Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
https://www.defenseone.com/technolo...gressive-offensive-cyber/157270/?oref=d-riverIn the latest signal NATO is adopting a tougher posture against cyber and electronic attacks, Secretary General Jens Stoltenberg this week said that the defensive alliance will not remain purely defensive.
Stoltenberg told attendees at the Cyber Defence Pledge conference in London, “We are not limited to respond in cyberspace when we are attacked in cyberspace.”
NATO members have already “agreed to integrate national cyber capabilities or offensive cyber into Alliance operations and missions,” he said. But the parameters of a NATO response to cyber attacks remains undefined. In 2015, Stoltenberg said that a cyber attack against one member nation could trigger an Article 5 collective response by all members. Yet only once has a collective response ever been invoked, at the request of the United States following the attacks of September 11, 2001. NATO is a defensive organization, so what an offensive cyber posture looks like remains something of a mystery. An Article 5 response can take many different forms.
That’s the strength of the article, according to NATO Deputy General Secretary Rose Gottmoeller. However, while an Article 5 response can be unpredictable, it must be coordinated, which can be tricky with many different partners in possession of many different capabilities.
At an event in May, Gottmoeller said NATO was in the processes of establishing a new innovation board to “bring together all of the parts of and pieces of NATO that have to wrestle with these new technologies to really try to get a flow of information. Many of you having served in any international institution or government, you know how things can get stove-piped. So we are resolved to break down those stove-pipes, particularly where innovation is concerned,” she said.
NATO is building a cyber command that is scheduled to be fully operational in 2023 and will coordinate and conduct all offensive cyber operations. Until then, whatever NATO does offensively, it will rely heavily on the United States and the discretion of U.S. commanders, according to Sophie Arts, program coordinator for security and defense at the German Marshall Fund, who explains in this December report.
“Yesterday’s remarks indicate that NATO’s leadership is thinking more seriously about buttressing the alliance’s deterrence posture in cyberspace and address threats that fall under the threshold of an Article 5 violation,” she told Defense One.
“This tracks recent shifts in strategy adopted by several NATO allies, including the United States, which integrate offensive cyber operations as an important tool to proactively address growing instances of cyber interference from hostile actors.”
But Arts points out there is no field manual for coordinating cyber offensive operations among individual allies, including big players in cyber like Estonia, the U.K. and the United States, who keep command and control over their assets.
In 2017, Gregory Edwards, then director of infrastructure services at NATO’s communication and information agency laid out what that might look like. “You could make a case-by-case decision” about responding to attacks, he said. “You need to have a policy that says, ‘if our operation is disturbed, we will take a specific action.’ The action will be listed. It will be listed what things the commander is allowed to do in that regard. It will be a specific action.”
At an April meeting of NATO policy planners in Washington D.C., Kiron Kanina Skinner, director of Policy Planning at the U.S. State Department said that NATO policy planners had spent most of their time during the meeting discussing how to coordinate cyber effects and policy.
The issue was competing against traditional NATO concerns and even topics like the Russian military buildup on the border of Eastern Europe. “Today, we didn’t talk about the Eastern flank; we talked about cybersecurity,” she said.
Osasto 31
Kapteeni
Linkki: https://www.nytimes.com/2019/05/25/us/nsa-hacking-tool-baltimore.html
In Baltimore and Beyond, a Stolen N.S.A. Tool Wreaks Havoc
For nearly three weeks, Baltimore has struggled with a cyberattack by digital extortionists that has frozen thousands of computers, shut down email and disrupted real estate sales, water bills, health alerts and many other services.
But here is what frustrated city employees and residents do not know: A key component of the malware that cybercriminals used in the attack was developed at taxpayer expense a short drive down the Baltimore-Washington Parkway at the National Security Agency, according to security experts briefed on the case.
Since 2017, when the N.S.A. lost control of the tool, EternalBlue, it has been picked up by state hackers in North Korea, Russia and, more recently, China, to cut a path of destruction around the world, leaving billions of dollars in damage. But over the past year, the cyberweapon has boomeranged back and is now showing up in the N.S.A.’s own backyard.
https://muropaketti.com/mobiili/israelilaisyritys-mainostaa-voimme-murtautua-mihin-tahansa-iphoneen/Israelilainen Cellebrite myy poliiseille ja muille viranomaisille työkalua, jonka avulla voi yrityksen mukaan murtautua mihin tahansa kohtuullisen tuoreeseen iPhoneen.
