LinkkiThe American military has ordered a review of its grunts' personal electronics – after the Strava fitness app used by soldiers revealed base locations and other operational security gaffes.
In November, the exercise-tracking software maker released a "heatmap" to show where in the world people were using the application to monitor their daily workouts.
Unfortunately, because not all users marked their training information private, the map revealed military bases and the jogging routes of personnel. It also highlighted dangerously stupid explorers, and the data allowed viewers to drill down into an individual's fitness stats.
In response, the Pentagon has urged servicemen and women to lock down the privacy settings on their apps – which, er, they should really have done in the first place. Meanwhile, top brass will come up with new rules, if necessary.
"We take these matters seriously, and we are reviewing the situation to determine if any additional training or guidance is required, and if any additional policy must be developed to ensure the continued safety of Department of Defense personnel at home and abroad," Army Colonel Robert Manning III said at a Pentagon news conference on Monday.
"DoD personnel are advised to place strict privacy settings on wireless technologies and applications. The heat map incident re-emphasizes the need for service members to be cautious about what data to share via wearable electronic devices."
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
LinkkiPython code has emerged that automatically searches for vulnerable devices online using Shodan.io – and then uses Metasploit's database of exploits to potentially hijack the computers and gadgets.
You set this script running, it crawls the internet looking for machines that are possibly vulnerable to attack – typically due to unpatched security bugs – and automatically takes over them for you. No super-l33t skills required.
We're surprised it took this long.
The software, posted publicly on GitHub this week by someone calling themselves Vector, is called AutoSploit. It makes mass hacking exceedingly easy. After collecting targets via the Shodan search engine – an API key is required – the Python 2.7 script attempts to run Metasploit modules against them.
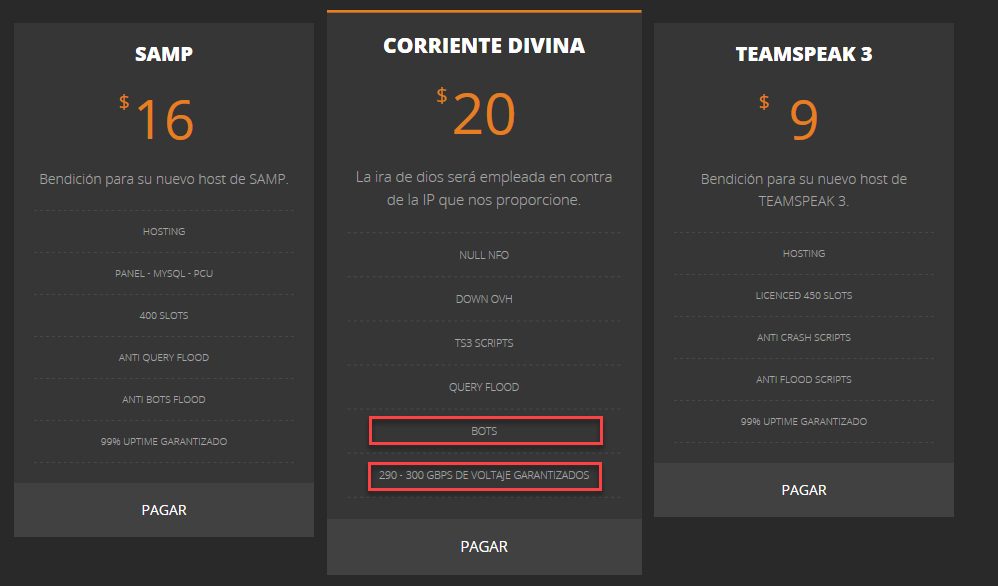
LinkkiOrganizers of a new botnet made up of infected home and small office routers are brazenly selling denial-of-service attacks of once unimaginable volumes for just $20 per target.
Calling itself Los Calvos de San Calvicie, the group is advertising several services on this site. Among the services are distributed denial-of-service attacks of 290 to 300 gigabits per second for $20 each. While a third the size of some of the biggest recorded attacks, 290Gbps is still enough to bring most sites down unless they seek DDoS mitigation services, which in many cases cost considerable amounts of money. Just five years ago, 300Gbps was considered enough volume to shut down the Internet's core infrastructure.
http://www.theregister.co.uk/2018/02/03/security_roundup/January's Meltdown and Spectre processor security design flaws continue to haunt the IT world.
