Kaksi oli jo muttei kolmas.
Huh huh... teillä tulee kiirus, kolme suojattavaa kahden sijaan

Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
Kaksi oli jo muttei kolmas.

Plus kaikki muut, no saatiin yksi osasto lisää.Huh huh... teillä tulee kiirus, kolme suojattavaa kahden sijaan
https://tech.slashdot.org/story/17/...-wants-isps-to-protect-customers-from-virusesIn a column in The West Australian, Dan Tehan, Australia's cybersecurity minister, wrote: "Just as we trust banks to hold our money, just as we trust doctors with our health, in a digital age we need to be able to trust telecommunications companies to protect our information from threats." A companion news article in the same newspaper cited Tehan as arguing that "the onus is on telecommunications companies to develop products to stop their customers being infected with viruses"...
Tehan's government roles include assisting the prime minister on cybersecurity, so folks throughout Australia perked up when he said all this. However, it's not clear if there's an actual plan behind Tehan's observations -- or if there is, whether it will be backed by legal mandates... Back home in Australia, some early reactions to the possibility of any new government interference weren't kind. In iTWire, Sam Varghese said, "Dan Tehan has just provided the country with adequate reasons as to why he should not be allowed anywhere near any post that has anything to do with online security."
https://threatpost.com/dan-geer-cybersecurity-humanitys-future-conjoined/125316/Given the intertwinement of technology with communication, politics, economies and overall human progress, it seems to go hand-in-hand that cybersecurity must be elevated in parallel.
Dan Geer, considered atop the food chain of security thinkers, said during last week’s Source Boston conference that cybersecurity and humanity’s future are “conjoined”, and since humans are evolving faster than at any other time in history, choices must be made about how to protect us.
“To be deadly serious about cybersecurity requires that—either—we damp down the rate of change, slowing it enough to give prediction operational validity—or—we purposely increase unpredictability so that the opposition’s targeting exercise grows too hard for them to do,” Geer said. “In the former, we give up many and various sorts of progress. In the latter, we give up many and various sorts of freedom as it would be the machines then in charge, not us. Either way, the conjoining is irreversible.”
Geer’s keynote included 26 predictions, highlighted by a declaration that cybersecurity “is and will remain the paramount national security risk.” Many of his predictions carried a national security slant, starting with attribution between nation states.
Geer said that since weapons such as Stuxnet can never be assuredly attributed, they will never “ensure threat-stasis” as did the concept of mutual assured destruction with nuclear threats.
“The reason is attribution: while intercontinental ballistic missiles have a visible flight path and a limited number of launch-capable governments, offensive software has neither,” Geer said.
That won’t stop governments from coveting mechanisms for assuring attribution such as a geocoding of the Internet similar to what exists for mobile devices today, he said.
Governments will also continue to be the top consumer of zero-days, and policies will be crafted that will keep technology developed by an adversarial sovereign nation from running on critical infrastructure.
“This will extend to cryptographic gear including any sensor product with hardware embodied cryptographic code,” Geer said. “Industrial espionage will thus rise in importance to nation states, as if it were not high enough already.”
Geer also said we should expect offensive capabilities to be integrated into conventional network infrastructure, calling it “all but certain.”
“Much of that pre-deployment will initially be for tactical denial of information service in one form or another, but is likely to expand into disinformation as soon as sensors assume a place in the critical path for autonomous devices,” Geer said.
http://www.theregister.co.uk/2017/05/02/clinton_election_loss/Hillary Clinton today gave her first full interview since dramatically losing the US presidential election – and has placed the blame for her downfall on Russian hackers, FBI director James Comey and Wikileaks.
"If the election had been on October 27, I would be your president," Clinton told CNN anchor Christiane Amanpour at a women's event in New York.
https://threatpost.com/intel-patches-nine-year-old-critical-cpu-vulnerability/125331/“We have been warning Intel about the vulnerability tied to Active Management Technology for years. Now, finally it’s realized there is a vulnerability here that needs to be patched,” said Charlie Demerjian, founder of Stone Arch Networking Services in an interview with Threatpost. He maintains that every Intel platform, from Nehalem in 2008 to Kaby Lake in 2017, has a remotely exploitable security hole in the chipset’s Management Engine (ME).
