuna aikaisempaan, että se alkoi kiinnittää huomiotani ja aloin seurata niitä.
- Parisen viikkoa sitten SSL yritykset eivät olleet enää vain portissa 443 vaan portteja skannattiin kaikista numeroista XX443. XX meni järjestelmällisesti 1…65.
- 90% noista yhteyksistä tuli näistä maista: Venäjä, Kiina, Vietnam ja Brasilia
- Torstaina yhteydenavausyritykset ovat palautuneet minimiin
Yhden ihmisen kokemuksesta ei saisi tehdä globaalia johtopäätöstä, mutta kyllä tässä on vähän sellainen fiilis, että joku yritti saada noita kameroita alustaksi itselleen.
Harva tietää, mitä sen oman yksinkertaisen WiFi reitittimen takana kulkee ja vielä harvemmalla on innostusta tai mahdollisuutta asentaa kotiin järeämpää palomuuria, jossa on myös tarvittavat analysointityökalut.
Ei minulla muuta tähän asiaan. Ehkä olen vainoharhainen.
Simpauttaja
Havaintoja omasta mikrokosmoksesta:
- Minulla on kaksi Axis IP kameraa, jotka on kytketty jo pari vuotta sitten DynDNS palveluun ja myös rekisteröity valmistajan sivuille. Suosittu kamera käsittääkseni globaalisti.
- Avasin tuossa huvikseni kamerat ja kummankin modulin on valmistanut Kiinalainen XiongMai
- Kameroissa on default asetuksena uPNP päällä, eli jos tuota ei muuta, kamera avaa portin reitittimeen http:tä ja Telnettiä varten
- Kolmisen viikkoa sitten omaan palomuuriin alkoi tulla jatkuvasti suuri määrä Telnet ja SSL yhteydenavausyrityksiä. About 3000 päivässä (!!!). Niin poikkeuksellisen suuri määrä verrattuna aikaisempaan, että se alkoi kiinnittää huomiotani ja aloin seurata niitä.
- Parisen viikkoa sitten SSL yritykset eivät olleet enää vain portissa 443 vaan portteja skannattiin kaikista numeroista XX443. XX meni järjestelmällisesti 1…65.
- 90% noista yhteyksistä tuli näistä maista: Venäjä, Kiina, Vietnam ja Brasilia
- Torstaina yhteydenavausyritykset ovat palautuneet minimiin
Yhden ihmisen kokemuksesta ei saisi tehdä globaalia johtopäätöstä, mutta kyllä tässä on vähän sellainen fiilis, että joku yritti saada noita kameroita alustaksi itselleen.
Harva tietää, mitä sen oman yksinkertaisen WiFi reitittimen takana kulkee ja vielä harvemmalla on innostusta tai mahdollisuutta asentaa kotiin järeämpää palomuuria, jossa on myös tarvittavat analysointityökalut.
Ei minulla muuta tähän asiaan. Ehkä olen vainoharhainen.
Simpauttaja
KorpiSISSI
Kenraali
HUOM! Hybridistä luentopäivä
https://theintercept.com/2016/10/23/endace-mass-surveillance-gchq-governments/It was a powerful piece of technology created for an important customer. The Medusa system, named after the mythical Greek monster with snakes instead of hair, had one main purpose: to vacuum up vast quantities of internet data at an astonishing speed.
The technology was designed by Endace, a little-known New Zealand company. And the important customer was the British electronic eavesdropping agency, Government Communications Headquarters, or GCHQ.
Dozens of internal documents and emails from Endace, obtained by The Intercept and reported in cooperation with Television New Zealand, reveal the firm’s key role helping governments across the world harvest vast amounts of information on people’s private emails, online chats, social media conversations, and internet browsing histories.
The leaked files, which were provided by a source through SecureDrop, show that Endace listed a Moroccan security agency implicated in torture as one of its customers. They also indicate that the company sold its surveillance gear to more than half a dozen other government agencies, including in the United States, Israel, Denmark, Australia, Canada, Spain, and India.