Fortinet put out an advisory on Tuesday warning 119 variants of code that exploit the CPU security cockups were detected doing the rounds last month.
The samples were collected by security lab AV-Test. Fortinet was able to confirm 83 per cent of them are proof-of-concept exploits, and couldn't find the other 17 per cent to test.
The discovery triggered a few excitable headlines, but the key thing is: this is proof-of-concept code that tests to see if it's possible to exploit Meltdown or Spectre on a machine. It's not 119 pieces of new malware that leverage the hardware flaws to steal passwords and other sensitive information from applications and the operating system.
Of course, the proof-of-concept code can be baked into software nasties to use once they've infected systems. So far, though, no known malware is abusing Meltdown or Spectre, and at least antivirus packages are getting on top of the issue by identifying code that attempts to exploit the processor faults.
"The samples will only check to see if the flaws can be exploited. The PoCs do not do any damage other than being able to capture the data in real-time via side channel attack," John Welton, a director at Fortinet, told The Register.
"All the samples we looked at were benign and based on proof of concept code.”
http://www.theregister.co.uk/2018/02/05/ncsc_active_defence/GCHQ's National Cyber Security Centre claims that its strategy of "actively defending" the UK against high-volume commodity attacks is working.
The Active Cyber Defence (ACD) programme aims to "protect the majority of people in the UK from the majority of the harm, caused by the majority of the attacks, for the majority of the time". The strategy, announced in September 2016, is intended to tackle the high-volume commodity attacks that affect people's everyday lives, rather than highly sophisticated and targeted attacks, which are contested through other tactics.
A year since the strategy's inception, Dr Ian Levy, technical director of the National Cyber Security Centre, declared: "People in the UK are objectively safer in cyberspace because of the ACD programme".
https://threatpost.com/covert-data-channel-in-tls-dodges-network-perimeter-protection/129779/Researchers have released a proof-of-concept framework for a new covert channel for data exchange using the Transport Layer Security (TLS) protocol. The method exploits the public key certificate standard X.509 and could allow for post-intrusion C2 communication and data exfiltration to go unnoticed despite network perimeter protections.
According to Fidelis researchers, the covert data exchange takes advantage of the TLS handshake when certificates are exchanged. The technique doesn’t require – or ever establish – a TLS session. The covert data exchange takes place as the clients are negotiating the handshake using the TLS X.509 extension.
“This would enable someone who already has persistence inside of a network to get past the perimeter defenses and perform a data exchange,” said Chad Robertson, director of threat research at Fidelis in an interview. “It’s a unique and novel method of covert data exchange and would have to be specifically looked for at the perimeter by a device that was inspecting certificates or anomalies in order to see the data embedded inside certificates.”
The attack is similar to data cloaking techniques such as DNS tunneling that takes advantage of the TXT transport layer within the DNS protocol used by top and second level domain name system servers.
Fidelis said that in the case of abusing the X.509 extension, an adversary could “place arbitrary binary data into the certificate or utilizing them as a covert channel,” researchers said.
Maidan
Respected Leader
Russian hackers hunt hi-tech secrets, exploiting US weakness
BY JEFF DONN, DESMOND BUTLER and RAPHAEL SATTER
Today
https://apnews.com/cc616fa229da4d59b230d88cd52dda51Link copied!
WASHINGTON (AP) — Russian cyberspies pursuing the secrets of military drones and other sensitive U.S. defense technology tricked key contract workers into exposing their email to theft, an Associated Press investigation has found.
What ultimately may have been stolen is uncertain, but the hackers clearly exploited a national vulnerability in cybersecurity: poorly protected email and barely any direct notification to victims.
The hackers known as Fancy Bear, who also intruded in the U.S. election, went after at least 87 people working on militarized drones, missiles, rockets, stealth fighter jets, cloud-computing platforms or other sensitive activities, the AP found.
BY JEFF DONN, DESMOND BUTLER and RAPHAEL SATTER
Today
https://apnews.com/cc616fa229da4d59b230d88cd52dda51Link copied!
WASHINGTON (AP) — Russian cyberspies pursuing the secrets of military drones and other sensitive U.S. defense technology tricked key contract workers into exposing their email to theft, an Associated Press investigation has found.
