https://threatpost.com/eu-authorities-crack-encryption-murder-network/157146/Four-year investigation shuts down EncroChat and busts 746 alleged criminals for planning murders, selling drugs and laundering money.
European law-enforcement officials have shut down an encrypted Android-based communications platform used exclusively by criminals to plot murders, traffic illegal drugs, commit money laundering and plan other organized crimes.
An international law-enforcement team from the France and the Netherlands cracked the encryption of EncroChat, a secure mobile messaging service that was “one of the largest providers of encrypted communications,” according to the U.K.’s National Crime Agency (NCA).
U.K. officials had been investigating the platform and nefarious activities of the criminals using it since 2016 through Operation Venetic, working alongside international law-enforcement agencies to share technical expertise and intelligence.
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
Kalliiksi käy jos noin paljon pitää Britissä leikata kyberin edestä.
"Draft plans suggest a significant chunk of the Royal Marines’ capability could be axed, including its artillery, engineers and landing craft." HUHHUH!
Access Restricted
www.telegraph.co.uk
"Draft plans suggest a significant chunk of the Royal Marines’ capability could be axed, including its artillery, engineers and landing craft." HUHHUH!
Viimeksi muokattu:
"Draft plans suggest a significant chunk of the Royal Marines’ capability could be axed, including its artillery, engineers and landing craft."
"Mandarins have suggested the scrapping of RAF air bases and a fleet of Hercules planes and Puma helicopters."
Nuo ei ole sitten Rajalle sopivia Super Pumia vaan jotain ikäloppua, joka olisi viimeisellä puolivuosikymmenyksellä muutenkin.

 en.wikipedia.org
en.wikipedia.org
Eiköhän vielä sieltä jotain Shadow R1 tapaista löydy vaihtoehdoiksi/lisäksi leikkuriin.
Tehneekö Royalien tykeillä mitään? Tuskin aluksia tarvitaan.
"Mandarins have suggested the scrapping of RAF air bases and a fleet of Hercules planes and Puma helicopters."
Nuo ei ole sitten Rajalle sopivia Super Pumia vaan jotain ikäloppua, joka olisi viimeisellä puolivuosikymmenyksellä muutenkin.

Aérospatiale SA 330 Puma - Wikipedia
Eiköhän vielä sieltä jotain Shadow R1 tapaista löydy vaihtoehdoiksi/lisäksi leikkuriin.
Tehneekö Royalien tykeillä mitään? Tuskin aluksia tarvitaan.
US president Donald Trump has revealed that in 2018 he authorized an attack on suspected-to-be-state-sponsored Russian internet trolls intent on disrupting the electoral process during Congressional elections.
In an interview with The Washington Post Trump claimed credit for a previously-reported but never-before-confirmed attack on the Internet Research Agency, the allegedly Moscow-controlled outfit that the Mueller Report found conducted a massive disinformation campaign ahead of the 2016 presidential election.
Trump’s remarks to the Post were thin but seemingly substantiate other statements in which he has said the USA was aware of the 2016 misinformation campaign and had resolved to prevent a recurrence.
Trump has repeatedly stated a preference for being friendly to Russia to bring it into the fold, a stance that has seen him criticised for being inexplicably soft on an adversary. Revealing an attack addresses such criticism. It also gives Russia two things it’s always hard to find after a cyber-attack: certainty of attribution, and therefore a chance to observe the techniques used in the hope of better understanding US offensive capabilities and tradecraft.
Admitting to the strike also runs counter to Trump’s oft-stated position that his own brilliance was the reason for his election win, rather than outside influence. Taking on a troll farm to secure an election suggests Russia has real muscle.

Trump reveals US cyber-attack on Russian election-misdirection troll farms
Maybe Donald isn’t in love with Vlad after all – but he did just give Russia attribution and maybe a peek at tradecraft
The CIA is running a secret cyberwar including Russian-style hack-and-leak operations with little or no oversight, US officials have warned.
The covert operations are largely targeted at Iran, China, Russia, and North Korea, say anonymous sources, and have included the public disclosure of 15 million debit card details belonging to customers of Iranian banks, according to a report by Yahoo! News.
The approval for the operations stems from a National Security Presidential Memorandum (NSPM) signed in 2018 by President Trump which has long been known about but the contents of which remain top secret. It has been officially described as authorizing “offensive cyber operations.”

