StepanRudanskij
Greatest Leader
Kuinka näkyvästi?
Tiedän vain sen, että noilla taajuusalueilla lämmin ja suhteellisen kostea ilma vaimentaa signaalia.
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
Kuinka näkyvästi?
Kuinka näkyvästi?
Teoriassa, käytännössä microsoluverkko on melko immuuni suomessa esiintyville sääilmiöille.Saattaa tulla myös heijastumia satojen kilometrien päästä jotka häiritsevät (vaimentavat sitä signaalia jota on tarkoitus käyttää)
Kuumat säät ja ilmakehän kerrokset siinä asennossa.
https://en.wikipedia.org/wiki/Tropospheric_ducting
https://en.wikipedia.org/wiki/Radio_propagation
Näytön HDMI -kaapelin signaalin sieppaus ilmasta. Seinä välissä.
Tempestiin(emf)Tämähän on kätevä (ja erittäin laiton).
Onko mitään ajatusta mihin tuo perustuu?
https://threatpost.com/highly-sophisticated-parasite-rat-emerges-on-the-dark-web/134478/Researchers are tracking a remote access trojan (RAT) on underground markets that, so far, has only been attributed to one small malicious email campaign. However, the RAT, dubbed Parasite HTTP by the Proofpoint researchers that discovered it, has an impressive list of sophisticated features – raising concerns over future attacks.
The ad for the malware on the Dark Web reads, “Parasite HTTP is a professionally coded modular remote administration tool for windows written in C that has no dependencies except the OS itself. With the stub size of ~49KB and plugin support it presents perfect solution for controlling large amount of computers from a remote location.”
Like most RATs, Parasite HTTP offers extensive information-stealing capabilities, VNC for unobtrusively observing or controlling a PC and user management for bypassing permissions. It also advertises capabilities such as firewall bypass, optional system-wide persistence and injection to white-listed system processes. And, like legitimate software, Parasite HTTP includes administrator perks, like backups, analysis views and activity statistics, a secure log-in page with CAPTCHA, an advanced task management system and password recovery. It also features encryption for its C2 communications.
Where it really shines though is with an array of sandbox detection, anti-debugging, anti-emulation and other protections for evading detection and analysis.
https://www.tivi.fi/Kaikki_uutiset/...an-tilanne-nayttaa-paremmalta-kuin-on-6735390"Suomessa kyberturvallisuus pahasti hunningolla" – kenraalin mukaan tilanne näyttää paremmalta kuin on

Suomalaisissa tietojärjestelmissä on jatkuvasti ulkoisia tunkeutujia, joista ei kuitenkaan turvallisuussyistä kerrota julkisesti.
”Olemme havainneet ulkoisia toimijoita tietojärjestelmissä ja ryhtyneet tarvittaviin toimenpiteisiin. Mutta me emme uutisoi asioista, koska sekin on tunkeutujalle tärkeää tietoa, mitä on havaittu ja mitä ei”, prikaatikenraali Mikko Heiskanenkertoo torstaina ilmestyvän Tivi-lehden haastattelussa.
Havaittuja tunkeutujia ei kannata samasta syystä myöskään eliminoida, kunhan ne pysyvät hallinnassa ja vaarattomina.
Heiskasen mukaan kyberuhkien ”uusi normaali on se, että kenelläkään ei ole sataprosenttista varmuutta siitä, mitä tapahtuu”.
Kenraali Mikko Heiskanen johtaa pääesikunnan johtamisjärjestelmäosastoa, joka puolestaan suunnittelee Suomen kyberpuolustuksen kokonaisuutta.
Heiskasen vastuulla on kymmenen prosenttia Puolustusvoimien henkilöstöstä ja budjetista.
Heiskasen mukaan Suomessa kyberturvallisuutta on laiminlyöty pahasti ja se on hunningolla.
”Suomen kyberturvallisuustilanne näyttää hyvältä pitkälti vain siksi, että siitä ei ole kunnon kokonaiskuvaa”, Heiskanen sanoo Tivin haastattelussa.
”Sinänsä erinomaiset tavoitteet määriteltiin kansallisessa kyberturvallisuusstrategiassa jo 2013, mutta niiden toteutus on pahasti kesken tai puuttuu kokonaan.”
”Tiedustelulakia tarvitaan tilannekuvan muodostamiseksi”
Heiskasen mukaan valveutuneilla toimijoilla tilanne voi olla hyväkin, mutta toisaalta on olemassa pahoja aukkoja. Hän kaipaa pikaisesti myös pitkään valmisteltua ja kaivattua tiedustelulakia, joka puuttuu edelleen. Laki mahdollistaisi myös puolustuksen tehokkaan toiminnan.