What ultimately may have been stolen is uncertain, but the hackers clearly exploited a national vulnerability in cybersecurity: poorly protected email and barely any direct notification to victims.
The hackers known as Fancy Bear, who also intruded in the U.S. election, went after at least 87 people working on militarized drones, missiles, rockets, stealth fighter jets, cloud-computing platforms or other sensitive activities, the AP found.
http://www.securityweek.com/stealthy-data-exfiltration-possible-magnetic-fieldsResearchers have demonstrated that a piece of malware present on an isolated computer can use magnetic fields to exfiltrate sensitive data, even if the targeted device is inside a Faraday cage.
A team of researchers at the Ben-Gurion University of the Negev in Israel have created two types of proof-of-concept (PoC) malware that use magnetic fields generated by a device’s CPU to stealthily transmit data.
A magnetic field is a force field created by moving electric charges (e.g. electric current flowing through a wire) and magnetic dipoles, and it exerts a force on other nearby moving charges and magnetic dipoles. The properties of a magnetic field are direction and strength.
The CPUs present in modern computers generate low frequency magnetic signals which, according to researchers, can be manipulated to transmit data over an air gap.
The attacker first needs to somehow plant a piece of malware on the air-gapped device from which they want to steal data. The Stuxnet attack and other incidents have shown that this task can be accomplished by a motivated attacker.
Once the malware is in place, it can collect small pieces of information, such as keystrokes, passwords and encryption keys, and send it to a nearby receiver.
The malware can manipulate the magnetic fields generated by the CPU by regulating its workload – for example, overloading the processor with calculations increases power consumption and generates a stronger magnetic field.
The collected data can be modulated using one of two schemes proposed by the researchers. Using on-off keying (OOK) modulation, an attacker can transmit “0” or “1” bits through the signal generated by the magnetic field – the presence of a signal represents a “1” bit and its absence a “0” bit.
Since the frequency of the signal can also be manipulated, the malware can use a specific frequency to transmit “1” bits and a different frequency to transmit “0” bits. This is known as binary frequency-shift keying (FSK) modulation.
Ben Gurion University researchers have developed two pieces of malware that rely on magnetic fields to exfiltrate data from an air-gapped device. One of them is called ODINI and it uses this method to transmit the data to a nearby magnetic sensor. The second piece of malware is named MAGNETO and it sends data to a smartphone, which typically have magnetometers for determining the device’s orientation.
In the case of ODINI, experts managed to achieve a maximum transfer rate of 40 bits/sec over a distance of 100 to 150 cm (3-5 feet). MAGNETO is less efficient, with a rate of only 0.2 - 5 bits/sec over a distance of up to 12.5 cm (5 inches). Since transmitting one character requires 8 bits, these methods can be efficient for stealing small pieces of sensitive information, such as passwords.
Researchers demonstrated that ODINI and MAGNETO also work if the targeted air-gapped device is inside a Faraday cage, an enclosure used to block electromagnetic fields, including Wi-Fi, Bluetooth, cellular and other wireless communications.
In the case of MAGNETO, the malware was able to transmit data even if the smartphone was placed inside a Faraday bag or if the phone was set to airplane mode.
