Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
In the run-up to Ars Frontiers, I had the opportunity to talk with Lesley Carhart, director of Incident Response at Dragos. Known on Twitter as @hacks4pancakes, Carhart is a veteran responder to cyber incidents affecting critical infrastructure and has been dealing with the challenges of securing industrial control systems and operational technology (OT) for years. So it seemed appropriate to get her take on what needs to be done to improve the security of critical infrastructure both in industry and government, particularly in the context of what’s going on in Ukraine.
Much of it is not new territory. “Something that we’ve noticed for years in the industrial cybersecurity space is that people from all different organizations, both military and terrorists around the world, have been pre-positioning to do things like sabotage and espionage via computers for years,” Carhart explained. But these sorts of things rarely get attention because they’re not flashy—and as a result, they don’t get attention from those holding the purse strings for investments that might correct them.
As a result, Carhart said, organizations aiming to benefit from the exploitation of industrial technology have spent years “trying to build their capacity so that when a geopolitical situation arose that it would be fruitful for them to do so, [they would] be able to attack infrastructure systems using cyber.”
An example of these capabilities is Pipedream, "a collection of tools that could be used to potentially intrude into industrial control systems and cause an impact to certain types of systems,” Carhart noted. Pipedream was uncovered by security professionals before it could be used to do damage, but it demonstrates that “people are pre-positioning to do things in the future,” Carhart said. “They have learned over the years, and certainly over the last couple of months, that sabotage, espionage, and information operations can be incredibly valuable as an element to traditional warfare… to demoralize enemies, sow confusion and dissent, and also impact the critical services that a civilian population uses while they're also dealing with an armed conflict.”
Much is being done by people trying to defend industrial networks, and there’s a great deal of work being done to improve the security of industrial systems and prepare for trouble. But, “some industries are much more well-resourced than others” for those tasks, Carhart noted. Municipally owned utilities aren’t on the same footing resource-wise as large corporations with vast cybersecurity resources. The US's Cybersecurity and Infrastructure Security Agency and other organizations are trying to help provide resources needed by municipal and other smaller utilities. But just how much CISA can do going forward to protect these organizations and other state and local providers of critical infrastructure is an open question.
Operational technology has a much longer life cycle than “normal” IT. We talked about what that means, both from the standpoint of securing existing OT and finding the people to do the critical work to establish and maintain that security. While some improvements are coming to security as Windows 10 makes its way into embedded systems and other OT, Carhart said, “we’ll probably be seeing Windows 10 for another 30 years in those environments”—and along with it, many of the security challenges IT has been facing down for years already.

How to make critical infrastructure safer—there’s a long way to go
At Ars Frontiers, Lesley Carhart spoke about the systems that make our world work.
video linkin alla
On Ukraine’s battlefields, the simple act of powering up a cellphone can beckon a rain of deathly skyfall. Artillery radar and remote controls for unmanned aerial vehicles may also invite fiery shrapnel showers.
This is electronic warfare, a critical but largely invisible aspect of Russia’s war against Ukraine. Military commanders largely shun discussing it, fearing they’ll jeopardize operations by revealing secrets.
A critical flaw in the LTE firmware of the fourth-largest smartphone chip biz in the world could be exploited over the air to block people's communications and deny services.
The vulnerability in the baseband – or radio modem – of UNISOC's chipset was found by folks at Check Point Research who were looking for ways the silicon could be used to remotely attack devices. It turns out the flaw doesn't just apply to lower-end smartphones but some smart TVs, too.
Check Point found attackers could transmit a specially designed radio packet to a nearby device to crash the firmware, ending that equipment's cellular connectivity, at least, presumably until it's rebooted. This would be achieved by broadcasting non-access stratum (NAS) messages over the air that when picked up and processed by UNISOC's firmware would end in a heap memory overwrite.
"We scanned NAS message handlers within a short period of time and found a vulnerability which can be used to disrupt the device's radio communication through a malformed packet," the researchers wrote in a detailed and fascinating advisory this week.
"A hacker or a military unit can leverage such a vulnerability to neutralize communications in a specific location." They stressed that the flaw was in the firmware of the UNISOC chipset and not the Android operating system.
UNISOC is a 21-year-old chip designer based in China that spent the first 17 years of life known as Spreadtrum Communications, and that by 2011 was supplying chips for more than half of the mobile phones in the country. In 2018, the company changed its name to UNISOC. The chips are found mostly in smartphones in Asia and Africa due to the low prices of its silicon.
According to market analyst firm Counterpoint, UNISOC is the fourth-largest smartphone chip house in the world, behind MediaTek, Qualcomm and Apple.