”Tiedustelulain käsittely ajautui keskusteluksi sähköpostiurkinnasta. Eivät meitä puolustusvoimien kyberpuolustajia kiinnosta tavallisten ihmisten sähköpostit, vaan se että ylipäätään mahdollistetaan sananvapaus ja esimerkiksi koko sähköpostijärjestelmän toimiminen. Tiedustelutietoa tarvitaan tilannekuvan muodostamiseksi päätöksentekoa varten ja muun kyberpuolustuksen tarpeisiin”, Heiskanen sanoo.
Lakia tarvittaisiin myös vastavuoroisen kansainvälisen tiedustelutietojen vaihdon vuoksi.
Kenraali Mikko Heiskanen sanoo myös, että kyberturvallisuuden kokoavaksi johtajaksi tarvittaisiin pieni johtoelin, joka loisi yhteisen tilannekuvan ja ennusteen valtiojohdolle.
”Luonteva paikka sille olisi valtioneuvoston kanslia. Käytännön toimijaksi elimen johtoon sijoittaisin tehtäväkentältään laajennetun Kyberturvallisuuskeskuksen”, Heiskanen ehdottaa.
https://arstechnica.com/information...-the-war-on-phishing-enlist-machine-learning/It's Friday, August 3, and I have hooked a live one. Using StreamingPhish, a tool that identifies potential phishing sites by mining data on newly registered certificates, I've spotted an Apple phishing site before it's even ready for victims. Conveniently, the operator has even left a Web shell wide open for me to watch him at work.
The site's fully qualified domain name is appleld.apple.0a2.com, and there's another registered at the same domain—appleld.applle.0a2.com. As I download the phishing kit, I take a look at the site access logs from within the shell. Evidently, I've caught the site just a few hours after the certificate was registered.
As I poke around, I find other phishing sites on the same server in other directories. One targets French users of the telecommunications company Orange; others have more generic names intended to disguise them as part of a seemingly legitimate URL, such as Secrty-ID.com-Logine-1.0a2.com. Others still are spam blogs filled with affiliate links to e-commerce sites.
I check the access log again. The phisher has come back, logged in from an IP address in Morocco. He's unzipped the phishing kit. I send a heads up to the hosting company, SingleHop, with screenshots of the phishing page. I report the site to Google Safe Browsing and check one more time to see if I've missed anything.
The phisher notices something suspicious in his access logs. His site now up and running, he's deleted his shell—but not one on another subdomain. I consider going back in, but my work here is done anyway.
During the two hours I spent investigating this Apple phish, another 1,678 suspicious sites have popped up—spoofing brands including Apple, PayPal, Netflix, Instagram, and Bank of America. It will be nearly two days before SingleHop responds about the initial Apple one: "We were in touch with the management of the allegedly abused server, and after discussion the reported problem is claimed to be resolved."
That sort of interaction can't scale very well, but phishing seems to only be growing in its popularity. So if I learned anything from my StreamingPhish-time on the frontlines of this new digital war, it's this: if we're going to make a dent in these phishes, we're going to need a bigger boat—one with a whole lot more machine learning-based automation.
https://www.theregister.co.uk/2018/08/09/neural_network_malware/Here's perhaps a novel use of a neural network: proof-of-concept malware that uses AI to decide whether or not to attack a victim.
DeepLocker was developed by IBM eggheads, and is due to be presented at the Black Hat USA hacking conference in Las Vegas on Thursday. It uses a convolutional neural network to stay inert until the conditions are right to pounce.
When samples of software nasties are caught by security researchers, they can be reverse-engineered to see what makes them tick, and what activates their payload, which is the heart of the malicious code that spies on the infected user, steals their passwords, holds their files to ransom, and so on. These payloads can be triggered by all sorts of things, from the country in which the computer is located, whether or not it is running in a virtual machine, how long the machine has been idle, etc.
This is all information that network defenders and antivirus tools can use to thwart or mitigate the spread and operation of the software. However, while it's possible to reverse-engineer simple heuristic checks within a malicious program, to figure out the trigger conditions, it's rather hard to work out what will make a trained neural network run a payload, just by studying its data structure.
Similarly, if the payload is encrypted, it's possible the decryption key can be figured out from the heuristic code that unlocks it. However, if the payload is encrypted using a key derived from a neural network's output, and you can't easily reverse-engineer the network, you'll have a hard time making it up cough up the right key and decrypting the payload.