In an article posted to the website SemiAccurate.com Monday–before Intel issued its advisory–Demerjian asserted Intel would patch a flaw first identified in June 2016 by researcher Damien Zammit. In an expose of Intel’s Management Engine, Zammit claimed last year that there was a vulnerability in Intel x86s chips that created a secret backdoor allowing a third-party to use undetectable rootkits against Intel PCs.
In a statement in response to Zammit’s allegation, Steve Grobman, chief technology officer for Intel Security, refuted the claim calling the feature a boon to admins who managed large installs of remote PCs.
When Threatpost asked Intel if the vulnerability that it warned of on Monday was tied to the same security issues discussed in June 2015, Moss said he was looking into it.
“I don’t know if there is any relationship to prior allegations. This current update is based on a report that we received in March from a security researcher. And to my knowledge it doesn’t have anything to do with anything before that,” Moss told Threatpost.
The vulnerability patched by Intel on Monday is a flaw found in an aspect of the Active Management Technology system called Intel Management Engine. This component runs on an ARC microprocessor that’s physically located inside the Intel chipset.
“The ME is capable of accessing any memory region without the main x86 CPU knowing about the existence of these accesses. It also runs a TCP/IP server on your network interface and packets entering and leaving your machine on certain ports bypass any firewall running on your system,” according to Zammit.
“The problem is quite simple, the ME controls the network ports and has DMA (direct memory access) access to the system. It can arbitrarily read and write to any memory or storage on the system, can bypass disk encryption once it is unlocked (and possibly if it has not, SemiAccurate hasn’t been able to 100 percent verify this capability yet), read and write to the screen, and do all of this completely unlogged. Due to the network access abilities, it can also send whatever it finds out to wherever it wants, encrypted or not,” Demerjian wrote in his post.
Matthew Garrett, a developer at Red Hat, wrote on his blog Monday that the flaw will only impact those that have explicitly enabled Active Management Technology at some point. “Most Intel systems don’t ship with AMT. Most Intel systems with AMT don’t have it turned on,” he said.
Garrett added, fixing the problem won’t be easy for Intel or admins. “Fixing this requires a system firmware update in order to provide new ME firmware (including an updated copy of the AMT code). Many of the affected machines are no longer receiving firmware updates from their manufacturers, and so will probably never get a fix. Anyone who ever enables AMT on one of these devices will be vulnerable,” he said.

https://threatpost.com/ibm-destroy-usbs-infected-with-malware-dropper/125377/USB drives shipped with some IBM’s Storwize storage products are infected with malware, and the tech giant advises customers destroy the devices.
IBM would not comment on the source of the infection or where in the supply chain the interdiction happened, and instead referred Threatpost to an advisory. “There’s no additional statement at this time,” a spokesperson said.
IBM said the USB drives contain an initialization tool and the affected devices were shipped with IBM Storwize V3500, V3700 and V5000 Gen 1 systems.
The malware is a dropper detected by Kaspersky Lab as Reconyc. The dropper is a cybercrime tool used to install other malware on infected computers, primarily in Russia and India (37 percent and 17 percent respectively of all infections).
IBM said the infected drives have a part number 01AC585; Storwize systems with serial numbers starting with 78D2 are not affected, IBM said.