UNISOC phone chip firmware vulnerable to remote crash
Android patches incoming for NAS-ty memory overwrite flaw
The notorious Conti ransomware gang has working proof-of-concept code to exploit low-level Intel firmware vulnerabilities, according to Eclypsium researchers.
Recently leaked Conti documents show the criminals developed the software more than nine months ago, and this is important because exploiting these kinds of weaknesses expands the extend and depth of an intrusion, the firmware security shop's analysis noted.
Specifically, we're told, Conti came up with code that targeted the Intel Management Engine (ME), a tiny hidden computer – with its own CPU, OS and software – within a processor chipset that runs independently from the main cores and provides various features including out-of-band management. The ME has total control over the box, so if you manage to compromise the ME, you'll be able to persistently infect and affect the machine below the operating system and its defenses.
The leaks show that the gang was fuzzing the ME to find undocumented commands and vulnerabilities. As a side note: although Conti engineers were looking for new ME vulns, the Eclypsium researchers have published a list of known ME flaws (plus related Intel advisories and CVEs) that enable remote code execution or privilege escalation. So it would be wise to take a quick break from reading this and make those fixes now if you haven't already.

Conti spotted working on exploits for Intel ME flaws
Don't leave those firmware patches to last
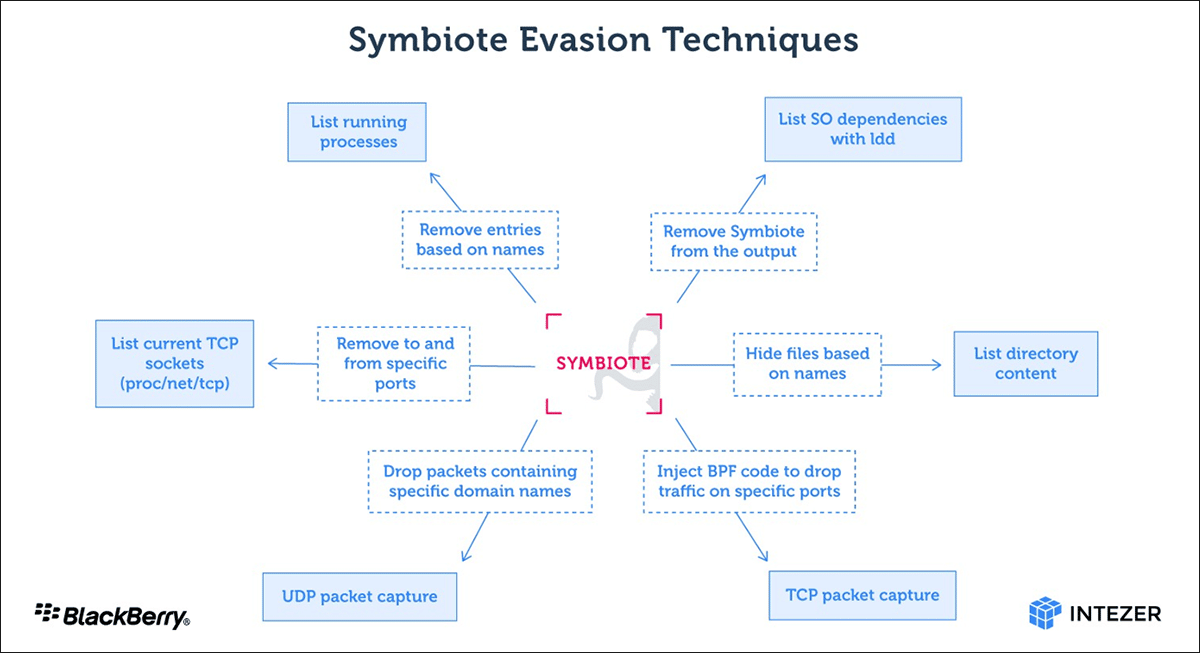
Researchers have unearthed a discovery that doesn’t occur all that often in the realm of malware: a mature, never-before-seen Linux backdoor that uses novel evasion techniques to conceal its presence on infected servers, in some cases even with a forensic investigation.
On Thursday, researchers from Intezer and The BlackBerry Threat Research & Intelligence Team said that the previously undetected backdoor combines high levels of access with the ability to scrub any sign of infection from the file system, system processes, and network traffic. Dubbed Symbiote, it targets financial institutions in Brazil and was first detected in November.
Researchers for Intezer and BlackBerry wrote:
What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object (SO) library that is loaded into all running processes using LD_PRELOAD (T1574.006), and parasitically infects the machine. Once it has infected all the running processes, it provides the threat actor with rootkit functionality, the ability to harvest credentials, and remote access capability.
With the help of LD_PRELOAD, Symbiote will load before any other shared objects. That allows the malware to tamper with other library files loaded for an application.

