http://hackaday.com/2017/05/14/car-...ll-their-research-and-vulnerabilities-online/[Charlie Miller] and [Chris Valasek] Have just released all their research including (but not limited to) how they hacked a Jeep Cherokee after the newest firmware updates which were rolled out in response to their Hacking of a Cherokee in 2015.
FCA, the Corp that owns Jeep had to recall 1.5 million Cherokee’s to deal with the 2015 hack, issuing them all a patch. However the patch wasn’t all that great it actually gave [Charlie] and [Chris] even more control of the car than they had in the first place once exploited. The papers they have released are a goldmine for anyone interesting in hacking or even just messing around with cars via the CAN bus. It goes on to chronicle multiple hacks, from changing the speedometer to remotely controlling a car through CAN message injection. And this release isn’t limited to Jeep. The research covers a massive amount of topics on a number of different cars and models so if you want to do play around with your car this is the car hacking bible you have been waiting for.
Jeep are not too happy about the whole situation. The dump includes a lot of background for vehicles by multiple manufactureres. But the 2015 hack was prominent and has step by step instructions. Their statement on the matter is below.
Under no circumstances does FCA condone or believe it’s appropriate to disclose ‘how-to information’ that would potentially encourage, or help enable hackers to gain unauthorized and unlawful access to vehicle systems.
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cyber-ketju: verkkovakoilu,kännyköiden ja wlanien seuranta, hakkerointi, virukset, DoS etc
- Viestiketjun aloittaja OldSkool
- Aloitus PVM
Microsoftin mukaan NSA:n työkalut mahdollistivat viikonlopun kyberhyökkäyksen – ”Kuin Yhdysvalloilta olisi varastettu Tomahawk-ohjuksia”
Teknologiayhtiö Microsoft vaatii valtioita ottamaan vastuun kehittämistään tiedustelutyökaluista. Muun muassa NSA:n ja CIA:n tiedustelutyökaluja on vuodettu nettiin viime aikoina.
”Toistuvasti valtioiden löytämät ohjelmistojen heikkoudet ovat vuotaneet julkisuuteen ja aiheuttaneet laajaa vahinkoa. Vastaava esimerkki perinteisten aseiden puolella olisi tilanne, jossa Yhdysvaltojen armeijalta olisi varastettu Tomahawk-ohjuksia”, hän kirjoittaa.
ASIANTUNTIJAT epäilevät kiristysohjelman liikkeelle laskeneiden rikollisten hyödyntäneen tiedusteluvirasto NSA:n työkaluja. Microsoftin Smithin mielestä hyökkäys ei jätä mitään arvailujen varaan.
http://www.hs.fi/talous/art-2000005211159.html
Teknologiayhtiö Microsoft vaatii valtioita ottamaan vastuun kehittämistään tiedustelutyökaluista. Muun muassa NSA:n ja CIA:n tiedustelutyökaluja on vuodettu nettiin viime aikoina.
”Toistuvasti valtioiden löytämät ohjelmistojen heikkoudet ovat vuotaneet julkisuuteen ja aiheuttaneet laajaa vahinkoa. Vastaava esimerkki perinteisten aseiden puolella olisi tilanne, jossa Yhdysvaltojen armeijalta olisi varastettu Tomahawk-ohjuksia”, hän kirjoittaa.
ASIANTUNTIJAT epäilevät kiristysohjelman liikkeelle laskeneiden rikollisten hyödyntäneen tiedusteluvirasto NSA:n työkaluja. Microsoftin Smithin mielestä hyökkäys ei jätä mitään arvailujen varaan.
http://www.hs.fi/talous/art-2000005211159.html
StepanRudanskij
Greatest Leader
Microsoftin mukaan NSA:n työkalut mahdollistivat viikonlopun kyberhyökkäyksen – ”Kuin Yhdysvalloilta olisi varastettu Tomahawk-ohjuksia”
Teknologiayhtiö Microsoft vaatii valtioita ottamaan vastuun kehittämistään tiedustelutyökaluista. Muun muassa NSA:n ja CIA:n tiedustelutyökaluja on vuodettu nettiin viime aikoina.