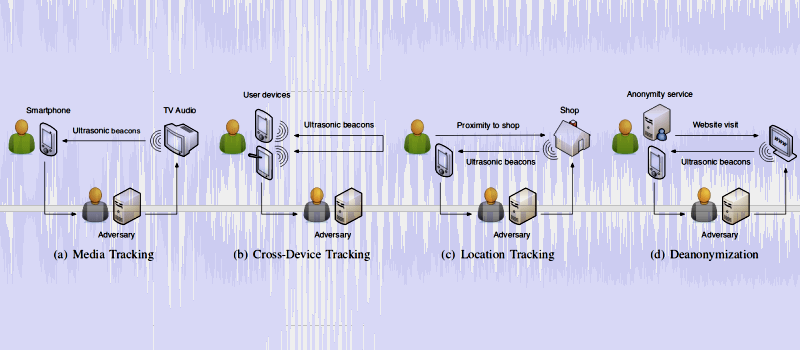
http://hackaday.com/2017/05/04/ultrasonic-tracking-beacons/An ultrasonic beacon is an inaudible sound with encoded data that can be used by a listening device to receive information on just about anything. Beacons can be used, for example, inside a shop to highlight a particular promotion or on a museum for guided tours where the ultrasonic beacons can encode the location. Or they can be used to track people consumers. Imagine if Google find outs… oh, wait… they already did, some years ago. As with almost any technology, it can be used to ‘do no harm’ or to serve other purposes.
Researchers from the Technische Universitat Braunschweig in Germany presented a paper about Ultrasonic Side Channels on Mobile Devices and how can they be abused in a variety of scenarios , ranging from simple consumer tracking to deanonymization. These types of ultrasonic beacons work in the 18 kHz – 20 kHz range, which the human being doesn’t have the ability to hear, unless you are under twenty years old, due to presbycusis. Yes, presbycusis. This frequency range can played via almost any speaker and can be picked up easily by most mobile device microphones, so no special hardware is needed. Speakers and mics are almost ubiquitous nowadays, so there is a real appeal to the technology.
In their research paper, presented last week at the IEEE European Symposium on Security and Privacy, they found that 234 current Android applications incorporate some type of ultrasonic listening technology and the number of apps with this tech is on the rise. They also found that physical locations like shopping malls are already adopting and emitting beacons. They covered SilverPush, Lisnr and ShopKick software implementations and also tested for beacons being emitted via TV channels, but with no success.
For some reason, there was not a single mention to Google Nearby technology nor its Nearby Messages API.
Acoustic covert channels are not new but they seem to take some time to emerge from the research papers to widespread technology, maybe because of their limitations, such as error-proneness and range. On the other hand, once it’s understood that these beacons can actually work reliably, this technology is just too juicy for advertising agencies not to use.
And other ‘agencies’ too.
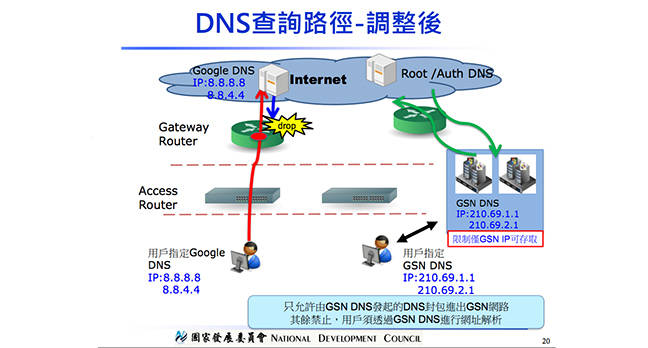
http://www.theregister.co.uk/2017/05/11/taiwan_gov_blocks_googles_public_dns/The Taiwanese government intends to block Google's public DNS service, citing cybersecurity concerns.
The question is whether those concerns are the government's or its citizens', with the government pushing its own DNS service – a setup that is typically used to spy on people's internet communications.
The announcement comes, somewhat unusually, in the form of a PDF of a presentation posted to the Government's Internet Service Network (GSN) news page.
Going through the presentation – written in Chinese – the GSN outlines the problem, as it sees it, with Google's DNS service, repeatedly highlighting DNS spoofing techniques and other cybersecurity issues.
"If you can reduce the use of restricted sources, then with the appropriate DNS protection mechanism, you can effectively reduce the risk of DNS spoofing," it notes, with numerous DNS diagrams that make it clear that Google's public DNS system should be viewed as one of those sources.
One diagram shows Google DNS service being used to circumvent a firewall – which is precisely what many Chinese citizens used it for in an effort to get around the Great Chinese Firewall. Another shows packets being dropped while using the service.
In contrast, the Taiwanese government's slides show the benefits of using its own DNS service (at 210.69.1.1) to search the internet, with China Telecom-owned ISP HiNet promoted in many of the examples.
