Yhdysvaltain sotilaiden GPS-tallennetut juoksulenkit paljastavat arkaluonteista tietoa Lähi-Idästä – ”Tukikohdat ovat kartalla selkeästi tunnistettavissa”
20-vuotias australialaisopiskelija havaitsi, että Yhdysvaltain armeijan sotilastukikohtien päätteleminen fitness-sovelluksen kartalta ei ole kovin vaikeaa.
https://www.hs.fi/ulkomaat/art-2000005543571.html
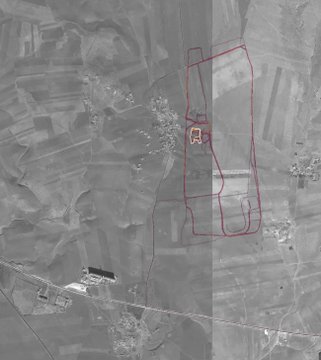
Yhdysvaltalaissotilaiden lenkkeilyreitit paljastavat Yhdysvaltojen salaisten sotilastukikohtien paikat. Stravan kartta on Afganistanista Helmlandin maakunnasta, jossa juoksulenkit ovat vaikuttaneet olevan yksinomaan ulkomaalaisten sotilaiden. (KUVA: STRAVA)
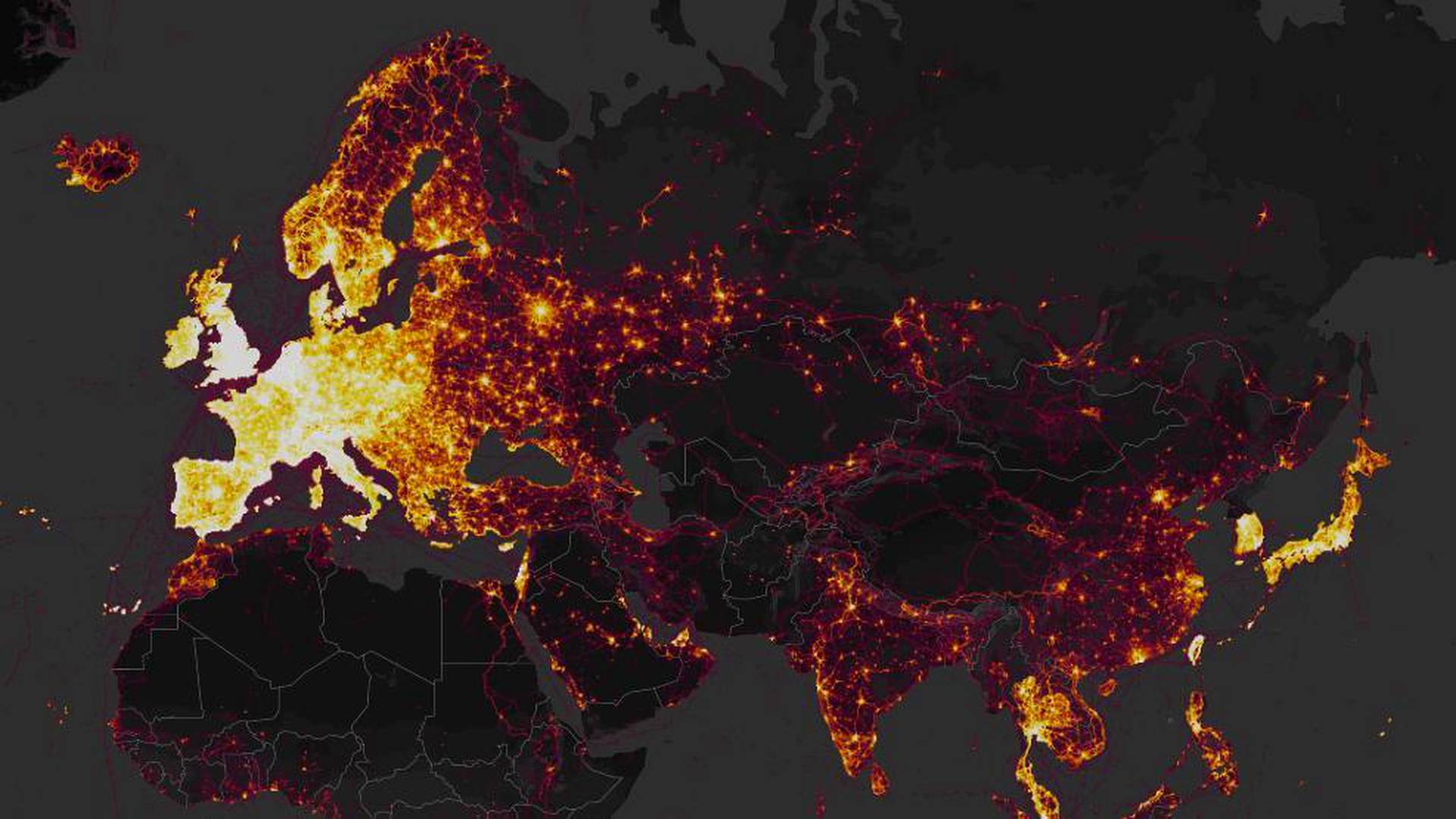
LENKKEILIJÖIDEN suosima Strava-sovellus julkaisi yli kolme triljoonaa datapistettä, joiden kautta käyttäjien juoksu- tai pyöräilylenkit ovat kulkeneet ympäri maailmaa. Asiasta on huolestunut eritoten Yhdysvaltain armeija.