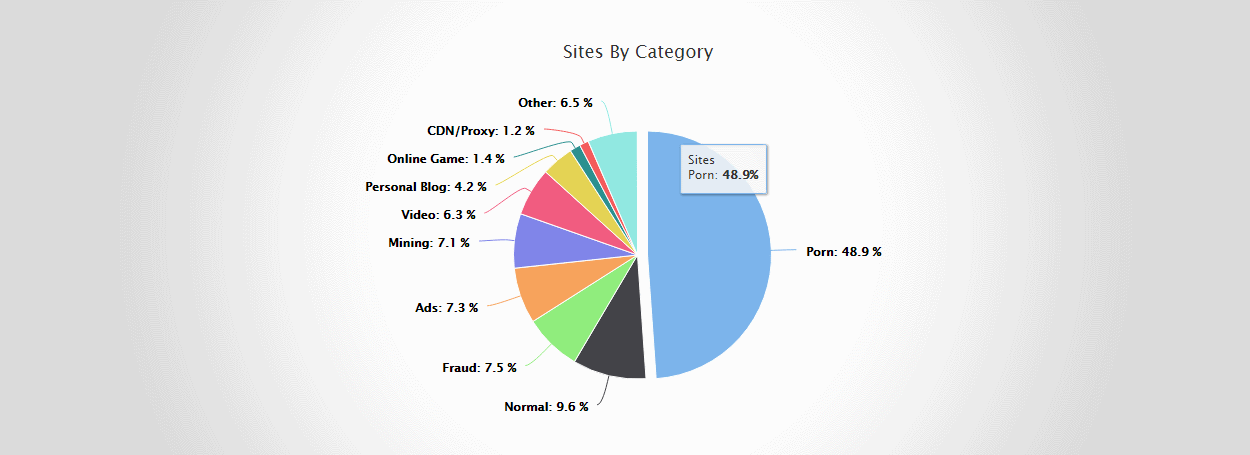
https://www.bleepingcomputer.com/ne...ll-cryptojacking-scripts-found-on-porn-sites/Almost 50% of all cryptojacking scripts (in-browser miners) are deployed on adult-themed sites, according to new numbers released this week by Qihoo 360's Netlab division.
Researchers gathered these numbers by using Netlab's DNSMon system, a tool that analyzes relations in DNS traffic between web domains.
DNSMon allowed researchers to analyze web traffic on the entire Internet level, and spot which sites loaded JavaScript code from domains known to offer in-browser mining services.
Pitäiskö valtiollisten taata sotilaille kaikkea pikkutuhmaa?
LULz
https://arstechnica.com/tech-policy...t-minting-blockchange-with-supercomputer/Russia's Interfax News Agency reports that engineers at the All-Russian Research Institute of Experimental Physics (RFNC-VNIIEF)—the Russian Federation Nuclear Center facility where scientists designed the Soviet Union's first nuclear bomb—have been arrested for mining cryptocurrency with "office computing resources," according to a spokesperson for the Institute. "There has been an unsanctioned attempt to use computer facilities for private purposes including so-called mining," said Tatyana Zalesskaya, head of the Institute's press service.
Zalesskaya did not say how many people were detained, and the Federal Security Service (FSB) has not issued a statement on the arrests or criminal charges pending. But reports indicate that the group was caught trying to harness the lab's supercomputer to mine cryptocurrency.
The Institute is located in Sarov, a "closed" city east of Moscow where nuclear weapons research has been conducted since 1946. The facility is so secret that it was left off Soviet maps; Sarov is surrounded by fences and guarded by the Russian military accordingly. While the city is the home of Russia's Nuclear Weapons Museum, don't plan a visit anytime soon—access to Sarov is restricted, and no one who does not live in the city is allowed to visit without permission. Foreigners visiting on official business have to surrender their passports, cell phones, and other electronic devices at the city's checkpoints.
Because of the nature of the work at the Institute, technically none of the Institute's computers—including its 1-petaflop capable supercomputer, used for simulating tests of nuclear weapons designs—is supposed to be connected to the Internet. According to the Russian news service Mash, someone at the Institute attempted to connect the supercomputer to the Internet, and that attempt was detected by the FSB, launching an investigation.
Cryptocurrency speculation and mining have generated so much interest in Russia that one businessman—Alexey Kolesnik—recently bought two power plants in the Russian republics of Perm Krai and Udmurtia to be used exclusively to generate electricity for Bitcoin-mining data centers. But there have been numerous other attempts recently in Russia to harness corporate and industrial computer systems for illicit cryptocurrency mining as well.
Zalesskaya told Interfax that a large number of companies "with large computing capacity" have recently experienced attempts to harness their computing infrastructure for cryptocurrency mining, but the PR rep told Interfax that these sorts of schemes "will be severely suppressed at our enterprises. This is technically a hopeless and criminal offense."
https://threatpost.com/olympic-dest...-olympics-cyberattack-researchers-say/129918/Winter Olympics officials have confirmed that a cyberattack occurred during the games’ opening ceremony on Feb. 9, but are remaining mum on the source of the attack. Researchers say the attack employed malware, dubbed Olympic Destroyer, that was written with the sole intention of destroying systems, not to steal data.