Cellebriten UFED Premium -työkalun avulla on mahdollista avata lukittu ja salattu iPhone tai iPad, jonka käyttöjärjestelmänä toimii mikä tahansa iOS-käyttöjärjestelmä versioiden iOS 7 ja iOS 12.3 väliltä, kertoo Wired. Työkalun avulla lukitusta ja salatusta puhelimesta voi kaivaa esiin muun muassa sähköposteja, tekstiviestejä ja muuta sisältöä.
Apple on tuomassa iPhoneihin ja iPadeihin iOS 13 -version jo tänä syksynä, mikä voi tehdä työkalusta jälleen tehottoman päivitettyjä laitteita vastaan. Applen puhelimien lisäksi UFED Premiumia voi käyttää muun muassa Samsung Galaxy S6 – S9 -mallien avaamiseen sekä Huawein, LG:n, Motorolan ja Xiaomin puhelimien hakkerointiin.
Olipa viranomaisten suorittamasta hakkeroinnista mitä tahansa mieltä, heikentää hakkerointiin soveltuvan työkalun olemassaolo Hacker House -tietoturvayhtiön perustaja Matthew Hickeyn mukaan joka tapauksessa laitteiden tietoturvaa. Hickey kertoo, että tämä on onnistunut ostamaan Cellebriten vanhoja hakkerointityökaluja eBaysta. Mikäli laitteet päätyvät vääriin käsiin, voivat myös rikolliset hyödyntää niitä laittomiin tarkoituksiin.
Uskon, että on mahdollista, että tätä käytettiin kaatamaan Lahden järjestelmät.
https://arstechnica.com/information...kers-remotely-sack-linux-and-freebsd-systems/The Linux and FreeBSD operating systems contain newly discovered vulnerabilities that make it easy for hackers to remotely crash servers and disrupt communications, researchers have warned. OS distributors are advising users to install patches when available or to make system settings that lower the chances of successful exploits.
The most severe of the vulnerabilities, dubbed SACK Panic, can be exploited by sending a specially crafted sequence of TCP Selective ACKnowledgements to a vulnerable computer or server. The system will respond by crashing, or in the parlance of engineers, entering a kernel panic. Successful exploitation of this vulnerability, tracked as CVE-2019-11477, results in a remote denial of service (DoS).
A second vulnerability also works by sending a series of malicious SACKs that consumes computing resources of the vulnerable system. Exploits most commonly work by fragmenting a queue reserved for retransmitting TCP packets. In some OS versions, attackers can cause what’s known as an “expensive linked-list walk for subsequent SACKs.” This can result in additional fragmentation, which has been dubbed “SACK slowness.” Exploitation of this vulnerability, tracked as CVE-2019-11478, drastically degrades system performance and may eventually cause a complete DoS.
Both of these vulnerabilities exploit the way the OSes handle the above-mentioned TCP Selective ACKnowledgement (abbreviated SACK). SACK is a mechanism that allows a computer on the receiving end of a communication to apprise the sender of what segments have been successfully sent so that any lost ones can be resent. The parties set up the use of SACK during the three-way handshake that establishes the initial connection. The exploits work by overflowing a queue that stores received packets.
A vulnerability in FreeBSD 12 (tracked as CVE-2019-5599) works similarly to CVE-2019-11478 but instead interacts with the RACK send map of that OS.
A fourth vulnerability, tracked as CVE-2019-11479, can slow down affected systems by lowering the maximum segment size for a TCP connection. The setting causes vulnerable systems to send responses across multiple TCP segments, each of which contains only 8 bytes of data. Exploits cause the system to consume large amounts of bandwidth and resources in a way that degrades system performance. Maximum segment size is a setting contained in the header of a TCP packet that specifies the total amount of data contained in a reconstructed segment.
https://blackmarble.sh/zipato-smart-hub/During the 0DAYALLDAY Research Event three vulnerabilities were discovered in the ZipaMicro Z-Wave Controller Model #: ZM.ZWUS and the Zipabox Z-Wave Controller Model #: 2AAU7-ZBZWUS. Two vulnerabilities are in the design and implementation of the authentication mechanism in the Zipato Application Programming Interface (API). The third vulnerability is embedded SSH private key for ROOT which isn't unique and can be extracted.