”Toistuvasti valtioiden löytämät ohjelmistojen heikkoudet ovat vuotaneet julkisuuteen ja aiheuttaneet laajaa vahinkoa. Vastaava esimerkki perinteisten aseiden puolella olisi tilanne, jossa Yhdysvaltojen armeijalta olisi varastettu Tomahawk-ohjuksia”, hän kirjoittaa.
ASIANTUNTIJAT epäilevät kiristysohjelman liikkeelle laskeneiden rikollisten hyödyntäneen tiedusteluvirasto NSA:n työkaluja. Microsoftin Smithin mielestä hyökkäys ei jätä mitään arvailujen varaan.
http://www.hs.fi/talous/art-2000005211159.html
Ai helkkari tuota tekopyhyyttä. Mikkisofta on yhteistyössä NSA:n ja muidenkin valtiollisten kanssa nuo backdoorit järjestänyt ohjelmiinsa.
Mikkisofta on yhteistyössä NSA:n ja muidenkin valtiollisten kanssa nuo backdoorit järjestänyt ohjelmiinsa.
Oli yhteistyössä. Nykyään pelaa samaan pussiin muiden kanssa koska on pakko. NSA ja GCHQ kehittävät noita reikiä ihan työkseen, eivätkä he kerro muille koska se on tabu.
Tässä on kartta mistä voi seurata Wcrypt viruksen leviämistä https://intel.malwaretech.com/pewpew.html painaa vasemmalta ylhäältä connect.
Nää älykodinkoneet on mahtavia.
Vituttais jos jääkaapis olis viikonloppuna kaljaa ja haittaohjelma olis lukinnu oven
Vituttais jos jääkaapis olis viikonloppuna kaljaa ja haittaohjelma olis lukinnu oven
Vituttais jos jääkaapis olis viikonloppuna kaljaa ja haittaohjelma olis lukinnu oven
 sorkkarauta avuksi. Ei kait se haittaohjelma soita poliisia paikalla vaikka murtautuisit sisälle.
sorkkarauta avuksi. Ei kait se haittaohjelma soita poliisia paikalla vaikka murtautuisit sisälle.Tietoturva-asiantuntijat: Kyberhyökkäyksellä mahdollinen yhteys aiempaan hyökkäykseen, josta epäillään Pohjois-Koreaa
Viikonloppuna räjähdysmäisesti levinneen WannaCry-haittaohjelman ja bangladeshilaisesta pankista viime vuonna kymmeniä miljoonia varastaneen ohjelman koodinäytteistä on löytynyt ilmeisiä yhtäläisyyksiä.
http://www.hs.fi/ulkomaat/art-2000005212496.html
Viikonloppuna räjähdysmäisesti levinneen WannaCry-haittaohjelman ja bangladeshilaisesta pankista viime vuonna kymmeniä miljoonia varastaneen ohjelman koodinäytteistä on löytynyt ilmeisiä yhtäläisyyksiä.
http://www.hs.fi/ulkomaat/art-2000005212496.html
http://spectrum.ieee.org/view-from-...rcriminals-and-why-engineers-are-easy-to-foolThe future of cybersecurity is in the hands of hardware engineers. That’s what Scott Borg, director of the U.S. Cyber Consequences Unit, told 130 chief technical officers, engineering directors, and key researchers from MEMS and sensors companies and laboratories Thursday morning.
Borg, speaking at the Mems and Sensors Technical Congress held on the campus of Stanford University, warned that “the people in this room are now moving into the crosshairs of cyberhackers in a way that has never happened before.”
And Borg should know. He and his colleagues at the Cyber Consequences unit (a nonprofit research institute) predicted the Stuxnet attack and some major developments in cybercrime over the last 15 years.
Increasingly, hackers are focusing on hardware, not on software, particularly equipment in industry, he indicated.
Tyrsky
Eversti
Nyt on korkea aika siirtyä uniikkeihin salasanoihin (jos ei sitä ole vielä tehnyt!). Täältä voi tarkistaa oman rekisteröinneissä käytetyn sähköpostiosoitteen tilanteen: https://haveibeenpwned.com/
Omia tunnareita ei ole ollut mukana noissa korkkauksissa, mutta esimerkiksi meidän teini.