“Maintaining secure operations is our purpose,” said International Olympic Committee (IOC) spokesman Mark Adams,” told Reuters. “We are not going to comment on the issue. It is one we are dealing with. We are making sure our systems are secure and they are secure. ”
“The infection vector is currently unknown as we continue to investigate,” the researchers wrote.
“The samples identified, however, are not from adversaries looking for information from the games but instead they are aimed to disrupt the games. The samples analyzed appear to perform only destructive functionality. There does not appear to be any exfiltration of data.”
http://www.bbc.co.uk/news/uk-politics-43062113The Russian military was directly behind a "malicious" cyber-attack on Ukraine last summer that spread across Europe, British ministers have said.
The UK government has taken the unusual step of publicly accusing Russia of June's NotPetya ransomware attack.
Reckitt Benckiser - maker of Dettol, Durex and Strepsils - was among the UK firms whose sales were affected.
Defence Secretary Gavin Williamson said Russia was "ripping up the rule book" and the UK was duty-bound to respond.
Russia has denied responsibility for the NotPetya attack - which is estimated to have cost companies more than $1.2bn - and pointed out that Russian firms were among those whose systems were affected.
https://arstechnica.com/information...-hacked-to-run-cryptocurrency-mining-malware/Add Tesla to the legion of organizations that have been infected by cryptocurrency-mining malware.
In a report published Tuesday, researchers at security firm RedLock said hackers accessed one of Tesla's Amazon cloud accounts and used it to run currency-mining software. The researchers said the breach in many ways resembled compromises suffered by Gemalto, the world's biggest SIM card maker, and multinational insurance company Aviva. In October, RedLock said Amazon and Microsoft cloud accounts for both companies were breached to run currency-mining malware after hackers found access credentials that weren't properly secured.
The initial point of entry for the Tesla cloud breach, Tuesday's report said, was an unsecured administrative console for Kubernetes, an open source package used by companies to deploy and manage large numbers of cloud-based applications and resources.
"The hackers had infiltrated Tesla's Kubernetes console which was not password protected," RedLock researchers wrote. "Within one Kubernetes pod, access credentials were exposed to Tesla's AWS environment which contained an Amazon S3 (Amazon Simple Storage Service) bucket that had sensitive data such as telemetry."
The attackers hid the malware behind an IP address hosted by security firm Cloudflare. They also configured the mining software to use a non-standard port to reach the Internet and to connect to an unlisted or semi-public endpoint rather than well-known mining pools. The attackers also likely ratcheted down the amount of CPU resources used to mine the digital coin. The measures helped to make the illicit mining harder to detect and lower the chances of it being shut down.
http://www.theregister.co.uk/2018/0...erds_australia_wants_plaintext_under_warrant/Australia's home affairs minister Peter Dutton has waded into the global crypto debate, uttering the familiar demand that the tech sector provide what the politicians want while adding that the government will protect Australians from cyber-threats.
Dutton on Wednesday told Australia's National Press Club today that “ubiquitous encryption, a vital tool to all of us for secure personal banking and other communications including messaging, has become a significant obstacle to terrorism investigations.”
Because “decryption takes time” (if a platform is using a modern algorithm, you might get a plaintext while the universe is still warm), the industry needs to make message recovery as trivial as a phone tap.
“Law enforcement access to encrypted communications should be on the same basis as telephone and other intercepts in which companies provide vital and willing assistance in response to court orders.“, Dutton said.
So the Australian government doesn't want the impossible to be routine, instead asking for it only if a warrant can be produced. And the government will pass laws to ensure that the magical comes true:
“The Government is willing to work closely with these firms but will also introduce legislation to ensure that companies providing communications, services and devices in Australia have an obligation to assist agencies with decryption and, as a society, we should hold these companies responsible when their service is used to plan or facilitate unlawful activity”
If this sounds familiar, it's because others among the “Five Eyes” group of intelligence-sharing nations (USA, UK, NZ and Canada) seem to have obtained the same song sheet. At the end of January, UK Prime Minister Theresa May made a very similar call; and magic reversible-by-cops-encryption has been on the US agenda so long, a bunch of experts last week demanded the FBI reveal who's been telling it the magic is possible.
http://www.wired.co.uk/article/gchq-uk-robert-hannigan-cyberwar-definitionThere should be an international treaty on cyberwarfare that sets clear boundaries for nation states around hacking computer infrastructure, the former director of GCHQ has said.