Report: CIA runs secret cyberwar with little oversight after Trump gave the OK, say US government officials
Details start to emerge on real-world impact of Prez-signed secret memo
Malicious actors are abusing the secondary market for IPv4 addresses, according to Lancaster University lecturer Vasileios Giotsas, University College London research and teaching assistant and postdoctoral fellow Ioana Livadariu from Norway's Simula Metropolitan Center for Digital Engineering.
In a recent paper titled A first look at the misuse and abuse of the IPv4 Transfer Market [PDF], the three explain how IP address depletion saw regional internet registries establish transfer markets for the increasingly-hard-to-find IPv4 addresses.
“However, the IPv4 market has been poorly regulated due to the lack of widely adopted IP prefix ownership authentication mechanisms, inconsistent contractual requirements between legacy and allocated address space, and policy incongruences among Regional Internet Registries (RIRs),” the trio wrote. “As a result, IPv4 transfers have become target of fraud and abuse by malefactors who try to bypass legal IP ownership processes.”
Those who abuse the process do things like using “clean” IP addresses from which to host botnets or fraudulent sites.
The authors explain that he was able to access data about address transfers from internet registries, map the address ranges against known autonomous system numbers (AS numbers), correlate all of that with border gateway protocol activity and eventually create a picture of what happens to IPv4 addresses after they are bought and sold.
The paper's conclusions are not pretty: “We find that for more than 65 percent of the IP transfers, the origin ASes and the transaction dates appear to be inconsistent with the transfer reports, while six percent of Route Origin Authorizations (ROAs) become stale after the transfer for many months.”
“Our results reveal at best poor practices of resource management that can facilitate malicious activities, such as hijacking attacks, and even lead to connectivity issues due to the increasing deployment of RPKI-based or IRR-based filtering mechanisms.”
It gets worse: “ASes involved in the transfer market exhibit consistently higher malicious behavior compared to the rest of the ASes, even when we account for factors such as business models and network span,” the three authors said, adding “Our findings are likely to be a lower bound of malicious activity from within transferred IP addresses since a number of transactions may occur without being reported to the regional internet registries.”

Networking boffins detect wide abuse of IPv4 addresses bought on secondary market
Suggests poorly-regulated address-marts are favorites of folks who want ‘clean’ addresses that give botnets a break
More than 1,000 unsecured databases so far have been permanently deleted in an ongoing attack that leaves the word “meow” as its only calling card, according to Internet searches over the past day.
The attack first came to the attention of researcher Bob Diachenko on Tuesday, when he discovered a database that stored user details of the UFO VPN had been destroyed. UFO VPN had already been in the news that day because the world-readable database exposed a wealth of sensitive user information, including:
- Account passwords in plain text
- VPN session secrets and tokens
- IP addresses of both user devices and the VPN servers they connected to
- Connection timestamps
- Geo-tags
- Device and OS characteristics
- Apparent domains from which advertisements are injected into free users’ Web browsers
Besides amounting to a serious privacy breach, the database was at odds with the Hong Kong-based UFO’s promise to keep no logs. The VPN provider responded by moving the database to a different location but once again failed to secure it properly. Shortly after, the Meow attack wiped it out.
Representatives of UFO didn’t immediately respond to an email seeking comment.
Since then, Meow and a similar attack have destroyed more than 1,000 other databases. At the time this post went live, the Shodan computer search site showed that 987 ElasticSearch and 70 MongoDB instances had been nuked by Meow. A separate, less-malicious attack tagged an additional 616 ElasticSearch, MongoDB, and Cassandra files with the string “university_cybersec_experiment.” That attackers in this case seem to be demonstrating to the database maintainers that the files are vulnerable to being viewed or deleted.

