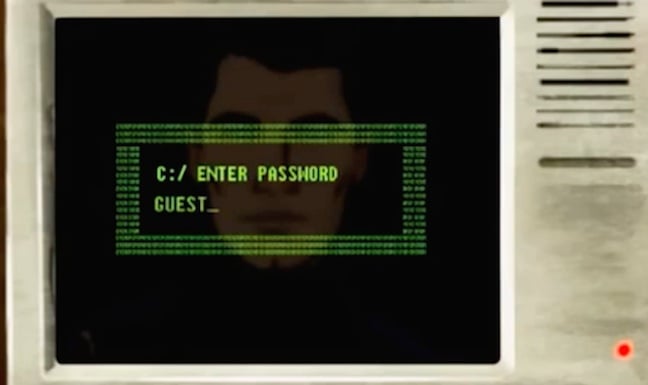
The US government's Computer Emergency Response Team (US-Cert) has posted a new report on the latest exploits of North Korea's Hidden Cobra hacking crews.
The updated advisory (PDF) details how the hacking groups believed to operate on behalf of the isolated government, have carried out various hacking operations in recent years in an effort to drum up cash for the sanctions-hit regime. There's currently up to $5m up for grabs for catching North Korean miscreants.
Among the claims in the report are that DPRK hackers (US-Cert uses Hidden Cobra as the catch-all name) have started strong-arming companies into paying them off for "protection" and have also loaned their services out to other hacking crews.
"DPRK cyber actors have also conducted extortion campaigns against third-country entities by compromising an entity’s network and threatening to shut it down unless the entity pays a ransom," US-Cert notes.
"In some instances, DPRK cyber actors have demanded payment from victims under the guise of long-term paid consulting arrangements in order to ensure that no such future malicious cyber activity takes place. DPRK cyber actors have also been paid to hack websites and extort targets for third-party clients."
US-Cert also notes a number of recent reports on the group, including the 2019 UN Panel of Experts report that determined the hacking crew had probably generated something in the range of $2bn for the despotic regime since it first emerged back in 2014 with the hack of Sony.
That crew, known as Lazarus Group, was also blamed for the Wannacry 2.0 malware and the $81m theft from a bank in Bangladesh.
Mentioned in that UN report and highlighted by US-Cert, was a more recent move into cryptojacking, as the crews have used their sizable malware arsenal to start targeting cryptocurrency wallets or using the compute cycles on infected machines to generate new coins.
"The [UN report] has identified several incidents in which computers infected with cryptojacking malware sent the mined assets – much of it anonymity enhanced digital currency (sometimes also referred to as “privacy coins”) – to servers located in the DPRK, including at Kim Il Sung University in Pyongyang," US-Cert reported.
So what's the point of all this? Well, other than to remind businesses that Hidden Cobra is still out there and posing a threat to both private and public-sector companies, US-Cert wanted to let people know that there remains a massive bounty on members of the hacking crew.
"If you have information about illicit DPRK activities in cyberspace, including past or ongoing operations, providing such information through the Department of State’s Rewards for Justice program could make you eligible to receive an award of up to $5 million."
So, if you're out of work and up for a bit of sleuthing to pass the time during the lockdown, there is plenty of cash to be had.

Stuck inside with time on your hands? The US govt would like to remind you it's paying $5m for Nork hacking scalps
US-Cert issues new report on misdeeds of North Korean groups