In a wide-ranging interview, Robert Hannigan spelled-out the growing threats cyberwarfare, Russia, and artificial intelligence pose as well as calling for tighter regulation. "We should be looking at some kind of arms control for cyberspace," says Hannigan, who left GCHQ last year. "We do need to come to some kind of international agreement about what's acceptable and what isn't".
How this would work, though, is a difficult proposition. Put simply: no straightforward solution to cyberwarfare and offensive hacking campaigns by countries exists – and coming up with one is no easy task.
Viimeksi muokattu:
Ensimmäinen advanced threat valtiollinen ryhmä
https://www.wired.com/story/north-korean-hacker-group-apt37/North Korea's most prolific hacking group, broadly known within the security community under the name Lazarus, has over the last half-decade proven itself one of the world's most internationally aggressive teams of intruders. It has pulled off audacious attacks around the globe, from leaking and destroying Sony Pictures' data to siphoning of tens of millions of dollars from banks in Poland and Bangladesh. Now, security researchers have detailed the capabilities of a far more obscure North Korean group, with its own distinct and diverse hacking arsenal.
Tuesday, security firm FireEye released a new report describing a group of sophisticated state-sponsored hackers it calls APT37—also known by the names ScarCruft and Group123—that it has followed for the last three years, tracing the operation to North Korea. The company notes that the hackers have, for the most part, remained focused on South Korea targets, which has allowed the team to keep a far lower profile than Lazarus. But FireEye says APT37 isn't necessarily any less skillful or well-resourced. It has used a broad range of penetration techniques, and has planted custom-coded malware on victims' computers capable of everything from eavesdropping via an infected PC's microphone to Sony-style data-wiping attacks.
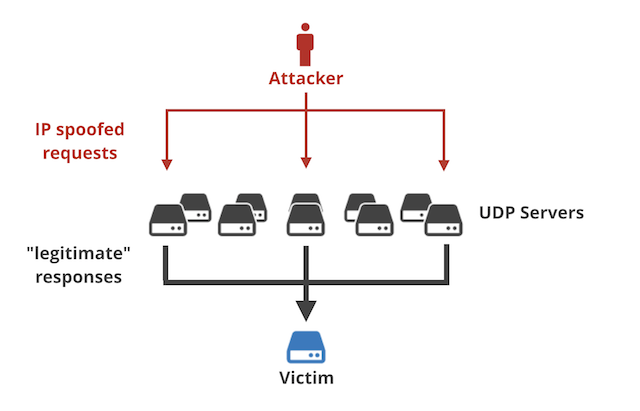
https://arstechnica.com/information...ses-use-new-way-to-achieve-unthinkable-sizes/Hackers have found a way to amplify distributed denial-of-service attacks by an unprecedented 51,000 times their original strength in a development that whitehats say could lead to new record-setting assaults that take out websites and Internet infrastructure.
DDoS vandals have long intensified their attacks by sending a small number of specially designed data packets to publicly available services. The services then unwittingly respond by sending a much larger number of unwanted packets to a target. The best known vectors for these DDoS amplification attacks are poorly secured domain name system resolution servers, which magnify volumes by as much as 50 fold, and network time protocol, which increases volumes by about 58 times.
http://www.theregister.co.uk/2018/02/28/memcached_reflected_dos_attacks/Attackers have discovered a new amplified denial-of-service attack vector, and have launched attacks reaching hundreds of gigabits per second in Asia, North America and Europe.
Former Internet Systems Consortium CEO and now Akamai principal architect Barry Raveendran Greene has detailed the reflected DOS attack on his blog and explained it can make it look like the incoming traffic comes from a service provider's router.
The attack abuses the memcached distributed in-memory caching utility, used to speed up dynamic Web applications by sharing around the database load.
The utility isn't meant to be installed on Internet-facing systems, because it has no security mechanism, but as SANS, Cloudflare, Arbor Networks and Akamai have all observed, there are a lot of memcached exposed instances out there.
As SANS' Johannes Ulrich wrote: “Apparently people are exposing memcached to the internet. For many other services, I would qualify that statement: 'without access control'. But for memcached there is no access control. This is by design.”