It's not clear whether the block on Google's DNS service will be nationwide or solely for government employees. Or whether it will only be government employees that will be obliged to use the government-provided DNS service or all citizens. But as one slide makes it quite clear, in both pictures and writing, only DNS requests that go through the government's DNS service will be allowed, with all others prohibited.
No date is provided for when this new approach will be introduced.
http://www.theregister.co.uk/2017/05/10/sec_fines_three_chinese_traders/Three Chinese miscreants have made millions on the stock market using insider information stolen from US law firms.
That's according to America's financial watchdog, the SEC, which this month won a default judgment against the trio. The blokes infiltrated systems used by two New York law firms, extracted confidential documents describing upcoming mergers and acquisitions, and traded shares capitalizing on this information, we're told.
Chinese citizens Iat Hong, 26, Bo Zheng, 30, and Hung Chin, 50, were fined $8,895,561.12 after the SEC claimed they infected legal firms with malware. US District Judge Valerie Caproni of the Southern District of New York also issued an order [PDF] freezing any funds the trio had in the US.
"As we allege, the defendants' 'hacking to trade' scheme involved numerous levels of deception as they gained broad access to the nonpublic networks of two law firms, stole confidential information and then used it for substantial personal gain," SEC crime-buster Antonia Chion previously claimed.
"This action marks the end of their alleged deception and serves as a stark reminder to companies and firms that your networks can be vulnerable targets."
"As alleged, the defendants – including Iat Hong, who was arrested in Hong Kong on Christmas Day – targeted several major New York law firms, specifically looking for inside information about pending mergers and acquisitions," then-Manhattan US Attorney Preet Bharara said in December.
"This case of cyber-meets-securities fraud should serve as a wake-up call for law firms around the world: you are and will be targets of cyber hacking, because you have information valuable to would-be criminals."
Hong and Chin were well used to using malware to further their aims, according to prosecutors. They ran a robotics controller chip manufacturing business in Hong Kong, and it's claimed they also used software nasties to hack into competitors and steal product plans and proprietary design schematics. Hong was arrested in Macau although we know of no extradition process.
The three have been charged in the US with conspiracy to commit securities fraud, conspiracy to commit wire fraud, wire fraud, conspiracy to commit computer intrusion, unlawful access, and intentional damage. If found guilty they could spend 70 years in prison – if they ever reach American soil.
https://www.washingtonpost.com/worl...13e_story.html?ref=yfp&utm_term=.a57b5b421223‘You’re just meat’ - Ukrainian soldiers get chilling texts
...
“Guys, Parasha sold us out to the Yanks. Let’s go attack Kiev instead!”
—text message received on Feb. 12, 2015, at Debaltseve, Ukraine.
“Your account was charged 10 hryvnias (then about $0.50) to support the Anti-Terrorism Operation.”
—text message received on Oct. 6, 2015, at Schastia, Ukraine.
“Are you ready to die for Poroshenko’s golden deposits!?”
—text message received at 12:58 a.m. on Oct. 16, 2015, at Checkpoint 29, an hour from Luhansk, Ukraine.
“Who is robbing your family while you are paid pennies waiting for your bullet?”
—text message received at 11:46 a.m. on Nov. 11, 2015, at Checkpoint 29.
“Murderer from the Ukrainian Armed Forces. The East won’t forgive you and the West won’t remember you!”
—text message received on Nov. 17, 2015, at Checkpoint 29.
“Ukrainian Armed Forces, you’re just meat for your commanders.”
—text message received at 9:32 a.m. on Jan. 31 in Avdiivka, Ukraine.


https://theintercept.com/2017/05/11...breaking-computer-project-to-entire-internet/In early December 2016, Adam was doing what he’s always doing, somewhere between hobby and profession: looking for things that are on the internet that shouldn’t be. That week, he came across a server inside New York University’s famed Institute for Mathematics and Advanced Supercomputing, headed by the brilliant Chudnovsky brothers, David and Gregory. The server appeared to be an internet-connected backup drive. But instead of being filled with family photos and spreadsheets, this drive held confidential information on an advanced code-breaking machine that had never before been described in public. Dozens of documents spanning hundreds of pages detailed the project, a joint supercomputing initiative administered by NYU, the Department of Defense, and IBM. And they were available for the entire world to download.
