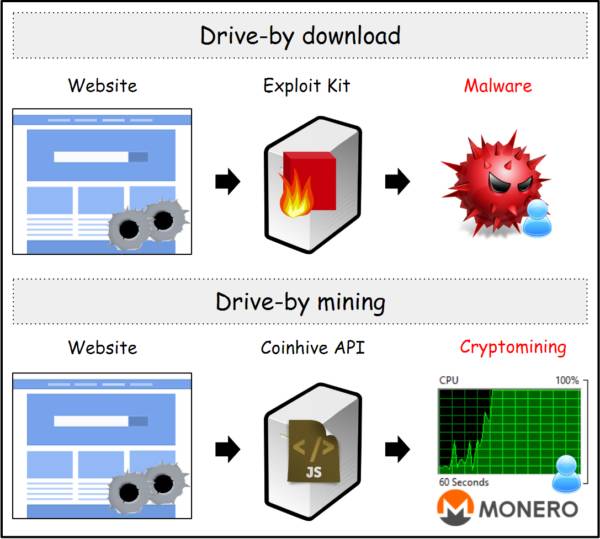
#PWHashMining
http://www.theregister.co.uk/2017/10/31/fireeye_simplifies_hashcat/FireEye reckons sysadmins need help enforcing enterprise password rules, so it's released and open-sourced a tool that distributes password testing across multiple GPU-equipped machines.
GoCrack (at GitHub) combines the management of a red team's cracking tasks with privilege management, so the password tests don't fall into the wrong hands.
Only creators of task data, or those they delegate permission to, can see the contents of a cracking task. “Modifications to a task, viewing of cracked passwords, downloading a task file, and other sensitive actions are logged and available for auditing by administrators”, the company explains in its blog post.
The cracking engine's dictionaries, mangling rules and the like are made available to other users, but the administrator can protect them against views or edits.
Under the hood, GoCrack uses hashcat v3.6 or higher, and while it doesn't need an external database server, it supports LDAP or database-backed authentication.
The server component runs on any Linux server with Docker, and NVIDIA Docker lets GoCrack run in a container with full GPU access.
Future plans include MySQL and PostgreSQP database support, UI support for file editing, automatic task expiration, and expanded hashcat configuration.