Omia tunnareita ei ole ollut mukana noissa korkkauksissa, mutta esimerkiksi meidän teini.
Another BIG reason to change your passwords immediately!
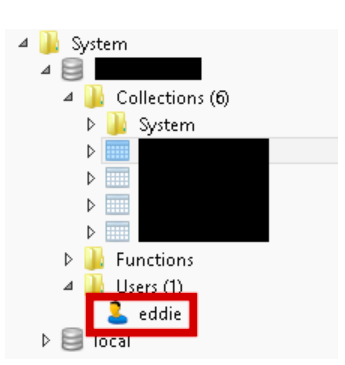
omeone (I call him Eddie, after a name found in database credentials) has put together a giant database containing more than 560 millions emails and passwords collected from variety of sources. That kind of stuff has been floating around the web for a couple of years already, until recently, when it started to appear in forms of “combo lists”
Troy Hunt did a great job describing all details about that, so this is why I have reached out to him first to see if this dump is something special.
After running a sample set at his HIBP project, Troy identified 243,692,899 unique emails, with almost every single address is already in HIBP, mostly centred around the big incidents.

And while it is not a news itself, the availability of this data almost publicly (I mean, unprotected MongoDB equals publicly) is alarming.
During our research we were surprised to see as many as 313 large databases, with size over 1GB, with several terabytes of data, hosted in US, Canada and Australia.
The database in question is hosted on a cloud-based IP, and it is unclear who actually owns it. We sent notification email to the hosting provider, but usually it is not the quickest way to shut it down.
After a series of ‘ransomware’ attacks targeted on MongoDBs left without authorization in the beginning of this year, I was not sure if somebody still uses early versions of Mongo where default configuration is possible. It appears that “Eddie” did.
Database is 75+ gigs in size and contains data structured in readable json format which included at least 10 previously leaked sets of data from LinkedIn, Dropbox, Lastfm, MySpace, Adobe, Neopets. RiverCityMedia, 000webhost, Tumblr, Badoo, Lifeboat etc.
The lesson here is simple: most likely, your password is already there and somebody might be trying to use this just now. So isn't that a good time to change it now?
--
Attention - Portions of this article may be used for publication if properly referenced and credit is given to Kromtech Security Research Center.
Nenialas Idook
Kapteeni
Twiittiketju Venäjän Ukrainassa käyttämistä menetelmistä matkapuhelinten paikantamiseen ja paikannustietojen käyttämiseen:
Lisää tietoja napsauttamalla twiittiä.
Johtopäätös lopussa: joko katkaise virta puhelimesta ja poista SIM-kortti tai mieluummin jätä koko puhelin pois völjystä, kun menet rintamalle.
Lisää tietoja napsauttamalla twiittiä.
Johtopäätös lopussa: joko katkaise virta puhelimesta ja poista SIM-kortti tai mieluummin jätä koko puhelin pois völjystä, kun menet rintamalle.
Shadow Brokers seems to be pleased. Se päivä kun he jäävät kiinni tulee olemaan mielenkiintoinen ja uskon, että juuri tämä kuukausimalli tulee olemaan heidän kompastuskivi. Olen aivan tasa varma, että FBI aikoo käyttää tätä hyväkseen.
https://www.theguardian.com/technol...ens-issue-more-leaks-hacking-tools-ransomwareThe hacking group that says data they released facilitated the WannaCry ransomware attack has threatened to leak a new wave of hacking tools they claim to have stolen from the US National Security Agency.
The so-called Shadow Brokers, who claimed responsibility for releasing NSA tools that were used to spread the WannaCry ransomware through the NHS and across the world, said they have a new suite of tools and vulnerabilities in newer software. The possible targets include Microsoft’s Windows 10, which was unaffected by the initial attack and is on at least 500m devices around the world.
In a blog post written in their trademark broken English, the group said they had more so-called Ops Disks, which they said were also stolen from the NSA. They also claimed to have exploits for web browsers, routers, smartphones, data from the international money transfer network Swift and “compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs”.