New ultra-stealthy Linux backdoor isn’t your everyday malware discovery
Symbiote gives remote access to any account. Normal methods don't detect it.
“When an administrator starts any packet capture tool on the infected machine, BPF bytecode is injected into the kernel that defines which packets should be captured,” the researchers wrote. “In this process, Symbiote adds its bytecode first so it can filter out network traffic that it doesn’t want the packet-capturing software to see.”
For the last two months, Costa Rica has been under siege. Two major ransomware attacks have crippled many of the country’s essential services, plunging the government into chaos as it scrambles to respond. Officials say that international trade ground to a halt as the ransomware took hold and more than 30,000 medical appointments have been rescheduled, while tax payments have also been disrupted. Millions have been lost due to the attacks, and staff at affected organizations have turned to pen and paper to get things done.
Costa Rica’s government, which changed midway through the attacks after elections earlier this year, has declared a “national emergency” in response to the ransomware—marking the first time a country has done so in response to a cyberattack. Twenty-seven government bodies were targeted in the first attacks, which ran from mid-April until the start of May, according to new president Rodrigo Chaves. The second attack, at the end of May, has sent Costa Rica’s health care system into a spiral. Chaves has declared “war” on those responsible.
At the heart of the hacking spree is Conti, the notorious Russia-linked ransomware gang. Conti claimed responsibility for the first attack against Costa Rica’s government and is believed to have some links to the ransomware-as-a-service operation HIVE, which was responsible for the second attack impacting the health care system. Last year, Conti extorted more than $180 million from its victims, and it has a history of targeting health care organizations. However, in February thousands of the group’s internal messages and files were published online after it backed Russia’s war against Ukraine.