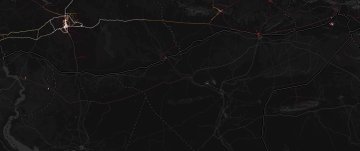
Yhdysvaltain armeijalle julkiset tiedot ovat erittäin kiusallisia, sillä kartta näyttää paljastavan yksityiskohtaista tietoa maan sotilastukikohdista. Kartasta pystyy mahdollisesti päättelemään esimerkiksi Syyrian, Irakin ja Afganistanin tukikohtien sijainteja.
Näyttää siltä, että monet sotilaat ovat lenkkeilleet tukikohtien ympärillä siten, että heidän sijaintitietonsa ovat olleet julkisia ja ne ovat tallentuneet kaikkien nähtäville Stravan karttaan.
Strava on älypuhelimessa toimiva sovellus, joka helpottaa käyttäjän liikunnan seuraamista tallentamalla tietoja lenkeistä internetiin. Esimerkiksi lenkkien reitit piirtyvät kartalle. Sovelluksessa on mahdollista jakaa tiedot myös kavereille tai jopa maailmanlaajuiselle yleisölle.
Asiasta ovat kertoneet esimerkiksi
The Guardian,
BBC,
The Washington Postja uutistoimisto AFP.
20-VUOTIAS australialaisopiskelija
Nathan Ruserhuomasi ensimmäisten joukossa, miten kartalta erottuu salaisia tietoja.
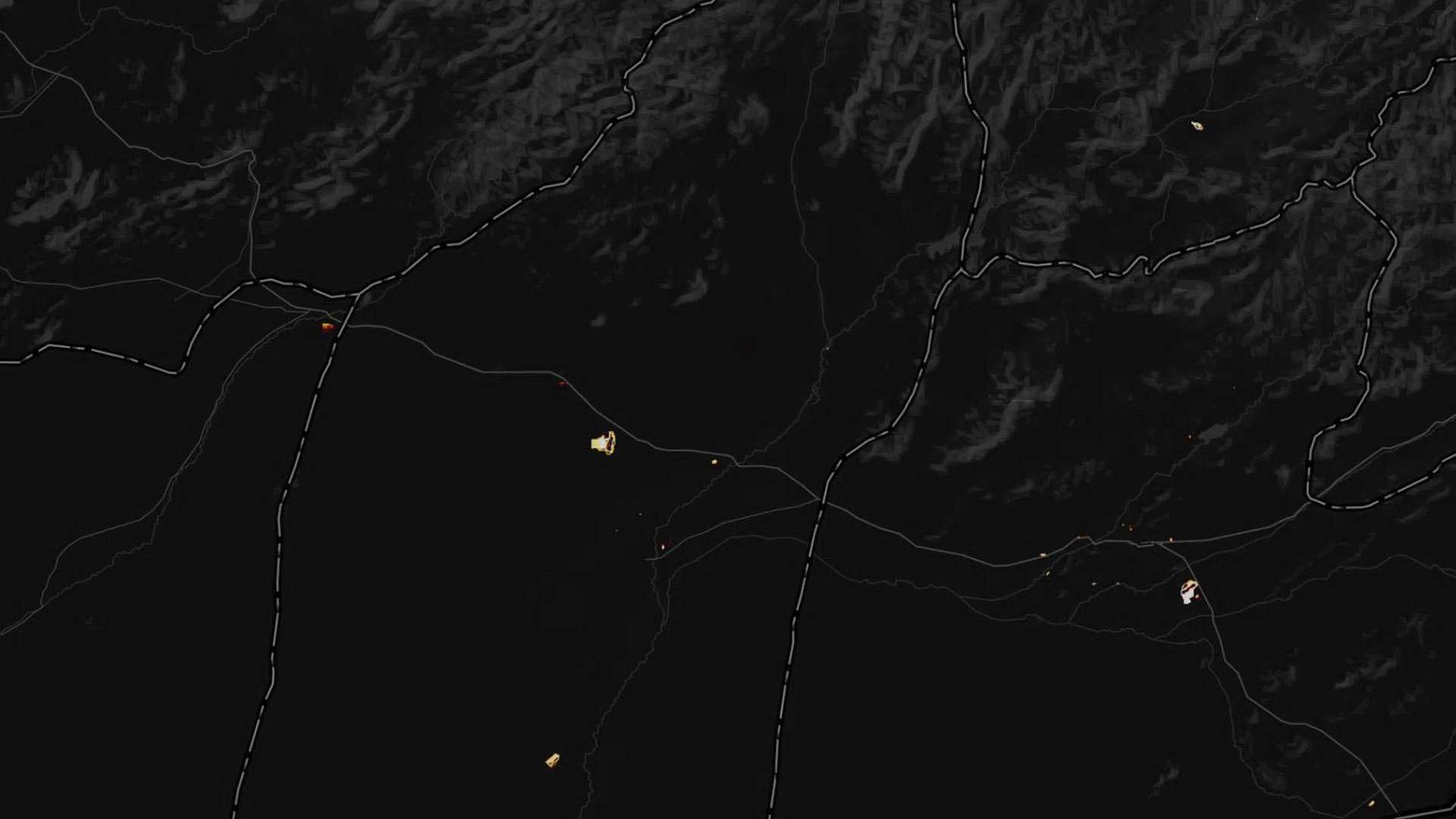
”Yhdysvaltojen tukikohdat ovat kartalla selvästi tunnistettavissa ja kartoitettavissa”, Ruser sanoi The Guardianille.
Ruser kuvailee, että lämpökartalta suorastaan loistavat Yhdysvaltain sotilastukikohtien ympäristöt.
”Jos sotilaat käyttävät sovellusta kuten tavalliset ihmiset, se on erityisen vaarallista”, Ruser totesi.
Yhdysvaltain keskushallinnon tiedottaja
John Thomas kertoi The Washington Postille, että maan armeija alkaa tutkia kartan julkaisun vaikutuksia. Samoin tiedotti Yhdysvaltain puolustusministeriö.