The supercomputer described in the trove, “WindsorGreen,” was a system designed to excel at the sort of complex mathematics that underlies encryption, the technology that keeps data private, and almost certainly intended for use by the Defense Department’s signals intelligence wing, the National Security Agency. WindsorGreen was the successor to another password-cracking machine used by the NSA, “WindsorBlue,” which was also documented in the material leaked from NYU and which had been previously described in the Norwegian press thanks to a document provided by National Security Agency whistleblower Edward Snowden. Both systems were intended for use by the Pentagon and a select few other Western governments, including Canada and Norway.

Intelligence agencies like the NSA hide code-breaking advances like WindsorGreen because their disclosure might accelerate what has become a cryptographic arms race. Encrypting information on a computer used to be a dark art shared between militaries and mathematicians. But advances in cryptography, and rapidly swelling interest in privacy in the wake of Snowden, have helped make encryption tech an effortless, everyday commodity for consumers. Web connections are increasingly shielded using the HTTPS protocol, end-to-end encryption has come to popular chat platforms like WhatsApp, and secure phone calls can now be enabled simply by downloading some software to your device. The average person viewing their checking account online or chatting on iMessage might not realize the mathematical complexity that’s gone into making eavesdropping impractical.
The spread of encryption is a good thing — unless you’re the one trying to eavesdrop. Spy shops like the NSA can sometimes thwart encryption by going around it, finding flaws in the way programmers build their apps or taking advantage of improperly configured devices. When that fails, they may try and deduce encryption keys through extraordinarily complex math or repeated guessing. This is where specialized systems like WindsorGreen can give the NSA an edge, particularly when the agency’s targets aren’t aware of just how much code-breaking computing power they’re up against.
http://www.theregister.co.uk/2017/05/11/us_security_chiefs_dont_trust_kaspersky/Five US spy bosses, and the acting FBI chief, today told the Senate intelligence committee they do not trust software from Russian antivirus maker Kaspersky.
And as a result, they are reviewing Uncle Sam's use of the software. It is feared the toolkit could be commandeered by the Kremlin to attack and sabotage computers used by the American government.
Daniel Coats, the Director of National Intelligence; Michael Pompeo, Director of the CIA; Michael Rogers, Director of the NSA; Andrew McCabe, Acting Director of the FBI; Vincent Stewart, Director of the Defense Intelligence Agency; and Robert Cardillo, Director of the National Geospatial-Intelligence Agency didn't agree on much, but they did agree on two things – they believe Putin meddled with the US elections, and they don't recommend using Kaspersky's software.
Suomessakin on laajalti yrityspuolella HP:n läppäreitä ja tässä on kohtuullisen raju väite Sveitsiläiseltä tietoturvapajalta:
Vakoiluohjelma sijaitsee käyttäjän sisään kirjautuessa automaattisesti käynnistyvässä c:\windows\system32\mictray64.exe-tiedostossa. Ohjelma kirjoittaa tallentamansa tiedot C:\Users\Public\MicTray.log-tiedostoon.
Asiansa osaava käyttäjä voi välttää ongelman uudelleennimeämällä tai poistamalla mictray64.exe-tiedoston. Tämän myötä ääniohjauksen pikanäppäimet lakkaavat kuitenkin toimimasta, eikä toimenpidettä suositella tavallisille käyttäjille.

WCry saattaa tulla hyvin laajaa tuhoa aiheuttaneeksi. Tänään aamulla uutisia monista maista. http://www.tivi.fi/Kaikki_uutiset/arhakka-haittaohjelma-leviaa-asenna-nama-paivitykset-heti-6649011 ja https://arstechnica.com/security/20...re-worm-is-shutting-down-computers-worldwide/
Kuuluu haittaohjelma toimivan tuollaisesakin combossa.