Conti's Attack Against Costa Rica Sparks a New Ransomware Era
A pair of ransomware attacks crippled parts of the country—and rewrote the rules of cybercrime.
pitkä artikkeli
The vulnerability, called PACMAN, assumes that there is already a software bug in operation on the computer that can read and write to different memory addresses. It then exploits a detail of the M1 hardware architecture to give the bug the power to execute code and possibly take over the operating system. “We assume the bug is there and we make it into a more serious bug,” says Joseph Ravichandran a student of Yan’s who worked on the exploit with fellow students Weon Taek Na and Jay Lang.
To understand how the attack works you have to get a handle on what pointer authentication is and how a detail of processor architecture called speculative execution works. Pointer authentication is a way to guard against software attacks that try to corrupt data that holds memory addresses, or pointers. For example, malicious code might execute a buffer overflow attack, writing more data than expected into a part of memory, with the excess spilling over into a pointer’s address and overwriting it. That might then mean that instead of the computer’s software executing code stored at the original address, it is diverted to malware stored at the new one.
Pointer authentication appends a cryptographic signature to the end of the pointer. If there’s any malicious manipulation of the pointer, the signature will no longer match up with it. PACs are used to guard the core of the system’s operating system, the kernel. If an attacker got so far as to manipulate a kernel pointer, the mismatch between the pointer and its authentication code would produce what’s called an “exception,” and the system would crash, ending the malware’s attack. Malware would have to be extremely lucky to guess the right code, about 1 in 65,000.
PACMAN finds a way for malware to keep guessing over and over without any wrong guesses triggering a crash. How it does this goes to the heart of modern computing. For decades now, computers have been speeding up processing using what’s called speculative execution. In a typical program, which instruction should follow the next often depends on the outcome of the previous instruction (think if/then). Rather than wait around for the answer, modern CPUs will speculate—make an educated guess—about what comes next and start executing instructions along those lines. If the CPU guessed right, this speculative execution has saved a bunch of clock cycles. If it turns out to have guessed wrong, all the work is thrown out, and the processor begins along the correct sequence of instructions. Importantly, the mistakenly computed values are never visible to the software. There is no program you could write that would simply output the results of speculative execution.

“PACMAN” Hack Can Break Apple M1’s Last Line of Defense
“What we found is actually quite fundamental,” says MIT's Mengjia Yan. “It’s a class of attack. Not one bug.”
 spectrum.ieee.org
spectrum.ieee.org
The researchers have dubbed their attack Hertzbleed because it uses the insights into DVFS to expose—or bleed out—data that's expected to remain private. The vulnerability is tracked as CVE-2022-24436 for Intel chips and CVE-2022-23823 for AMD CPUs. The researchers have already shown how the exploit technique they developed can be used to extract an encryption key from a server running SIKE, a cryptographic algorithm used to establish a secret key between two parties over an otherwise insecure communications channel.
The researchers said they successfully reproduced their attack on Intel CPUs from the 8th to the 11th generation of the Core microarchitecture. They also claimed that the technique would work on Intel Xeon CPUs and verified that AMD Ryzen processors are vulnerable and enabled the same SIKE attack used against Intel chips. The researchers believe chips from other manufacturers may also be affected.
In a blog post explaining the finding, research team members wrote:
Hertzbleed is a new family of side-channel attacks: frequency side channels. In the worst case, these attacks can allow an attacker to extract cryptographic keys from remote servers that were previously believed to be secure.
Hertzbleed takes advantage of our experiments showing that, under certain circumstances, the dynamic frequency scaling of modern x86 processors depends on the data being processed. This means that, on modern processors, the same program can run at a different CPU frequency (and therefore take a different wall time) when computing, for example, 2022 + 23823 compared to 2022 + 24436.
Hertzbleed is a real, and practical, threat to the security of cryptographic software.
We have demonstrated how a clever attacker can use a novel chosen-ciphertext attack against SIKE to perform full key extraction via remote timing, despite SIKE being implemented as “constant time”.
A new vulnerability in Intel and AMD CPUs lets hackers steal encryption keys
Hertzbleed attack targets power-conservation feature found on virtually all modern CPUs.
Ketju jatkuu toki tätä pidemmäs.
Police forces around the world have increasingly used hacking tools to identify and track protesters, expose political dissidents' secrets, and turn activists' computers and phones into inescapable eavesdropping bugs. Now, new clues in a case in India connect law enforcement to a hacking campaign that used those tools to go an appalling step further: planting false incriminating files on targets' computers that the same police then used as grounds to arrest and jail them.
More than a year ago, forensic analysts revealed that unidentified hackers fabricated evidence on the computers of at least two activists arrested in Pune, India, in 2018, both of whom have languished in jail and, along with 13 others, face terrorism charges. Researchers at security firm SentinelOne and nonprofits Citizen Lab and Amnesty International have since linked that evidence fabrication to a broader hacking operation that targeted hundreds of individuals over nearly a decade, using phishing emails to infect targeted computers with spyware, as well as smartphone hacking tools sold by the Israeli hacking contractor NSO Group. But only now have SentinelOne's researchers revealed ties between the hackers and a government entity: none other than the very same Indian police agency in the city of Pune that arrested multiple activists based on the fabricated evidence.