Some of Endace’s largest sales in recent years, however, were to the United Kingdom’s GCHQ, which purchased a variety of “data acquisition” systems and “probes” that it used to covertly monitor internet traffic.
Documents from the National Security Agency whistleblower Edward Snowden, previously disclosed by The Intercept, have shown how GCHQ dramatically expanded its online surveillance between 2009 and 2012. The newly obtained Endace documents add to those revelations, shining light for the first time on the vital role played by the private sector in enabling the spying.
https://www.wired.com/2016/10/inside-cyberattack-shocked-us-government/The Office of Personnel Management repels 10 million attempted digital intrusions per month—mostly the kinds of port scans and phishing attacks that plague every large-scale Internet presence—so it wasn’t too abnormal to discover that something had gotten lucky and slipped through the agency’s defenses. In March 2014, for example, OPM had detected a breach in which blueprints for its network’s architecture were siphoned away. But in this case, the engineers noticed two unusually frightening details. First, opmsecurity.org had been registered on April 25, 2014, which meant the malware had probably been on OPM’s network for almost a year. Even worse, the domain’s owner was listed as “Steve Rogers”—the scrawny patriot who, according to Marvel Comics lore, used a vial of Super-Soldier Serum to transform himself into Captain America, a member of the Avengers.
Registering sites in Avengers-themed names is a trademark of a shadowy hacker group believed to have orchestrated some of the most devastating attacks in recent memory. Among them was the infiltration of health insurer Anthem, which resulted in the theft of personal data belonging to nearly 80 million Americans. And though diplomatic sensitivities make US officials reluctant to point fingers, a wealth of evidence ranging from IP addresses to telltale email accounts indicates that these hackers are tied to China, whose military allegedly has a 100,000-strong cyberespionage division.
Once Captain America’s name popped up, there could be little doubt that the Office of Personnel Management had been hit by an advanced persistent threat (APT)—security-speak for a well-financed, often state-sponsored team of hackers. APTs like China’s Unit 61398 have no interest in run-of-the-mill criminal activities such as selling pilfered Social Security numbers on the black market; they exist solely to accumulate sensitive data that will advance their bosses’ political, economic, and military objectives. “Everyone can always say, ‘Oh, yeah, the Pentagon is always going to be a target, the NSA is always going to be a target,’” says Michael Daniel, the cybersecurity coordinator at the White House, who was apprised of the crisis early on. “But now you had the Office of Personnel Management as a target?”
http://www.theregister.co.uk/2016/1...ebcams_over_mirai_botnet_infection_ddos_woes/Chinese electronics firm Hangzhou Xiongmai is set to recall swathes of webcams after they were compromised by the Mirai botnet.
Mirai exploits the low security standards of internet-connected devices, from routers to webcams, and after enslaving them with malware uses their network connections to launch DDoS attacks, such as that hobbling Dyn's DNS services last week.
Among the many devices infected by Mirai were products sold by Hangzhou Xiongmai, although the company disputes claims that its products comprised the majority of those involved in the attack.
The firm's devices do not force the end-user to change the default password, and in some cases does not allow the administration password to be changed at all, leaving many thousands open to rogue access.
In a statement, the company announced that it would now be recalling some of the products it had sold in the US, as well as strengthen their password functions and issue a patch for earlier products.
See more at: Dyn DDoS Work of Script Kiddies, Not Politically Motivated Hackers https://wp.me/p3AjUX-vChNew research on the source of Friday’s DDoS attack against DNS provider Dyn indicates that script kiddies are likely responsible, rather than a politically motivated actor. Researchers at Flashpoint dismissed numerous claims of responsibility that separately linked the attack to the Russian government, WikiLeaks or the New World Hackers group. Instead, the threat intelligence company said with “moderate confidence” that the attacks are linked to the Hackforums community. Hackforums is an English-speaking hacking forum and the place where the source code for the Mirai malware was publicly released by a hacker known as Anna-Senpai.