In the post, which will worry security agencies and companies worldwide, the Shadow Brokers said: “In June, TheShadowBrokers is announcing ‘TheShadowBrokers Data Dump of the Month’ service. TheShadowBrokers is launching new monthly subscription model. Is being like wine of month club. Each month peoples can be paying membership fee, then getting members only data dump each month. What members doing with data after is up to members.”
Umkhonto
Ylipäällikkö
Nenialas Idook
Kapteeni
Nää älykodinkoneet on mahtavia.
Vituttais jos jääkaapis olis viikonloppuna kaljaa ja haittaohjelma olis lukinnu oven
Eipä tosiaan kovin kauaa tarvinnut aikanaan funtsia, liitänkö television talon Wi-Fiin vai hoidanko nettitelkkarin/telkkarin päivitykset piuhallisella nettiyhteydellä. Aika lailla epäilyttää jatkuvasti netissä kiinni oleva telkkari, jossa ei ole minkäänlaista palomuuria tai muuta suojausta.
https://threatpost.com/eternalrocks-worm-spreads-seven-nsa-smb-exploits/125825/Someone has stitched together seven of the Windows SMB exploits leaked by the ShadowBrokers, creating a worm that has been spreading through networks since at least the first week of May.
Researcher Miroslav Stampar, a member of the Croatian government’s CERT, captured a sample of the worm last Wednesday in a Windows 7 honeypot he runs, and posted a report over the weekend on his Github page.
http://www.defenseone.com/technology/2017/05/who-are-shadow-brokers/138088/?oref=d-riverIn 2013, a mysterious group of hackers that calls itself the Shadow Brokers stole a few disks full of National Security Agency secrets. Since last summer, they’ve been dumping these secrets on the internet. They have publicly embarrassed the NSA and damaged its intelligence-gathering capabilities, while at the same time have put sophisticated cyberweapons in the hands of anyone who wants them. They have exposed major vulnerabilities in Cisco routers, Microsoft Windows, and Linux mail servers, forcing those companies and their customers to scramble. And they gave the authors of the WannaCry ransomware the exploit they needed to infect hundreds of thousands of computer worldwide this month.
After the WannaCry outbreak, the Shadow Brokers threatened to release more NSA secrets every month, giving cybercriminals and other governments worldwide even more exploits and hacking tools.
Who are these guys? And how did they steal this information? The short answer is: We don’t know. But we can make some educated guesses based on the material they’ve published.
System admin ei ole sama kuin tietoturvaspesialisti, mutta ei haittaa jos sysadmin tietää tietoturvasta sekä pystyy siihen vaikuttamaan.
https://it.slashdot.org/story/17/05...ity-staff-waste-time-fixing-other-it-problemsA new survey of security professionals reveals that 83 percent say colleagues in other departments turn to them to fix personal computer problems. The study by security management company FireMon shows a further 80 percent say this is taking up more than an hour of their working week, which in a year could equate to more than $88,000. For organizations, eight percent of professionals surveyed helping colleagues out five hours a week or more could be costing over $400,000. Organizations are potentially paying qualified security professionals salaries upwards of $100,000 a year and seeing up to 12.5 percent of that investment being spent on non-security related activities.
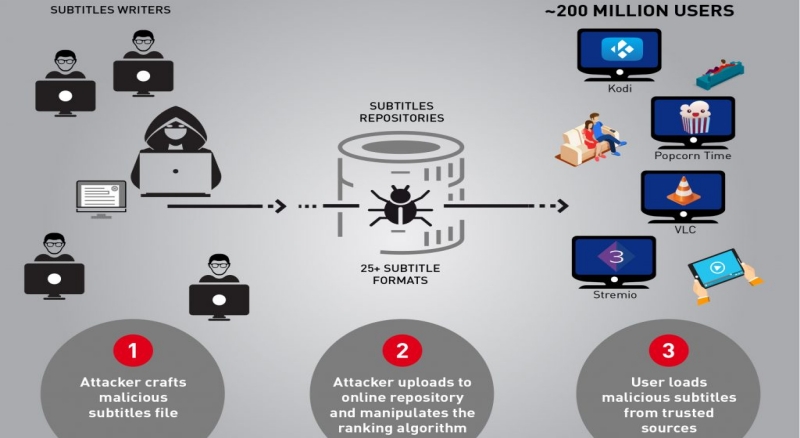
http://hackaday.com/2017/05/25/hacked-by-subtitles/CheckPoint researchers published in the company blog a warning about a vulnerability affecting several video players. They found that VLC, Kodi (XBMC), Popcorn-Time and strem.io are all vulnerable to attack via malicious subtitle files. By carefully crafting a subtitles file they claim to have managed to take complete control over any type of device using the affected players when they try to load a video and the respective subtitles.