Police linked to hacking campaign to frame Indian activists
Details connect police in India to a plot to plant evidence on victims' computers.
Europol cops have arrested nine suspected members of a cybercrime ring involved in phishing, internet scams, and money laundering.
The alleged crooks are believed to have stolen "several million euros" from at least "dozens of Belgian victims," according to that nation's police, which, along with the Dutch, supported the cross-border operation.
On Tuesday, after searching 24 houses in the Netherlands, officers cuffed eight men between the ages of 25 and 36 from Amsterdam, Almere, Rotterdam, and Spijkenisse, and a 25-year-old woman from Deventer. We're told the cops seized, among other things, a firearm, designer clothing, expensive watches, and tens of thousands of euros.
The suspects are in police custody and will be extradited to Belgium. Dutch police haven't ruled out additional arrests.
According to law enforcement, a crime ring contacted victims via scam emails, text messages, and cellphone messaging apps. These messages included a phishing link that led to fake banking websites, which were used to harvest credentials.
"Thinking they were viewing their own bank accounts through this website, the victims were duped into providing their banking credentials to the suspects," Europol noted, adding that whoever was behind the scams used money mules to transfer funds from victims' accounts before cashing out their loot.
In addition to the millions of stolen euros, those fraudsters also trafficked drugs and possibly firearms, according to police.

Cops arrests nine suspected of stealing millions via email
Victims lured into handing over online banking logins, police say
An unusually advanced hacking group has spent almost two years infecting a wide range of routers in North America and Europe with malware that takes full control of connected devices running Windows, macOS, and Linux, researchers reported on Tuesday.
So far, researchers from Lumen Technologies' Black Lotus Labs say they've identified at least 80 targets infected by the stealthy malware, infecting routers made by Cisco, Netgear, Asus, and DayTek. Dubbed ZuoRAT, the remote access Trojan is part of a broader hacking campaign that has existed since at least the fourth quarter of 2020 and continues to operate.
The discovery of custom-built malware written for the MIPS architecture and compiled for small office and home office routers is significant, particularly given its range of capabilities. Its ability to enumerate all devices connected to an infected router and collect the DNS lookups and network traffic they send and receive and remain undetected is the hallmark of a highly sophisticated threat actor.
"While compromising SOHO routers as an access vector to gain access to an adjacent LAN is not a novel technique, it has seldom been reported," Black Lotus Labs researchers wrote. "Similarly, reports of person-in-the-middle style attacks, such as DNS and HTTP hijacking, are even rarer and a mark of a complex and targeted operation. The use of these two techniques congruently demonstrated a high level of sophistication by a threat actor, indicating that this campaign was possibly performed by a state-sponsored organization."

A wide range of routers are under attack by new, unusually sophisticated malware
Router-stalking ZuoRAT is likely the work of a sophisticated nation-state, researchers say.
Palo Alto Networks' Unit 42 threat intelligence team has claimed that a piece of malware that 56 antivirus products were unable to detect is evidence that state-backed attackers have found new ways to go about the evil business.
Unit 42's analysts assert that the malware was spotted in May 2022 and contains a malicious payload that suggests it was created using a tool called Brute Ratel (BRC4). On its rather brazen website, BRC4 is described as "A Customized Command and Control Center for Red Team and Adversary Simulation". The tool's authors even claim they reverse-engineered antivirus software to make BRC4 harder to detect.
The malware Unit 42 observed starts life as a file that pretends to be the curriculum vitae of a chap named Roshan Bandara. Unusually, Bandara's CV is offered as an ISO file – a disk image file format. If users click on the ISO it mounts as a Windows drive and displays a File Manager window with a sole file: "Roshan-Bandara_CV_Dialog".
The file looks like a Microsoft Word file but – shockingly – is not really a CV. When double-clicked it opens CMD.EXE and runs the OneDrive Updater, which retrieves and installs BRC4.