Flashpoint hinges its conclusion on a number of factors, starting with public release of the Mirai source code. Mirai scans the Internet for IoT devices such as those used in the attack on Dyn, Krebs on Security and French webhost OVH. The malware uses 60 known weak and default credentials on the IP-enabled cameras, DVRs and home networking gear to access the devices before corralling them into giant botnets used to DDoS targets.
Since the source code was made public, the number of bots compromised by the malware has more than doubled, Level 3 Communications, a Colorado telco and ISP, said. “The personalities involved in this community are known for creating and using commercial DDoS tools called booters or stressers. The hackers offer these services online for pay, essentially operating a DDoS-for-hire service,” said Allison Nixon director of security research at Flashpoint. “One of the few known personalities that have been associated with Mirai malware and botnets is known to frequent these forums. …The hackers that frequent this forum have been previously known to launch these types of attacks, though at a much smaller scale.”
Supporting its claim, Flashpoint said the infrastructure used in Friday’s DDoS attack was also used to target a well-known and unnamed video game company. “While there does not appear to have been any disruption of service, the targeting of a video game company is less indicative of hacktivists, state-actors, or social justice communities, and aligns more with the hackers that frequent online hacking forums,” Nixon said, adding that the script kiddies likely involved in the attack are less motivated by financial or political gain, and more by notoriety, or to “cause disruption and chaos for sport,” Nixon said.
Nixon added that skilled criminals or nation-state groups are less likely to launch DDoS attacks without clear financial, political or strategic gains. “Participants in the Hackforums community have been known to launch DDoS attacks against video game companies to show off their credentials as hackers of skill, or to troll and gain attention by causing disruption to popular services,” Nixon said.
http://www.theregister.co.uk/2016/10/27/schneider_plugs_gaping_industrial_control_security_flaw/A vulnerability in Schneider Electric’s industrial controller management software created a possible mechanism for hackers to plant malicious code on industrial networks.
Industrial cybersecurity firm Indegy discovered the recently resolved flaw in Schneider Electric’s flagship industrial controller management software, Unity Pro. “The vulnerability in Unity Pro allows any user to remotely execute code directly on any computer on which this product is installed, in debug privileges,” Indegy warned in an advisory.
In a statement issued to El Reg, Schneider Electric said the flaw had been addressed in the latest version of its software. The firm is pushing out an alert [pdf] to customers explaining how to guard against the threat, either through updates or by following its mitigating advice.
Schneider Electric has become aware of a vulnerability in the Unity PRO Software prior to V11.1. We issued a Security Notification that shares mitigation recommendations. This vulnerability is made possible when no application program has been loaded in the simulator, or when the application program loaded in the simulator is not password protected.
David Zahn, general manager at PAS, Inc, a provider of industrial control systems cybersecurity technology, added that further flaws along the lines of the one successfully resolved by Schneider are inevitable because industrial control technology was never designed with security in mind.
“It is good that cybersecurity companies are disclosing these vulnerabilities and following good ethical disclosure practices, but no one should be surprised that such vulnerabilities exist,” Zahn said. “This is tip of the iceberg stuff as most control systems in the field today were designed without cybersecurity as even a consideration.”
He added: “It is common to see control systems that are 15, 20, and 25 years old in a production environment. They rely on air gapping, complexity, and other factors to protect them, but nothing specific to cybersecurity was inherently built within them."
The flaw was discovered six months ago before; Schneider Electric was privately notified to allow it to investigate and remedy the problem. Indegy went public with its research this week at the 2016 Industrial Control Systems Cyber Security Conference at Atlanta, USA.
Mike Ahmadi, global director of critical systems security at Synopsys, added: "Security issues in control systems are widespread and continue to grow in numbers as researchers focus on uncovering them.”
Ei ole ensimmäinen kerta kun vastavirusta taikka vastamatoa on tarjottu lääkkeeksi bottiongelmaan. Ei ole varmaan viimeinenkään kerta. Silti vieläkään ei ole kunnon lakia siitä milloin sen saa tehdä, sillä tekemällä tämän levittäjä altistuu rikollisen asteelle. Laissa on useita samanlaisia aukkoja. Mutta asiakkaan allekirjoittama get-out-from-jail läpyskä on auttanut hillitsemaan lakitupa juttuja.
http://www.theregister.co.uk/2016/1...ot_could_silence_epic_mirai_ddos_attack_army/Security researcher Jerry Gamblin has created an anti-worm "nematode" that could help to patch vulnerable devices used in the massive Mirai distributed denial of service attack.