Here's a great idea: Why don't we hardcode the same private key into all our smart home hubs?
Another day, another appalling Internet of S**t security flaw
Ei enään kannata tärvellä tulevaisuuttaan tekemällä tyhmyyksiä, kun homman voi hoitaa laillisesti esim olemalla pentesting bisneksessä taikka sysadminin taikka vastaavana lafkassa, joka antaa sulle aikaa, resursseja ja rahaa itsesi toteuttamiseen. Valtiolliset hoitavat hyökkäysbisnestä ja jos olet rikollinen, niin aika vaikea venkuilla ulos siitä koukusta.
https://www.theregister.co.uk/2019/07/04/reports_of_cyber_breaches_fall_due_to_less_virus_nasties/UK businesses have reported a significant fall in cyber attacks over the last 12 months.
The proportion identifying breaches or attacks in the least year was 32 per cent, compared with 43 per cent in 2018 and 46 per cent in 2017, according to a survey of 1,566 businesses by the Department for Digital, Culture, Media and Sport (DCMS) (PDF).
Those figures echo the Crime Survey for England and Wales, which found that between September 2017 and September 2018, the number of computer misuse incidents among individuals fell from 1.5 million to 1 million.
This was driven, according to Office for National Statistics data, by a significant reduction in computer viruses (down by 45 per cent over the same period).
However, the DCMS report said other factors could be at play such as more investment in cybersecurity, better compliance due to GDPR, or a change in attack behaviour.
For example, those carrying out cyber attacks could be focusing on a narrower (though still numerous) set of businesses.
This fits with another broad trend in the survey showing that, among the 32 per cent of businesses that did identify breaches or attacks, the median number they recall facing has gone up, from two attacks in 2017 to six in 2019.
Of those targeted, phishing attacks were the most common, with 80 per cent having been subject to email scams, while 27 per cent said they had been hit by viruses, spyware or malware.
However, Ken Munro of Pen Test Partners said there are too many variables to make the findings conclusive.
"Are the number of antivirus reports down because organisations (rightly) don't consider them to be attacks/breaches or incidents? Or is it because the antivirus products aren't detecting the types of malware that are being used now?"
He added: "Without analysing the quality of phishing attacks, the data is also meaningless. Are untargeted phishing attempts being filtered out upstream?
"I don't think anything can be concluded from the report other than that 'cyber stuff is still happening and some businesses are taking it more seriously'."
Hain duunia Product Security Officer paikasta ja tunnin sisään CVn lähettämisestä mulle sanottiin että en ole sopiva cybersecurity töihin.
Download the report: https://www.issa.org/page/issa-esg-global-3rd-annual-cybersecurity-skills-survey or https://www.esg-global.com/esg-issa-research-report
https://www.globenewswire.com/news-...-Sounding-the-Alarm-for-Business-Leaders.htmlThe cybersecurity skills shortage is worsening for the third year in a row and has impacted nearly three quarters (74 percent) of organizations, as revealed today in the third annual global study of cybersecurity professionals by the Information Systems Security Association (ISSA) and independent industry analyst firm Enterprise Strategy Group (ESG).
Further the report confirms that the cybersecurity skills shortage continues to be the root cause of rising security incidents, as organizations remain plagued by a lack of end-user cybersecurity awareness and the inability to keep up with the growing cybersecurity workload. Almost half (48 percent) of respondents have experienced at least one security incident over the past two years with serious ramifications including lost productivity, significant resources for remediation, disruption of business processes and systems, and breaches of confidential data.
In fact, cybersecurity professionals are downright skeptical about their chances for success. Ninety-one (91) percent believe that most organizations are vulnerable to a significant cyber-attack. And an overwhelming 94 percent believe that the balance of power is with cyber-adversaries over cyber-defenders. With the battlefield advantage skewed, organizations face increasing and potentially devastating cyber-risks.