Near-undetectable malware linked to Russia's Cozy Bear
The fun folk who attacked Solar Winds using a poisoned CV and tools from the murky world of commercial hackware
Quick to jump in, Binance CEO Changpeng Zhao stated on Twitter the data was swiped after a government developer wrote a blog post on the Chinese Software Developer Network that, presumably accidentally, included the credentials necessary to access the information.
But according to cybersecurity experts, this may not be correct. Instead, the data was exposed to the world from a non-password-protected web dashboard. And that public-facing Kibana-powered site had been left open since the end of 2020, according to LeakIX, a website that tracks exposed databases online.
Open-source Kibana is used all around the world to view and manage Elasticsearch clusters. "The service leaking the data was an unprotected Kibana instance running on port 5601, the default Kibana port," LeakIX claimed. If that's correct, it means if anyone scanned the internet for public-facing Kibana deployments, they would have eventually found this one in China.
We're told the service was running on a .kibana.elasticsearch.aliyuncs.com domain. "This is the default Kibana endpoint exposed by Alibaba when an Elasticsearch service is deployed on a public network," the researchers wrote.
Furthermore, we're told, Alibaba Cloud documentation shows that "exposure of the endpoint to a public network will happen by default." It also said "a default username and password (elastic/elastic) will be assigned to the Elasticsearch cluster."
Now it all seems to click into place. If LeakIX is correct, the thief may have pulled the data from the unprotected public-facing Kibana instance or from the underlying public Elasticsearch cluster that Kibana provided a web interface for. The exposed Elasticsearch cluster's version, 5.5.3, is a legacy version "which did not support authentication out of the box and required a paid license or a third-party authentication plugin to enable it," LeakIX wrote, adding that there was no evidence this security defense was enabled.
The team added: "On the 1st of July, Alibaba made private or shut down all the Kibana servers running 5.5.3."
There is no indication that anyone other than the techie who set up this deployment was at fault for this security lapse. The software was hosted on Alibaba, and we have asked the cloud giant for its take on events.

How data on a billion people may have leaked from China
Record-breaking dump thanks to password-less Kibana endpoint?
The botnet behind the largest-ever HTTPS-based distributed-denial-of-service (DDoS) attack has been named after a tiny shrimp.
Cloudflare said it thwarted the 26 million request per second (rps) attack last month, and we're told the biz has been tracking the botnet ever since. Now, the internet infrastructure company has given the botnet a name — Mantis — and said it's the next phase in the evolution of Meris.
"The name Mantis was chosen to be similar to 'Meris' to reflect its origin, and also because this evolution hits hard and fast," Cloudflare product manager Omer Yoachimik wrote in a blog post this week. "Over the past few weeks, Mantis has been especially active directing its strengths towards almost 1,000 Cloudflare customers."

Mantis, the tiny shrimp that launched 3,000 DDoS attacks
Watch out for deadly pinchers after that record-breaking attack
While Mantis initially launched its network-flooding-traffic attack over HTTPS, in the month since its discovery, Mantis has launched more than 3,000 HTTP DDoS attacks against the firm's customers, Yoachimik added.
In addition to sounding similar to Meris, Mantis is also a "small but powerful" shrimp. The tiny crustaceans are about only about 10cm in length, but their "thumb-splitter" claws can inflict serious damage against prey or enemies — and can strike with a force of 1,500 newtons at speeds of 83km/h from a standing start.
Likewise, the Mantis botnet operates a small fleet of bots (a little over 5,000), but uses them to cause massive damage – specifically, a record-breaking attack.
"That's an average of 5,200 HTTPS rps per bot," Yoachimik explained. "Generating 26 million HTTP requests is hard enough to do without the extra overhead of establishing a secure connection, but Mantis did it over HTTPS."
These HTTPS-based attacks are more expensive than their HTTP counterparts because it costs more in compute resources to establish a secure TLS connection. And because of this, instead of using hijacked IoT devices (like DVRs or cameras) to form its bot army, Mantis uses virtual machines and servers.
From the what-could-possibly-go-wrong files comes this: People hawking password-cracking software are targeting the hardware used in industrial-control facilities with malicious code that makes their systems part of a botnet, a researcher reported.
Lost passwords happen in many organizations. A programmable logic controller—used to automate processes inside factories, electric plants, and other industrial settings, for example, may be set up and largely forgotten over the following years. When a replacement engineer later identifies a problem affecting the PLC, they may discover the now long-gone original engineer never left the passcode behind before departing the company.
According to a blog post from security firm Dragos, an entire ecosystem of malware attempts to capitalize on scenarios like this one inside industrial facilities. Online advertisements like those below promote password crackers for PLCs and human-machine interfaces, which are the workhorses inside these environments.