“While a class of malware like DeepLocker has not been seen in the wild to date, these AI tools are publicly available, as are the malware techniques being employed — so it’s only a matter of time before we start seeing these tools combined by adversarial actors and cybercriminals," said Stoecklin.
"In fact, we would not be surprised if this type of attack were already being deployed. The security community needs to prepare to face a new level of AI-powered attacks. We can’t, as an industry, simply wait until the attacks are found in the wild to start preparing our defenses. To borrow an analogy from the medical field, we need to examine the virus to create the 'vaccine.'"
https://www.theregister.co.uk/2018/08/10/data_center_hacking/Data centers are vital in this cloudy world – yet little-understood management chips potentially give hackers easy access to their servers in ways sysadmins may not have imagined.
The components in question are known as baseband management controllers (BMCs). They are discrete microcontrollers popped into boxes by the likes of Dell, HPE, and Lenovo to allow data-center managers to control machines without having to brave the chilly confines of a server farm. They can be accessed in various ways, from dedicated wired networks to Ethernet LANs.
BMCs can be used to remotely monitor system temperature, voltage and power consumption, operating system health, and so on, and power cycle the box if it runs into trouble, tweak configurations, and even, depending on the setup, reinstall the OS – all from the comfort of an operations center, as opposed to having to find an errant server in the middle of a data center to physically wrangle. They also provide the foundations for IPMI.
"They are basically a machine inside a machine – even if the server is down, as long as it has power, the BMCs will work,” said Nico Waisman, VP of security shop Immunity, in a talk at this year's Black Hat USA hacking conference on Thursday.
“They have a full network stack, KVM, serial console, and power management. It’s kind of like the perfect backdoor: you can remotely connect, reboot a device, and manage keyboard and mouse.”
It’s a situation not unlike Intel’s Active Management Technology, a remote management component that sits under the OS or hypervisor, has total control over a system, and been exploited more than once over the years.
Waisman and his colleague Matias Soler, a senior security researcher at Immunity, examined these BMC systems, and claimed the results weren’t good. They even tried some old-school hacking techniques from the 1990s against the equipment they could get hold of, and found them to be very successful. With HP's BMC-based remote management technology iLO4, for example, the builtin web server could be tricked into thinking a remote attacker was local, and so didn’t need to authenticate them.
"We decided to take a look at these devices and what we found was even worse than what we could have imagined," the pair said. "Vulnerabilities that bring back memories from the 1990s, remote code execution that is 100 per cent reliable, and the possibility of moving bidirectionally between the server and the BMC, making not only an amazing lateral movement angle, but the perfect backdoor too."
The fear is that once an intruder gets into a data center network, insecure BMC firmware could be used to turn a drama into a crisis: vulnerabilities in the technology could be exploited to hijack more systems, install malware that persists across reboots and reinstalls, or simple hide from administrators.
Sadly, the security of the BMCs is lax – and that's perhaps because manufacturers made the assumption that once a miscreant gets access to a server rack's baseboard controllers, it's game over completely anyway.
Of course, data center managers aren’t stupid, and BMC services are typically kept behind firewalls, segmented on the network, or only accessible via dedicated serial lines – and certainly shouldn't be facing the public internet. However, Waisman and Soler said they found plenty exposed to the web.
The bottom line is that IT admins need to assess the routes to their BMC services, make sure none are internet facing, and harden up access. Once an attacker establishes persistence with a BMC, you'll really wish you'd taken their advice.
https://www.theregister.co.uk/2018/08/10/satellite_hacking/Four years ago, IOActive security researcher Ruben Santamarta came to Black Hat USA to warn about insecurities in aircraft satellite-communication (SATCOM) systems. Now he’s back with more doom and gloom.
During a presentation at this year's hacking conference in Las Vegas this week, he claimed he had found a host of flaws in aircraft, shipping, and military satellite comms and antenna-control boxes that can be exploited to snoop on transmissions, disrupt transportation, infiltrate computers on military bases, and more – including possibly directing radio-transmission electronics to bathe fleshy humans in unhealthy amounts of electromagnetic radiation.
“It’s pretty much the same principle as a microwave oven,” he told The Register. “The flaws allow us to ramp up the frequency.”
The vulnerabilities stem from a variety of blunders made by SATCOM hardware manufacturers. Some build backdoors into their products for remote maintenance, which can be found and exploited, while other equipment has been found to be misconfigured or using hardcoded credentials, opening them up to access by miscreants. These holes can be abused by a canny hacker to take control of an installation's antenna, and monitor the information the data streams contain.