According to the researchers, things look pretty grim:
We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years. (…) Each of the media players found to be vulnerable to date has millions of users, and we believe other media players could be vulnerable to similar attacks as well.
One of the reasons you might want to make sure your software is up to date is that some media players download subtitles automatically from several shared online repositories. An attacker, as the researchers proved, could manipulate the website’s ranking algorithm and not only would entice more unsuspecting users to manually download his subtitles, but would also guarantee that his crafted malicious subtitles would be those automatically downloaded by the media players.
No additional details were disclosed yet about how each video player is affected, although the researchers did share the details to each of the software developers so they can tackle the issue. They reported that some of the problems are already fixed in their current versions, while others are still being investigated. It might be a good idea to watch carefully and update your system before the details come out.
VLC ajoi tietoturva päivityksen tälle bugille eilen.
NTP vuotaa privaattidataa mahdolliselle kolmannelle osapuolelle (man-in-the-middle)
http://www.theregister.co.uk/2017/05/29/network_time_protocol_updated_to_spookharden_user_comms/The Internet Engineering Task Force has taken another small step in protecting everybody's privacy – this time, in making the Network Time Protocol a bit less spaffy.
This Internet Draft, published last week, calls for changes in Network Time Protocol (NTP) clients – and devs will be pleased to hear it won't be that difficult to implement.
As the draft explains, the RFCs that define NTP have what amounts to a convenience feature: packets going from client to server have the same set of fields as packets sent from servers to clients.
A lot of that information is specific to packets that originate from the server (mode 4, server-to-client responses; mode 5, broadcast packets; and modes 1/2, packets between peers).
The same fields appear in client-to-server packets (mode 3), they're not necessary, and the draft says they're a privacy risk to users.
“Populating these fields with accurate information is harmful to privacy of clients because it allows a passive observer to fingerprint clients and track them as they move across networks”.
The header fields in question are “Stratum, Root Delay, Root Dispersion, Reference ID, Reference Timestamp, Origin Timestamp, and Receive Timestamp”.
The Origin Timestamp and Receive Timestamp offer a handy example or a “particularly severe information leak”. Under NTP's spec (RFC 5905), clients copy the server's most recent timestamp into their next request to a server – and that's a boon to a snoop-level watcher.
“Therefore, when a client moves between networks, a passive observer of both network paths can determine with high confidence that the old and new IP addresses belong to the same system by noticing that the transmit timestamp of a response sent to the old IP matches the origin timestamp of a request sent from the new one.”
Because the fields are there, clients populate them with accurate information; the draft says client developers should, instead, set the fields to zero – and it shouldn't break anything, because as the draft states, “Server implementations never need to inspect them, and they can achieve nothing by doing so”.
http://www.reuters.com/article/us-china-cyber-law-idUSKBN18P0G9China, battling increased threats from cyber-terrorism and hacking, will adopt from Thursday a controversial law that mandates strict data surveillance and storage for firms working in the country, the official Xinhua news agency said.
The law, passed in November by the country's largely rubber-stamp parliament, bans online service providers from collecting and selling users' personal information, and gives users the right to have their information deleted, in cases of abuse.
"Those who violate the provisions and infringe on personal information will face hefty fines," the news agency said on Monday, without elaborating.
Reuters reported this month that overseas business groups were pushing Chinese regulators to delay implementation of the law, saying the rules would severely hurt activities.
Until now, China's data industry has had no overarching data protection framework, being governed instead by loosely defined laws.
However, overseas critics say the new law threatens to shut foreign technology companies out of sectors the country deems "critical", and includes contentious requirements for security reviews and data stored on servers in China.