Ongoing Meow attack has nuked >1,000 databases without telling anyone why
Ongoing attack hitting unsecured data leaves the word "meow" as its calling card.
Amerikkalainen elektroniikkafirma Garmin ilmeisesti laajan hakkerointi & kiristyshyökkäyksen kohteena. Firmahan on todella suosittu kuluttajatuotteiden tekijä erilaisten kannettavien tai puettavien laitteiden (wearabless) parissa Suomessakin.
Lähde: https://teknavi.fi/elektroniikka/ki...arminin-laitteiden-synkronoinnin-ja-tuotannon
" Kiristäjät lamauttivat Garminin laitteiden synkronoinnin ja tuotannon
Julkaistu 24.7.2020
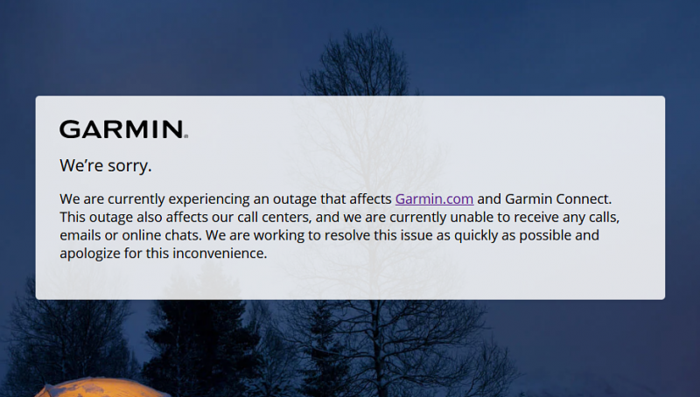
Kiristäjät ovat saaneet Garminin palvelut polvilleen, ZDNet kertoo. Jopa älykellovalmistajan tuotantolinjastoja on jouduttu sulkemaan.
MÄlykellovalmistaja Garmin on joutunut kiristyshyökkäyksen kohteeksi. Hakkerit ovat lamauttaneet Garminin palveluita, kuten Garmin Connectin ja flyGarminin, ja älykellovalmistaja on joutunut Twitterissä ilmoittamaan usean vuorokauden huoltokatkosta.
Myös asiakaspalvelulinjat ovat kaatuneet, ja mikä erikoisinta, tilanne vaikuttaa taiwanilaisen iThome-sivuston mukaan jopa tuotantolinjastoihin, jotka on Taiwanissa suljettu kahdeksi vuorokaudeksi. Työntekijöille on tiedotettu, että sulun taustalla on ”virus”, mikä viitannee tässä tapauksessa kiristyksessä käytettyyn haittaohjelmaan.
Garmin ei virallisesti ole vahvistanut, että kyseessä on kiristyshyökkäys. Se kertoo tutkivansa tilannetta, mutta yhtiön työntekijät ovat jo paljastaneet Garminin joutuneen kiristyksen kohteeksi.
Käyttäjille tilanne näkyy siten, että Garmin Connect -älypuhelinsovellus ja -verkkopalvelu eivät toimi, eikä asiakaspalveluun saa yhteyttä puhelimitse tai sähköpostitse. Myös lentäjien suosima flyGarmin-palvelu on nyt väliaikaisesti pois käytöstä, mikä on aiheuttanut harmia monille amatööripiloteille."
Lähde: https://teknavi.fi/elektroniikka/ki...arminin-laitteiden-synkronoinnin-ja-tuotannon
" Kiristäjät lamauttivat Garminin laitteiden synkronoinnin ja tuotannon
Julkaistu 24.7.2020

Kiristäjät ovat saaneet Garminin palvelut polvilleen, ZDNet kertoo. Jopa älykellovalmistajan tuotantolinjastoja on jouduttu sulkemaan.
MÄlykellovalmistaja Garmin on joutunut kiristyshyökkäyksen kohteeksi. Hakkerit ovat lamauttaneet Garminin palveluita, kuten Garmin Connectin ja flyGarminin, ja älykellovalmistaja on joutunut Twitterissä ilmoittamaan usean vuorokauden huoltokatkosta.
Myös asiakaspalvelulinjat ovat kaatuneet, ja mikä erikoisinta, tilanne vaikuttaa taiwanilaisen iThome-sivuston mukaan jopa tuotantolinjastoihin, jotka on Taiwanissa suljettu kahdeksi vuorokaudeksi. Työntekijöille on tiedotettu, että sulun taustalla on ”virus”, mikä viitannee tässä tapauksessa kiristyksessä käytettyyn haittaohjelmaan.
Garmin ei virallisesti ole vahvistanut, että kyseessä on kiristyshyökkäys. Se kertoo tutkivansa tilannetta, mutta yhtiön työntekijät ovat jo paljastaneet Garminin joutuneen kiristyksen kohteeksi.
Käyttäjille tilanne näkyy siten, että Garmin Connect -älypuhelinsovellus ja -verkkopalvelu eivät toimi, eikä asiakaspalveluun saa yhteyttä puhelimitse tai sähköpostitse. Myös lentäjien suosima flyGarmin-palvelu on nyt väliaikaisesti pois käytöstä, mikä on aiheuttanut harmia monille amatööripiloteille."