The nematode, a concept detailed by security man Dave Aitel [PDF], would fight back against the massive and highly dangerous inter-of-things-borne botnet used in highly disruptive attacks against major web infrastructure including DNS provider Dyn.
Some 100,000 Telnet-exposed-and-web-connected cameras, sensors and other devices are held to have downed Dyn.
Researcher Scott Tenaglia Friday found a stack buffer overflow vulnerability in the Mirai code which could be used to crash bots and shut down Mirai attacks.
Gamblin's (@JGamblin) worm goes further and can be used to break into woefully-insecure internet-of-things devices and change the default Telnet credentials within.
Doing so would lock Mirai and other malware users out of the devices, along with legitimate administrators.
"This is a purely academic research project intended to show a proof of concept anti-worm worm, or nematode, for the types of vulnerabilities exploited by Mirai," Gamblin says.
"The idea is to show that devices can be patched by a worm that deletes itself after changing the password to something device- specific or random.
"Such a tool could theoretically be used to reduce the attack surface."
Gamblin says it is only for closed research environments and warns users to test at their own risk.
Unleashing the nematode would breach computer crime laws in the US, UK, and Australia, and likely in many other countries where unauthorised use and modification of computer equipment is an offense.
It is not the first nematode. Researchers in 2004 unleashed the Welchia worm to combat the damage wrought from the Blaster worm, by breaking into infected devices and downloading and installing Microsoft patches before self-deleting.
A nematode was used in the same year to patch phpBB installations to counter the Santy malware.
These nematodes are not without problems. The Welchia worm caused headaches for IT managers while any anti-Mirai worm could disrupt inexperienced users who would be locked out of remote device access.
http://www.theregister.co.uk/2016/11/01/postmirai_hackforums_kills_off_ddos_rental/The success of the Mirai botnet was apparently a shiver looking for a spine to run up: HackForums has killed off its “server stress test” DDoS-for-hire section.
Site admin Jesse LaBrocca posted the decision last Friday (here for registered members of the site), saying “recent events” forced the decision.
Brian Krebs quotes LaBrocca's post as saying “I’m personally disappointed that this is the path I have to take in order to protect the community.
“I loathe having to censor material that could be beneficial to members. But I need to make sure that we continue to exist and given the recent events I think it’s more important that the section be permanently shut down.”
The code first emerged being passed around the forums, until it was leaked to GitHub at the end of September.
LaBrocca, who goes by the handle “Omniscient” on HackForums, is apparently displeased by events since Mirai emerged, complaining that “the few ruin it for the many”.
Before making the decision, LaBrocca had already warned that Mirai would bring about a backlash.
Krebs notes that pulling the Server Stress Test is going to burn a hole in HackForums' income, since banner ads in the section ran to as much as US$200 a week, with a $60 premium to make the ads sticky.
Viimeksi muokattu:
http://www.zdnet.com/article/uk-will-strike-back-if-it-comes-under-cyber-attack-says-government/"Our new strategy, underpinned by £1.9bn of support over five years and excellent partnerships with industry and academia, will allow us to take even greater steps to defend ourselves in cyberspace and to strike back when we are attacked," Philip Hammond, UK Chancellor of the Exchequer, is set to say in a speech in which he argues Britain "must now keep up with the scale and pace of the threats we face".
LULZ It's a never ending cycle. The flood will never stop.
https://wp.me/p3AjUX-vEZResearchers have thrown back the covers on more malware infecting IoT devices for the purposes of building a botnet that carries out DDoS attacks.
http://www.defenseone.com/news/2016...old-heres-best-guess-yet/132932/?oref=d-riverThe U.S. government likely retains an arsenal of just dozens of otherwise unknown computer vulnerabilities that can be used for spying or sabotage and adds fewer than 10 new vulnerabilities to that cache each year, according to a Columbia University analysis released today.