The mechanism attackers have used was to send memcached instances a request for statistics over UDP, apparently coming from the spoofed victim's IP address. The stats request is 15 bytes long, but the reply is between 1,500 bytes up to hundreds of kilobytes.
There's the amplification factor: 15-byte requests sent to a bunch of memcached instances, and the target is hosed.
Qrator Labs reckons it's seen attacks reach 500 Gbps.
If you're under attack, there are two things to do: block all traffic from port 11211, and if you can, get help from your ISP to block the traffic.
Operators are being asked to help block the attacks as well. A note to Australian Network Operators' Group (AUSNOG) suggests implementing Exploitable Port Filters as per these instructions.
And if you're a sysadmin whose memcached server is outside the firewall, get it inside, configure it so it doesn't listen on UDP, and strap yourself to the butt-kicking machine, because as Ulrich pointed out, the utility's config file told you not to put it on the Internet.
Viimeksi muokattu:
Valtiollinen, tällä kertaa naapuri Saksassa kylässä.
https://www.wsj.com/articles/german-says-government-network-was-breached-1519840559German authorities said on Wednesday they were investigating a security breach of the government's highly protected computer network. The country's intelligence agencies were examining attacks on more than one government ministry, the interior ministry said, adding that the affected departments had been informed and that the attack had been isolated and brought under control. Earlier on Wednesday, the German news agency DPA reported that German security services had discovered a breach of the government's IT network in December and traced it back to state-sponsored Russian hackers. German companies have been the target of sustained attacks by state-sponsored hackers, mainly believed to be Chinese. In 2015, the Bundestag, parliament's lower house, suffered a extensive breach, leading to the theft of several gigabytes of data by what German security officials believe were Russian cyberthieves. Hackers believed to be part of the Russia-linked APT28 group sought to infiltrate the computer systems of several German political parties in 2016, Germany's domestic intelligence agency said in 2016.
http://www.theregister.co.uk/2018/0...ckers_blitzkrieged_its_servers_to_steal_data/The German Interior ministry has confirmed that it has identified a serious attack against its servers, amidst reports that the culprits were the Russian APT28 – aka Fancy Bear – hacking group.
On Wednesday local news site DPA International reported that the German government discovered a serious intrusion into its servers in December 2017. The attack is thought to have seen data exfiltrated for up to a year before its discovery.
Johannes Dimroth, a spokesman for the ministry, confirmed that "government information technology and networks," had been affected by an intrusion. "The incident is being treated as a high priority and with substantial resources," he said.
Fancy Bear has been active for at least a decade. Its activities have often non-Russian government targets. The group was fingered for the Democratic National Committee hack ahead of the 2017 US Presidential election, attacks during the 2017 French election, brazen rummaging in Finnish security forces' servers and even attacks on the sports doping authorities.
In December 2016 Germany's Federal Office for the Protection of the Constitution took the unusual step of issuing a public warning about hacking ahead of national elections in September 2017. That warning named Russia as the likely culprit.
Russia has always denied that it has anything to do with Fancy Bear, but the types of malware used, the software and coding styles, and its choice of targets suggest that Putin and his pals might have Fancy Bear dancing to their tune.
This latest attack on Germany will not serve to warm relations between these two historical enemies. With Russia looking to take an increasingly muscular role in European affairs, hopefully such conflicts will not leave the online realm
Viimeksi muokattu:
http://www.theregister.co.uk/2018/0..._oversight_of_uks_mass_comms_data_collection/Privacy International has slammed the UK's spy agencies for failing to keep a proper paper trail over what data telcos were asked to provide under snooping laws, following its first ever cross-examination of a GCHQ witness.
The campaign group was granted the right to grill GCHQ's star witness after he made a series of errors in previous statements submitted to the Investigatory Powers Tribunal (IPT). The evidence was part of a long-running challenge over the spy agency's collection of bulk communications and personal data.
Although the witness's most recent errors related to submissions made at an October 2017 hearing about how much access IT contractors employed by GCHQ have to data, much of the cross-examination aimed to unpick GCHQ's role in choosing what information telcos hand over.
Under section 94 of the Telecommunications Act, communications service providers and public electronic communications networks can be asked to provide the UK's spy agencies with bulk communication data on users' phone and internet records.