5 miljoonaa taalaa
A ransomware attack that took the GPS and smartwatch business Garmin entirely offline for more than three days is believed to have been carried out by a Russian cybercriminal gang which calls itself “Evil Corp”.
Garmin began to restore services to customers on Monday morning, after being held hostage for a reported ransom of $10m, although some services were still operating with limited functionality.
The hack is thought to be just the latest in a long string of attacks on American companies that have earned the cybercriminals’ alleged leader, Maksim Viktorovich Yakubets, 33, a $5m bounty on his head from the FBI. That reward is the highest ever offered for a cybercriminal.
Unlike those behind some previous high-profile ransomware outbreaks, such as the notorious WannaCry and NotPetya campaigns of 2017, Evil Corp has historically been very focused in how it picks and attacks its targets. Rather than going after end users and small businesses, who may be easy to trick into opening a malicious email attachment but unlikely to pay significant ransoms for their data, the organisation has instead deployed a mixture of technical prowess and social engineering to attack sizeable targets such as banks, media organisations and now technology companies.

Ransomware attack on Garmin thought to be the work of 'Evil Corp'
Russian cybercrime gang is believed to be responsible for taking Garmin services offline
Over the past few years, online disinformation has taken evolutionary leaps forward, with the Internet Research Agency pumping out artificial outrage on social media and hackers leaking documents—both real and fabricated—to suit their narrative. More recently, Eastern Europe has faced a broad campaign that takes fake news ops to yet another level: hacking legitimate news sites to plant fake stories, then hurriedly amplifying them on social media before they’re taken down.
On Wednesday, security firm FireEye released a report on a disinformation-focused group it’s calling Ghostwriter. The propagandists have created and disseminated disinformation since at least March 2017, with a focus on undermining NATO and the US troops in Poland and the Baltics; they’ve posted fake content on everything from social media to pro-Russian news websites. In some cases, FireEye says, Ghostwriter has deployed a bolder tactic: hacking the content management systems of news websites to post their own stories. They then disseminate their literal fake news with spoofed emails, social media, and even op-eds the propagandists write on other sites that accept user-generated content.
That hacking campaign, targeting media sites from Poland to Lithuania, has spread false stories about US military aggression, NATO soldiers spreading coronavirus, NATO planning a full-on invasion of Belarus, and more. “They’re spreading these stories that NATO is a danger, that they resent the locals, that they’re infected, that they’re car thieves,” says John Hultquist, director of intelligence at FireEye. “And they’re pushing these stories out with a variety of means, the most interesting of which is hacking local media websites and planting them. These fictional stories are suddenly bona fide by the sites that they’re on, and then they go in and spread the link to the story.”

Hackers Broke Into Real News Sites to Plant Fake Stories
A disinfo operation broke into the content management systems of Eastern European media outlets in a campaign to spread misinformation about NATO.
Chinese hackers infiltrated the Vatican's computer networks in the past three months , a private monitoring group has concluded, in an apparent espionage effort before the beginning of sensitive negotiations with Beijing. The attack was detected by Recorded Future, a firm based in Somerville, Mass. The Chinese Communist Party has been waging a broad campaign to tighten its grip on religious groups, in what government leaders have periodically referred to as an effort to "Sinicize religions" in the country.
China officially recognizes five religions, including Catholicism, but the authorities often suspect religious groups and worshipers of undermining the control of the Communist Party and the state, and of threatening the country's national security. Chinese hackers and state authorities have often used cyberattacks to try to gather information on groups of Buddhist Tibetans, Muslim Uighurs and Falun Gong practitioners outside China. But this appears to be the first time that hackers, presumed by cybersecurity experts at Recorded Future to be working for the Chinese state, have been publicly caught directly hacking into the Vatican and the Holy See's Study Mission to China, the Hong Kong-based group of de facto Vatican representatives who have played a role in negotiating the Catholic Church's status. The Vatican and Beijing are expected to start talks in September over control of the appointment of bishops and the status of houses of worship as part of a renewal of a provisional agreement signed in 2018 that revised the terms of the Catholic Church's operations in China.

The Vatican Is Said To Be Hacked From China Before Talks With Beijing - Slashdot
An anonymous reader quotes a report from The New York Times: Chinese hackers infiltrated the Vatican's computer networks in the past three months , a private monitoring group has concluded, in an apparent espionage effort before the beginning of sensitive negotiations with Beijing. The attack...
it.slashdot.org
Writing a successful Windows rootkit is easier than you would think. All you need is do is learn assembly and C/C++ programming, plus exploit development, reverse engineering, and Windows internals, and then find and abuse a buggy driver, and inject and install your rootkit, and bam. Happy days.
So you've decided you want to write a Windows rootkit. Good thing this chap's just demystified it in a talk
Demirkapi shows how drivers can be misused for deep pwnage
FYI, if you didn't already know: readily available satellite TV electronics can be used to sniff and inspect satellite internet traffic.
That's according to a team lead by University of Oxford PhD student (and occasional GDPR exploiter) James Pavur, who presented his crew's findings on the matter at this year's remote edition of the DEF CON hacking conference. See below for the presentation in full.