Despite these findings, for the third straight year, sixty-three (63) percent of organizations continue to fall behind in providing an adequate level of training for their cybersecurity professionals. The most acute skills shortages shifted this year to cloud security (33 percent), followed by application security (32 percent) and security analysis & investigations (30 percent).
In an era where business leaders are more reliant on technology for success and are facing more scrutiny and accountability than ever before, this lack of progress and the resulting cyber-risk for organizations and their shareholders, customers and business partners should be a cause for concern for business and technology leaders alike.
The research also indicates an alarming personal impact related to cybersecurity jobs. While cybersecurity professionals remain dedicated to their craft, attracted by the deep technical challenges and moral implications, this year’s study explores for the first time the causes and consequences of stress and burnout, including:
“Based upon the results of this year’s and past research projects, it is safe to conclude that cybersecurity progress has been marginal at best over the last three years. ESG and ISSA agree with security researcher, author and ISSA Hall of Fame recipient Bruce Schneier’s quote, ‘We may be making some cybersecurity improvements but we are getting worse faster.’ This issue should be of concern to technologists, business executives and private citizens and continues to cause an existential threat to national security,” said Jon Oltsik, Senior Principal Analyst and Fellow at the Enterprise Strategy Group (ESG) and the author of the report.
- Stressful aspects of the job: Forty (40) percent responded with keeping up with security needs of new IT initiatives, followed closely by “shadow” IT initiatives, trying to get end-users to better understand cyber-risks and change their behavior, and trying to get the business to better understand cyber risks.
- Added stress of new data privacy responsibilities: Almost one year in, GDPR is in full swing, and cybersecurity teams may not be up to the task. Eighty-four (84) percent claim that the cybersecurity team at their organization has taken a more active role with data privacy over the past 12 months, but 21 percent don’t believe the cybersecurity team has been given clear directions and 23 percent don’t believe the cybersecurity team has been given the right level of training.
- Job-related pressures driving virtual CISO (vCISO) as attractive career option: Ten (10) percent of organizations now employ a vCISO. Furthermore, 29 percent of CISOs are working as a vCISO while another 21 percent are considering it and 33 percent would consider it in the future. Almost half claim that working as a vCISO brings more variety and flexibility to a CISO position. CISOs are clearly seeking to avoid some of the politics and stress while taking more control of their careers.
“Organizations are looking at the cybersecurity skills crisis in the wrong way: it is a business, not a technical, issue. Business executives need to acknowledge that they have a key role to play in addressing this problem by investing in their people. In an environment of a ‘sellers market’ with 77 percent of cybersecurity professionals solicited at least once per month, the research shows in order to retain and grow cybersecurity professionals at all levels, business leaders need to get involved by building a culture of support for security and value the function,” said Candy Alexander, CISSP CISM, Executive Cybersecurity Consultant and ISSA International President.
Top 5 Roles in Addressing the Cybersecurity Skills Crisis
- Business Leaders: Twenty-three (23) percent of respondents say business managers don’t understand and/or support an appropriate level of cybersecurity. Job satisfaction and employee retention depends largely upon business leadership’s commitment to cybersecurity, in addition to career incentives and competitive compensation. The number one recommended action is adding cybersecurity goals and metrics to IT and business managers.
- CISOs: CISOs need to be more active with business executives. They want a seat at the board table. CISO success depends upon characteristics like communication skills, leadership skills, a strong relationship with business executives, and a strong relationship with the CIO and IT leadership team.
- Practitioners: While 93 percent of survey respondents agree that cybersecurity professionals must keep up with their skills, 66 percent claim that cybersecurity job demands often preclude them from skills development. This imbalance must be addressed. Additionally, 57 percent of respondents say security certifications such as CISSP are far more useful in getting a job than doing a job. Prioritize practical skills development over certifications.
- HR and Recruiters: Forty-one (41) percent of survey respondents say that their organization has had to recruit and train junior personnel rather than hire more experienced infosec professionals. Designing their own training program will develop future talent and loyalty. Casting a wider net beyond IT and finding transferable business skills and cross career transitions will help expand the pool of talent.
- Educators and Trainers: KSA development with face-to-face interaction is most effective, such as attending specific cybersecurity training courses, participating in professional organizations and events, attending trade shows, and participating in on-the-job mentoring programs.