The use of s94 directions only became public knowledge in 2015, when the government introduced its so-called Snooper's Charter and admitted that such collection had been going on since 1998. Privacy International launched a legal challenge against the government and, in 2016, the IPT ruled the activity illegal for the time it was carried out under wraps.
Since then, the tribunal has been ploughing through related issues arising from the case, as Privacy International pushes to uncover more detail about how the s94 directions work, with GCHQ providing much of its evidence through one key witness.
Witness X, as he is known – he has been granted anonymity and speaks from behind a screen – was the deputy director for mission policy at the Cheltenham-based agency for about three years up until last month.
Throughout the case, he has given evidence and submitted multiple statements on behalf of GCHQ to the tribunal. However, Witness X has had to amend his statements a number of times, and following the most recent correction Privacy International was granted permission to cross-examine him.
During the two-hour hearing this week, Thomas de la Mare, acting for Privacy International, unpicked Witness X's statements in granular detail, pressing for precise explanations on how GCHQ worked with service providers, how providers were issued with demands for information and how detailed those requests were.
No voi hyvää päivää. Tätä olen odottanut yli kymmenen vuotta. En usko että IBMllä menee paljon paremmin tämän asian kanssa, mutta jos ajattelen tätä valtiollisen työkalupakissa, niin kyky sulkea adminit pois palvelimista on kiva lahja. Kiitos HP.
https://threatpost.com/bug-in-hp-remote-management-tool-leaves-servers-open-to-attack/130189/Hewlett Packard Enterprise has patched a vulnerability in its remote management hardware called Integrated Lights-Out 3 that is used in its popular line of HP ProLiant servers. The bug allows an attacker to launch an unauthenticated remote denial of service attack that could contribute to a crippling on vulnerable datacenters under some conditions.
The vulnerability (CVE-2017-8987) is rated “high severity”, with a CVSS base score of 8.6, and was discovered by Rapid7 researchers in September. HPE publicly reported the bug on Feb. 22 and has made patches available.
Affected is the v1.88 firmware for HPE’s Integrated Lights-Out 3 (iLO3). Not impacted are newer versions of the firmware (1.8, 1.82, 1.85, and 1.87) along with firmware for iLO4 (v2.55). iLO5 devices were not tested, according to a Rapid7 technical brief on the vulnerability written by Sam Huckins, the company’s program manager.
The Hewlett-Packard iLO is an embedded server management technology for ProLiant servers that consists of a physical card with a separate network connection. It allows system administrators to remotely manage servers.
“An attacker who has already compromised a network can now can easily lock out an admin from fixing or mitigating against an attack,” said Tod Beardsley, Rapid7’s research director. “An attacker can use this to make a data center go dark and keep it that way by locking out remote management and mitigation.” Alternatively, system administrators will have to tackle on-premises fixes.
According to Beardsley, an attacker sharing the same network as a vulnerable iLO3 can simply send several HTTP requests and cause the iLO3 device (running firmware v1.88) to stop responding for up to 10 minutes.
One of those examples includes using a Secure Socket Shell where an “open sessions will become unresponsive; new SSH sessions will not be established.” In another scenario with a web portal “users cannot log into the web portal; the login page will not successfully load,” according to Rapid7.
Where as HTTP GET and POST requests are benign, curl -X OPTIONS request to an iLO3 device can trigger the DoS condition. “Any method requested other than GET or POST will trigger the DoS, even invalid ones,” Beardsley wrote. “Ten minutes after the DoS is triggered, the watchdog (automatic system recovery) service restarts the device.”
“An attack doesn’t require authentication. The device itself requires some kind of authentication, such as a web portal that you use to like login. But this attack comes in before that. The attack is literally just an HTTP command,” Beardsley said.
According to Rapid7, HP’s Integrated Lights-Out is not on by default, which likely disqualifies many ProLiant from the vulnerability.

https://www.wired.com/story/github-ddos-memcached/ampWednesday's onslaught wasn't the first time a major DDoS attack targeted GitHub. The platform faced a six-day barrage in March 2015, possibly perpetrated by Chinese state-sponsored hackers. The attack was impressive for 2015, but DDoS techniques and platforms—particularly Internet of Things–powered botnet - have evolved and grown increasingly powerful when they’re at their peak. To attackers, though, the beauty of memcached DDoS attacks is there's no malware to distribute, and no botnet to maintain.