USEISSA kartalla näkyvissä paikoissa on ongelmana se, ettei alueella ole juurikaan GPS-tallennettuja reittejä, joten sotilaiden lenkkeilyt tietyillä alueilla erottuvat selvästi. Strava-juoksusovellus julkaisi vain julkiseksi asetettuja tietoja, mutta vaikuttaa siltä, että suuri osa sotilaista on pitänyt asetuksensa julkisina.
Päätelmiä sotilastukikohtien sijainneista vahvistaa se, että tietyillä alueilla näkyvistä henkilöistä huomattava määrä näyttää olevan sotilashenkilöitä.
Tällainen paikka löytyy esimerkiksi Afganistanista Helmlandin maakunnasta, jossa lenkkeilijät vaikuttavat olevan yksinomaan ulkomaalaisia sotilaita.
Uusin versio kartasta julkaistiin jo marraskuussa 2017, mutta sen vaikutuksia on nostettu esille vasta nyt. Karttaa pääsee katsomaan kuka tahansa
Stravan verkkosivuilta.
Yhdysvaltain keskushallinnon tiedottaja
John Thomas kertoi The Washington Postille, että maan armeija alkaa tutkia kartan julkaisun vaikutuksia. Samoin tiedotti Yhdysvaltain puolustusministeriö.
USEISSA kartalla näkyvissä paikoissa on ongelmana se, ettei alueella ole juurikaan GPS-tallennettuja reittejä, joten sotilaiden lenkkeilyt tietyillä alueilla erottuvat selvästi. Strava-juoksusovellus julkaisi vain julkiseksi asetettuja tietoja, mutta vaikuttaa siltä, että suuri osa sotilaista on pitänyt asetuksensa julkisina.
Päätelmiä sotilastukikohtien sijainneista vahvistaa se, että tietyillä alueilla näkyvistä henkilöistä huomattava määrä näyttää olevan sotilashenkilöitä.
Tällainen paikka löytyy esimerkiksi Afganistanista Helmlandin maakunnasta, jossa lenkkeilijät vaikuttavat olevan yksinomaan ulkomaalaisia sotilaita.
Uusin versio kartasta julkaistiin jo marraskuussa 2017, mutta sen vaikutuksia on nostettu esille vasta nyt.
Karttaa pääsee katsomaan kuka tahansa
Stravan verkkosivuilta.




 Nathan Ruser@Nrg8000
Nathan Ruser@Nrg8000