Finally, the private sector can only do so much. The public sector needs to help by investing more in training and education, public awareness, and scholarships and grants.
Download the report: https://www.issa.org/page/issa-esg-global-3rd-annual-cybersecurity-skills-survey or https://www.esg-global.com/esg-issa-research-report
Coffee Man
Respected Leader
Isoveli valvoo. Tai paremminkin kalastelee tietoja. Tämän johtopäätöksen voi tehdä kuunnellessa Kankaanpään kaupungin tietoturvapäällikön Jukka Ehdon toteamusta siitä, miten kaupungin tietoverkkoon kohdistuu hyökkäysyrityksiä aina kun Niinisalossa järjestetään sotaharjoituksia.

 www.iltalehti.fi
www.iltalehti.fi
– Kaupungin verkkoa kohtaan on jatkuva mielenkiinto. Tähän mennessä hyökkäykset eivät ole päässeet palomuurin läpi. Noin 70 prosenttia hyökkäyksistä on suhteellisen vaarattomia, mutta loput 30 prosenttia ovat sellaisia mitkä todella laittavat tietoturvan koetukselle, kertoo Ehto.

Loputon taistelu: Aina kun Niinisalossa on sotaharjoitus, Kankaanpään kaupungin palomuuriin kohdistuu poikkeuksellisen paljon kyberhyökkäyksiä
Aina kun Niinisalossa on sotaharjoitus, Kankaanpään kaupungin palomuuriin kohdistuu poikkeuksellisen paljon kyberhyökkäysyrityksiä. Kankaanpää panostaa tietoturvaan kymmeniä tuhansia euroja vuodessa.
– Kaupungin verkkoa kohtaan on jatkuva mielenkiinto. Tähän mennessä hyökkäykset eivät ole päässeet palomuurin läpi. Noin 70 prosenttia hyökkäyksistä on suhteellisen vaarattomia, mutta loput 30 prosenttia ovat sellaisia mitkä todella laittavat tietoturvan koetukselle, kertoo Ehto.
https://threatpost.com/linux-ransomware-nas-servers/146441/A rare instance of ransomware targeting Linux-based file storage systems (network-attached storage servers, specifically) has been spotted, spreading via 15 separate but related campaigns. The adversaries behind the effort are continuing their depredations on an ongoing basis, according to researchers, so targets are expected to proliferate.
Researchers at Intezer Labs dubbed the malware “QNAPCrypt,” after QNAP, one of the larger NAS server vendors out there.
“NAS servers normally store large amounts of important data and files, which make them a valuable target for attackers and especially a viable target for ransomware campaigns,” Intezer researcher Ignacio Sanmillan said in an analysis of the malware, posted this week. However, he noted that “It is rare to see ransomware being used to target the Linux operating system.”
Mili
Eversti
Galileo ollut poissa käytöstä jo perjantaista lähtien, tivi uutisoi torstaista.
"... Järjestelmän tilaa kuvaavan sivuston mukaan kaikki konstellaation satelliitit ovat joko pois käytöstä tai ne ovat testitilassa.
Ongelmat liittyvät kerrottujen tietojen Galileon maanpäälliseen infrastruktuuriin, joten satelliitit itsessään ovat toimintakuntoisia vaikka ne eivät kykenekään tarjoamaan eurooppalaisille paikannustietoa. ..."
"... Järjestelmän tilaa kuvaavan sivuston mukaan kaikki konstellaation satelliitit ovat joko pois käytöstä tai ne ovat testitilassa.
Ongelmat liittyvät kerrottujen tietojen Galileon maanpäälliseen infrastruktuuriin, joten satelliitit itsessään ovat toimintakuntoisia vaikka ne eivät kykenekään tarjoamaan eurooppalaisille paikannustietoa. ..."
https://www.theguardian.com/world/2...ial-records-of-nearly-every-bulgarian-exposedA 20-year-old cybersecurity worker has been arrested in Bulgaria and charged with hacking the personal and financial records of millions of taxpayers, as police continue to investigate the country’s biggest ever data breach.
Bulgaria’s NRA tax agency is facing a fine of up to €20m ($22.43m) over the hack, which was revealed this week and is thought to have compromised the records of nearly every working adult among the country’s population of 7 million.