Hackers are targeting industrial systems with malware
An entire ecosystem of sketchy software is targeting potentially critical infrastructure.
“In general, it appears there is an ecosystem for this type of software,” Hanson said. “Several websites and multiple social media accounts exist all touting their password ‘crackers.’”
The account is concerning because it illustrates the threat posed to many industrial control settings. The criminals behind the malware Dragos analyzed were after money, but there’s no reason more malicious hackers out to sabotage a dam, power plant, or similar facility couldn’t perform a similar intrusion with much more severe consequences.
A security firm and the US government are advising the public to immediately stop using a popular GPS tracking device or to at least minimize exposure to it, citing a host of vulnerabilities that make it possible for hackers to remotely disable cars while they’re moving, track location histories, disarm alarms, and cut off fuel.
An assessment from security firm BitSight found six vulnerabilities in the Micodus MV720, a GPS tracker that sells for about $20 and is widely available. The researchers who performed the assessment believe the same critical vulnerabilities are present in other Micodus tracker models. The China-based manufacturer says 1.5 million of its tracking devices are deployed across 420,000 customers. BitSight found the device in use in 169 countries, with customers including governments, militaries, law enforcement agencies, and aerospace, shipping, and manufacturing companies.
BitSight discovered what it said were six “severe” vulnerabilities in the device that allow for a host of possible attacks. One flaw is the use of unencrypted HTTP communications that makes it possible for remote hackers to conduct adversary-in-the-middle attacks that intercept or change requests sent between the mobile application and supporting servers. Other vulnerabilities include a flawed authentication mechanism in the mobile app that can allow attackers to access the hardcoded key for locking down the trackers and the ability to use a custom IP address that makes it possible for hackers to monitor and control all communications to and from the device.

Critical flaws in GPS tracker enable “disastrous” and “life-threatening” hacks
China-based Micodus has yet to patch critical vulnerabilities in MV720 GPS tracker.
“BitSight recommends that individuals and organizations currently using MiCODUS MV720 GPS tracking devices disable these devices until a fix is made available,” researchers wrote. “Organizations using any MiCODUS GPS tracker, regardless of the model, should be alerted to insecurity regarding its system architecture, which may place any device at risk.”
The US Cybersecurity and Infrastructure Security Administration is also warning about the risks posed by the critical security bugs.
“Successful exploitation of these vulnerabilities could allow an attacker control over any MV720 GPS tracker, granting access to location, routes, fuel cutoff commands, and the disarming of various features (e.g., alarms),” agency officials wrote.
“The exploitation of these vulnerabilities could have disastrous and even life-threatening implications,” BitSight researchers wrote. “For example, an attacker could exploit some of the vulnerabilities to cut fuel to an entire fleet of commercial or emergency vehicles. Or, the attacker could leverage GPS information to monitor and abruptly stop vehicles on dangerous highways. Attackers could choose to surreptitiously track individuals or demand ransom payments to return disabled vehicles to working condition. There are many possible scenarios which could result in loss of life, property damage, privacy intrusions, and threaten national security.”