The analysis gives some context to the government’s largely opaque decision-making about whether to disclose exploitable glitches it discovers in commercial and industrial computer systems or to use them for intelligence operations.
Such previously unknown vulnerabilities have been at the root of numerous high-profile cyber operations, including the Stuxnet attack that seriously damaged Iranian nuclear reactors.
It comes as a group called the Shadow Brokers is releasing a trove of leaked National Security Agency hacking tools that includes a handful of the nonpublic vulnerabilities known as zero days—because they’re not known to the manufacturer, which has had zero days to offer a patch.
Titled “The U.S. Government and Zero-Day Vulnerabilities,” the report is based on six months of research by Jason Healey, senior research scholar at Columbia University’s School of International and Public Affairs, and a class of graduate students. Healey, who is a former director of infrastructure protection at the White House and has held numerous cyber defense positions in government and industry, previewed some of the report’s findings at the Black Hat cybersecurity conference in Las Vegas in August.
Government agencies currently submit zero days they discover to an interagency Vulnerability Equities Process headed by the National Security Council. The review examines questions such as how likely criminals and foreign adversaries are to discover the vulnerability and how much damage they could do if they did discover it, balancing that with what value the vulnerability might provide to U.S. intelligence agencies.
The review process launched in 2010 with NSA taking the lead. That responsibility was shifted to NSC in the wake of the former contractor Edward Snowden’s revelations in 2014 with a goal of giving a stronger voice to the Department of Homeland Security and other agencies more focused on cyber defense than offense.
The review process only applies to products made or widely used in the United States.
The government has been tight-lipped about how many vulnerabilities go through this review, though NSA said in 2015 that historically, it disclosed 91 percent of vulnerabilities to manufacturers and that a portion of the remaining 9 percent were discovered by manufacturers before the government completed its review.
The best takeaway from the Columbia report, according to the authors, is that the equities review process is not “hopelessly broken,” but “does appear to be in need of further strengthening.”
The authors recommend increasing transparency about reviews through annual or quarterly reports and formalizing the review process by executive order. They also recommend instituting annual or biennial re-examinations for zero days the government opted not to disclose but that still haven’t been discovered—in case they’ve become less valuable to U.S. intelligence agencies or it’s become more likely adversaries will use them against U.S. targets.
Agencies should also be barred from exploiting vulnerabilities before equity reviews are completed “to prevent agencies from bureaucratically delaying the process while they squeeze the orange dry,” the report states.
The report also criticizes the FBI’s decision to contract with an undisclosed firm to unlock the iPhone used by San Bernardino shooter Syed Farook.
The FBI reportedly paid the firm in the neighborhood of $1 million to unlock the phone, but the firm did not sell the vulnerability that made the unlocking possible to the bureau. The authors recommend closing that loophole, “so agencies cannot bypass the [review process] because of a nondisclosure agreement or other chicanery.”
The report also recommends including industry perspectives in the review process in some way, perhaps by including members who are retired from both government and industry but retain government clearances
https://www.theguardian.com/world/2...w-sparks-fresh-censorship-and-espionage-fearsChina adopted a controversial cybersecurity law on Monday that it said would tackle growing threats such as hacking and terrorism but has triggered concern from foreign business and rights groups.
The legislation, passed by China’s largely rubber-stamp parliament and set to come into effect in June 2017, was an “objective need” of China as a major internet power, a parliamentary official said.
Overseas critics argue it threatens to shut out foreign technology companies and includes contentious requirements for security reviews and for data to be stored on servers in China.
https://www.theguardian.com/technol...-strategy-stop-children-cybercrime-governmentBritain’s cybercrime tsar will formally ask the government to set up a programme based on the controversial Prevent strategy to stop children as young as 12 becoming involved in sophisticated computer offences, the Guardian has learned.
Dr Jamie Saunders said training was needed to help spot teenagers at risk as many young internet users experiment with hacking or other cyber offences without realising that what they are doing is a crime.