Speaking at a government meeting on Wednesday, prime minister Boyko Borissov described the arrested man as a “wizard” hacker and said the country should hire similar “unique brains” to work for the state.
https://www.theregister.co.uk/2019/07/18/dutch_cops_malware_arrest/A 20-year-old man from the Netherlands accused of building and selling Office macro malware was arrested Wednesday.
The Dutch National Police's Office of the Team High Tech Crime (THTC) unit claimed the unnamed bloke, cuffed while on his computer as cops swooped on his home, was responsible for building, selling, and supporting the Rubella, Cetan, and Dryad malware kits.
The toolkits allowed criminals to build Office files with malicious macro code embedded in the documents. When the victim opened the file, usually delivered by spear-phishing or spam, the macro code would then proceed to download and open the malware payload.
While macro attacks are relatively old-school and don't generate headlines the way more exotic exploits and other forms of infection do, the poisoned documents remain a tried-and-true way for criminals to sneak malicious code onto victim machines, particularly at the enterprise level where workers are used to opening documents without much scrutiny. In this case, the macro kits were every bit as polished and professional as other crimeware packages, police said.
"The toolkit was marketed with colorful banners on different underground forums," said John Fokker and Thomas Roccia, two McAfee engineers who helped Dutch police track own the man.
"For the price of $500 per month you could use his toolkit to weaponize Office documents that bypass end-point security systems and deliver a malicious payload or run a PowerShell Code of your choice."
Kustaanmiekka
Kenraali

Loputon taistelu: Aina kun Niinisalossa on sotaharjoitus, Kankaanpään kaupungin palomuuriin kohdistuu poikkeuksellisen paljon kyberhyökkäyksiä
Aina kun Niinisalossa on sotaharjoitus, Kankaanpään kaupungin palomuuriin kohdistuu poikkeuksellisen paljon kyberhyökkäysyrityksiä. Kankaanpää panostaa tietoturvaan kymmeniä tuhansia euroja vuodessa.
Aina kun Niinisalossa on sotaharjoitus, Kankaanpään kaupungin palomuuriin kohdistuu poikkeuksellisen paljon kyberhyökkäysyrityksiä.
Kankaanpää panostaa tietoturvaan kymmeniä tuhansia euroja vuodessa.
Isoveli valvoo. Tai paremminkin kalastelee tietoja.
Tämän johtopäätöksen voi tehdä kuunnellessa Kankaanpään kaupungin tietohallintopäällikkö Jukka Ehdontoteamusta siitä, miten kaupungin tietoverkkoon kohdistuu hyökkäysyrityksiä aina kun Niinisalossa järjestetään sotaharjoituksia.
– Jo viikkoa ennen sotaharjoitusten alkua ja niiden aikana kaupungin palomuuriin kohdistuu huomattavasti kovempaa painetta kuin normaalitilanteessa.
Vastaavanlaisia havaintoja on tehty myös muissa varuskuntakaupungeissa, kertoo Ehto.
Se, miksi sotilasorganisaation ulkopuolinen taho, kuten kaupunki tai kunta, joutuu kyberhyökkäysten kohteeksi sotaharjoitusten aikaan on vaikea sanoa.
Toisaalta, hetken tuumaamisen jälkeen jonkinlaista logiikkaa siitäkin löytyy.
– Uskoisin, että hyökkäyksillä yritetään saada tietoa esimerkiksi vedenkulutuksesta tai sähkönkäytöstä.
Mistä tahansa, mikä voisi liittyä varuskuntaan.
Isolla rahalla
Kankaanpään kaupunki on jo vuosien ajan panostanut jopa poikkeuksellisen paljon tietoturva-asioihin.
Vuositasolla siihen käytetään kymmeniä tuhansia euroja.
– Satsaus on merkittävä, mutta myös kannattava.
Pitää ajatella asia niin, että tietoturvallisuuteen satsatut varat turvaavat sen, että tietoverkkomme on turvassa.
Pahimmassa tapauksessa koko verkkomme kaapattaisiin ja siellä olevat tiedot vaarantuisivat.
Järjestelmän uudelleen pystyttäminen voi viedä paljon aikaa ja rahaa.
Kyberuhka on jokapäiväistä.