"Some of the largest airlines in the US and Europe had their entire fleets accessible from the internet, exposing hundreds of in-flight aircraft," according to Santamarta. "Sensitive NATO military bases in conflict zones were discovered through vulnerable SATCOM infrastructure. Vessels around the world are at risk as attackers can use their own SATCOM antennas to expose the crew to radio-frequency radiation."
Essentially, think of these vulnerable machines as internet-facing or network-connected computers, complete with exploitable remote-code-execution vulnerabilities. Once you've been able to get control of them – and there are hundreds exposed to the internet, apparently – you can disrupt or snoop on or meddle with their communications, possibly point antennas at people, and attack other devices on the same network.
This is all particularly worrying for military antennas. Very often these are linked to GPS units, and an intruder could use this data to divine the location of military units, as well as siphon off classified information from the field. Similar SATCOM systems are often used by journalists in trouble spots; unwelcome press interest could be targeted, perhaps terminally.
In satellite-communications units for the shipping industry, Santamarta said he found flaws that could be used to identify where a particular vessel was, and also damage installations by overdriving the hardware. Malicious firmware could be installed to interfere with positioning equipment, and lead ships astray, it was claimed.
Santamarta also postulated crews and passengers on container and cruise ships could be harmed by directing antennas at them. There are safeguards to make sure antennas can’t point at people, but those could be overridden, he claimed.
To make matters worse, some of these software flaws remain unpatched, as manufacturers continue to develop updates, while others privately disclosed to vendors have been fixed.
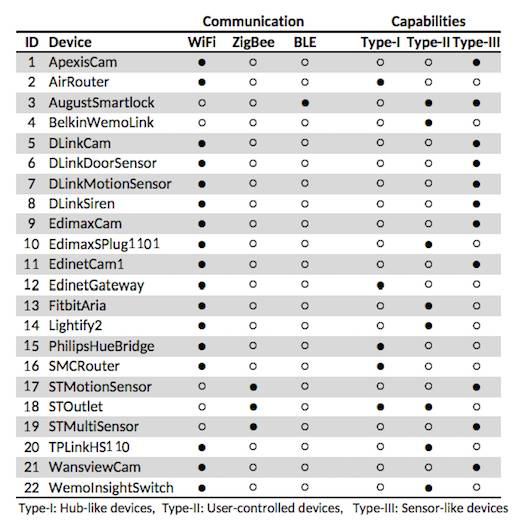
https://www.theregister.co.uk/2018/08/10/internet_of_things_encryption_snooping/You don't need to sniff clear-text Internet of Things traffic to comprehensively compromise a gadget-fan's home privacy: mere traffic profiles will do the job nicely, a group of researchers has found.
Encrypted streams can be surprisingly revealing, after all: just ask Cisco, which learned how to identify malware crossing the network boundary, without having to decrypt the data.
What they found is that even with encrypted payloads, light bulbs, power switches, door locks, speakers and the like reveal their activity in how, rather than what, they communicate: the duration of a traffic spike, the length of packets in a communication, packets' inter-arrival time, deviations in packet lengths, whether the user is contacting the device locally or over the Internet.
Once the researchers had sampled traffic from a selection of 22 devices (shown in the table below), the combination of unencrypted headers (MAC address and other information that helps identify manufacturers) with traffic patterns revealed not just what a device is doing (the light went on or off), but enough to infer what the user is doing (walking between rooms, sleeping, cooking and so on).
http://www.digitalattackmap.com"Palvelunestohyökkäys on kaatanut useiden viranomaisten verkkosivustoja – tunnistautuminen ei onnistu Kelan sivuilla
https://yle.fi/uutiset/3-10349357
12.8.2018 klo 18:33
Palvelunestohyökkäys kaatoi iltapäivällä useiden valtionhallinnon viranomaisten ja ministeriöiden verkkosivustoja, kertoo Valtion tieto- ja viestintätekniikkakeskuksen Valtorin toimitusjohtaja Pasi Lehmus.
Palvelunestohyökkäys tapahtui Lehmuksen tietojen mukaan noin kello 16.30. Hyökkäys tapahtui Valtorin palveluita vastaan. Se estää useisiin verkkopalveluihin tunnistautumisen, ja osa sivustoista ei aukene ollenkaan.
Muun muassa valtioneuvoston, sisäministeriön, opetus- ja kulttuuriministeriön sekä sosiaali- ja terveysministeriön sivut ovat poissa käytöstä. Myös poliisin ja tullin verkkosivut ovat kaatuneet.
Terveydenhuollon Omakannan, Kelan ja Väestörekisterikeskuksen sivuille kirjautuminen ei onnistu. Palvelunestohyökkäys on Lehmuksen mukaan selätetty, ja nyt verkkosivustoja aletaan nostaa ylös."