Saunders, the director of the national cyber crime unit at the National Crime Agency (NCA), said he was proposing the scheme, known internally as Cyber Prevent, to ministers. It is modelled in part on Prevent, the official counter-radicalisation programme that has been dogged by controversy.
http://www.bleepingcomputer.com/new...le-rootkit-that-targets-industrial-equipment/Two researchers presenting at the Black Hat Europe security conference in London revealed a method of infecting industrial equipment with an undetectable rootkit component that can wreak havoc and disrupt the normal operations of critical infrastructure all over the world.
The attack targets PLCs (Programmable Logic Controllers), devices that sit between normal computers that run industrial monitoring software and the actual industrial equipment, such as motors, valves, sensors, breakers, alarms, and others.
Jos tietoturvasta on kiinnostunut, niin kannattaa katse ohjata linuxiin ja erityisesti distroon:
http://www.theregister.co.uk/2016/11/14/its_2016_and_a_ping_of_death_can_still_be_a_thing/A code artefact in a number of popular firewalls means they can be crashed by a mere crafted ping.
The low-rate “Ping of death” attack, dubbed BlackNurse, affects firewalls from Cisco, SonicWall, Zyxel, and possibly Palo Alto.
Since we don't imagine Switchzilla has started giving away the version of IOS running in its ASA firewalls, Vulture South suspects it arises from a popular open source library. Which means other vulnerable devices could be out there.
Unlike the old-fashioned ping-flood, the attack in question uses ICMP “Type 3, Code 3” (destination unreachable, port unreachable) packets.
In the normal course of events, a host would receive that packet in response to a message it had initiated – but of course, it's trivial to craft that packet and send it to a target.
In devices susceptible to BlackNurse, the operating system gets indigestion trying to process even a relatively low rate of these messages – in the original report from Denmark's TF-CSIRT, gigabit-capable routers could be borked by just 18 Mbps of BlackNurse traffic on their WAN interfaces.
The good news is that in most cases, the attack is trivial to block, by dropping ICMP traffic. For example, the TF-CSIRT report includes suitable Snort rules, while Palo Alto says users of PAN-OS-based firewalls can block all ICMP traffic, or write a more sophisticated BlackNurse-specific DoS filter.
Forensics company Netresec has more detail on BlackNurse here, and has test information here.
In some environments, a blanket ban on ICMP is problematic. As Cisco notes, losing ICMP MTU path discovery can upset IPSec and/or PPTP sessions.
http://www.nytimes.com/2016/11/16/us/politics/china-phones-software-security.html?_r=1WASHINGTON — For about $50, you can get a smartphone with a high-definition display, fast data service and, according to security contractors, a secret feature: a backdoor that sends all your text messages to China every 72 hours.
Security contractors recently discovered preinstalled software in some Android phones that monitors where users go, whom they talk to and what they write in text messages. The American authorities say it is not clear whether this represents secretive data mining for advertising purposes or a Chinese government effort to collect intelligence.
International customers and users of disposable or prepaid phones are the people most affected by the software. But the scope is unclear. The Chinese company that wrote the software, Shanghai Adups Technology Company, says its code runs on more than 700 million phones, cars and other smart devices. One American phone manufacturer, BLU Products, said that 120,000 of its phones had been affected and that it had updated the software to eliminate the feature.
Kryptowire, the security firm that discovered the vulnerability, said the Adups software transmitted the full contents of text messages, contact lists, call logs, location information and other data to a Chinese server. The code comes preinstalled on phones and the surveillance is not disclosed to users, said Tom Karygiannis, a vice president of Kryptowire, which is based in Fairfax, Va. “Even if you wanted to, you wouldn’t have known about it,” he said.
Security experts frequently discover vulnerabilities in consumer electronics, but this case is exceptional. It was not a bug. Rather, Adups intentionally designed the software to help a Chinese phone manufacturer monitor user behavior, according to a document that Adups provided to explain the problem to BLU executives. That version of the software was not intended for American phones, the company said.
“This is a private company that made a mistake,” said Lily Lim, a lawyer in Palo Alto, Calif., who represents Adups.