How did you spend your time at university? Pizza, booze, sleeping? This Oxford student is snooping on satellites
Bug-hunter details how his team slurped data… IN SPAAAAACE
The North Korean-linked APT’s latest campaign shows that it is shifting focus to target the cryptocurrency and financial verticals.
The nation-state threat operator Lazarus Group is being tied to a recent phishing campaign that targeted admins at a cryptocurrency firm via LinkedIn messages.
Researchers say that the recently identified a series of incident that were part of a broader campaign targeting businesses worldwide through LinkedIn messages sent to targets’ personal LinkedIn accounts. The goal of the campaign appears to be financially motivated, with the attackers harvesting credentials necessary for accessing cryptocurrency wallets or online bank accounts.
“Lazarus Group’s activities are a continued threat: the phishing campaign associated with this attack has been observed continuing into 2020, raising the need for awareness and ongoing vigilance amongst organizations operating in the targeted verticals,” said researchers with F-Secure in a Tuesday post [PDF].

Lazarus Group Targets Cryptocurrency Firms Via LinkedIn Messages
The North Korean-linked APT's latest campaign shows that it is shifting focus to target the cryptocurrency and financial verticals.
Tulevan koronaseuranta-apllikaation lähdekoodi on julkaistu:

 www.solita.fi
www.solita.fi
Simpauttaja

THL ja Solita julkaisivat Koronavilkun lähdekoodin – avoin koodi mahdollistaa sovelluksen riippumattoman arvioinnin - Solita
THL ja ohjelmistoyhtiö Solita ovat julkaisseet Koronavilkku-sovelluksen lähdekoodin. Tämä mahdollistaa järjestelmän toiminnan ja turvallisuuden riippumattoman arvioinnin sekä lähdekoodin hyödyntämisen.
Simpauttaja
North Korean government hackers dubbed the BeagleBoyz are trying to electronically rob banks, the United States warned this week.
Operating under the umbrella of Pyongyang's cyber-spy efforts dubbed HIDDEN COBRA by Uncle Sam, the gang compromises and hijacks SWIFT terminals used by banks to transfer large sums of money among one another. The crew is believed to have been behind attempts to steal as much as $2bn from banks around the world using this method. Many of the attempted heists are spotted and stopped before they complete, though, and only a few seemingly succeed.
In one such successful instance, they swiped $81m from the Bank of Bangladesh in 2016, a theft previously attributed to North Korea. According to the US government, BeagleBoyz "use unwitting banks, including banks in the United States, for their SWIFT fraud scheme. These banks are custodians of accounts belonging to victim banks or unknowingly serve as a pass-through for the fraud."
The hackers also like to make ATMs pay out free money, known as cash outs: "Fraudulent ATM cash outs have affected upwards of 30 countries in a single incident. The conspirators have withdrawn cash from ATM machines operated by various unwitting banks in multiple countries, including in the United States."

BeagleBoyz: 2020's hottest country-rap band, or N. Korea hackers stealing millions. Only one way to find out...
...read the article, of course
Kiinalaiset henkiltietoja keräämässä:

 www.hs.fi
www.hs.fi

Kiina | Kiinalaisyritys keräsi 2,4 miljoonan ihmisen tietokannan – HS:n näkemässä vuodetussa aineistossa on myös satoja suomalaisnimiä, kuten poliitikkojen lapsia
Kiinalaisyritys Zhenhua Data keräsi kaikkialta maailmasta tietokantaa vallan verkostoista. Tietokannassa on ainakin 800 suomalaisnimeä – ja kuva ”Tiitisen listasta”.
"Tietoja on haettu myös Facebookista, Linkedinistä, Twitteristä ja muilta suosituilta sosiaalisen median sivustoilta."Kiinalaiset henkiltietoja keräämässä:

Kiina | Kiinalaisyritys keräsi 2,4 miljoonan ihmisen tietokannan – HS:n näkemässä vuodetussa aineistossa on myös satoja suomalaisnimiä, kuten poliitikkojen lapsia
Kiinalaisyritys Zhenhua Data keräsi kaikkialta maailmasta tietokantaa vallan verkostoista. Tietokannassa on ainakin 800 suomalaisnimeä – ja kuva ”Tiitisen listasta”.www.hs.fi
Selvä se sitten on, kohta pyörii mustia
Ssangyong Mussoja nurkissa.
Tuo "Tiitisen lista" on hyvä osoitus pohjoisen poikien maskirovkasta.