– Kaupungin verkkoa kohtaan on jatkuva mielenkiinto.
Tähän mennessä hyökkäykset eivät ole päässeet palomuurin läpi.
Noin 70 prosenttia hyökkäyksistä on suhteellisen vaarattomia, mutta loput 30 prosenttia ovat sellaisia mitkä todella laittavat tietoturvan koetukselle, kertoo Ehto.
Kaupunki testaa oman tietoturvansa kestävyyttä säännöllisesti.
Taannoin kaupunki oli mukana myös tietoturva-ammattilaisten järjestämässä Kuntahaasteessa.
Hyökkäysten seurauksena löytyi kaksi haavoittuvuutta, mitkä on luonnollisesti nyt korjattu.
Hallinkorva
Ylipäällikkö
Tämä on iso.
Russia's Secret Intelligence Agency Hacked: 'Largest Data Breach In Its History'

 www.forbes.com
www.forbes.com
Russia's Secret Intelligence Agency Hacked: 'Largest Data Breach In Its History'

Russia's Secret Intelligence Agency Hacked: 'Largest Data Breach In Its History'
Hackers successfully targeted Russia's state security agency last week through a major contractor, stealing and publishing details of secret internet projects including social media scraping and Tor de-anonymization.
 www.forbes.com
www.forbes.com
New York
https://www.cbsnews.com/news/nyc-su...e-resumes-after-trains-halted-mta-2019-07-20/— About a third of New York City's subway lines were suspended for more than an hour during Friday's hot evening commute, and the head of the city's Transit Authority acknowledged that the agency "did not know exactly where our trains were." A computer system failure that resulted in the snafu stranded some passengers underground and sent others searching for alternate ways home.
The stoppage affected the No. 1, 2, 3, 4, 5 and 6 trains that serve swaths of Manhattan, the Bronx and Brooklyn. It also halted the S shuttle train that links Grand Central Terminal and Times Square — two of the city's busiest stations.
The Metropolitan Transportation Authority (MTA) warned that there would still be "extensive delays" in the system, which serves more than 5 million people per day, even after service began to resume Friday night.
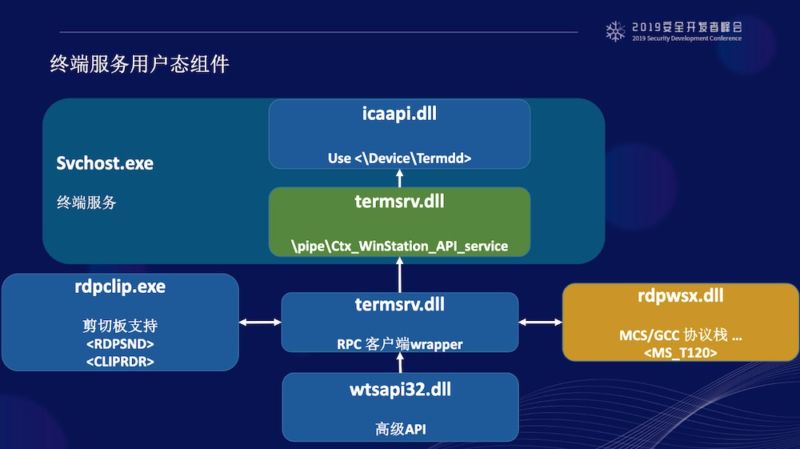
A security researcher has published a detailed guide that shows how to execute malicious code on Windows computers still vulnerable to the critical BlueKeep vulnerability. The move significantly lowers the bar for writing exploits that wreak the kinds of destructive attacks not seen since the WannaCry and NotPetya attacks of 2017, researchers said.
As of three weeks ago, more than 800,000 computers exposed to the Internet were vulnerable to the exploit, researchers from security firm BitSight said last week. Microsoft and a chorus of security professionals have warned of the potential for exploits to sow worldwide disruptions. The risk of the bug, found in Microsoft's implementation of the remote desktop protocol, stems from the ability for attacks to spread from one vulnerable computer to another with no interaction required of end users.

Microsoft practically begs Windows users to fix wormable BlueKeep flaw
With 1M computers still unpatched, company tries to prevent worldwide wormpocalypse.
 arstechnica.com
arstechnica.com
