Joka on myös kyseisen paatin kotisatama. Eikös tuo liki törmäys tapahtunut jossain Filippiinien lähistöllä eli kaukana Vladovostokista.
Filippiinien merellä, 1400 merinpeninkulmaa pyöreesti.
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
Joka on myös kyseisen paatin kotisatama. Eikös tuo liki törmäys tapahtunut jossain Filippiinien lähistöllä eli kaukana Vladovostokista.
Niinhän ne tekee, mutta riippuu todellakin vastustajasta ja paikasta. Tuo oli kansainvälisillä vesillä ja vastassa USA, siinä on vähän sen makua että kipparilla muutama pullo vodkaa alla ja sen voimalla uhotaan.
Aina kun näitä käy, on se riski että joku mokaa ja sitten voi olla helvetti irti, sitäköhän ne hakee.
Jospa Putin haluaa neuvottelupöytään Trumpin kanssa... hieman heruttelemaanSiksi kylmänsodan vuosina NL ja USA neuvottelivat yhteiset toimintaohjeet, jotka estivät matalalla yli lentelyn ja tuollaisen.
Riskit eskalaatioon olivat liian suuret. Nyt venäjä on alkanut taas pelleillä.
Jospa Putin haluaa neuvottelupöytään Trumpin kanssa... hieman heruttelemaan

Tuosta keissistä Wikipedia kertoo:31 vuotta sitten meni näin
Aika kiltti on tuollainen pieni törmäys reaktiona, kun tunkeudutaan aluevesille provosointi yms. mielessä tärkeän tukikohdan edustalla.In February 1988, Caron, again operating with Yorktown, entered Soviet 12 miles (19 km) territorial waters limit in the Black Sea off the Crimean Peninsula. Under international law, this act could be permissible if the ship was progressing from one point in international waters to another point in international waters via the shortest course possible, but according to the Soviet Union, it was the right of the USSR to authorize or prohibit travel in selected areas within the 12 mile limit. The United States however did not recognize the Soviet claim in this case. To prevent it from becoming accepted precedent, the US Navy claimed that it had sailed warships through such areas at regular intervals in the past in accordance with established international law.
Tuosta keissistä Wikipedia kertoo:
Aika kiltti on tuollainen pieni törmäys reaktiona, kun tunkeudutaan aluevesille provosointi yms. mielessä tärkeän tukikohdan edustalla.
https://arstechnica.com/information...sored-hackers-attacked-rival-espionage-group/If nation-sponsored hacking was baseball, the Russian-speaking group called Turla would not just be a Major League team—it would be a perennial playoff contender. Researchers from multiple security firms largely agree that Turla was behind breaches of the US Department of Defense in 2008, and more recently the German Foreign Office and France’s military. The group has also been known for unleashing stealthy Linux malware and using satellite-based Internet links to maintain the stealth of its operations.
Now, researchers with security firm Symantec have uncovered evidence of Turla doing something that would be a first for any nation-sponsored hacking group. Turla, Symantec believes, conducted a hostile takeover of an attack platform belonging to a competing hacking group called OilRig, which researchers at FireEye and other firms have linked to the Iranian government. Symantec suspects Turla then used the hijacked network to attack a Middle Eastern government OilRig had already penetrated. Not only would the breach of OilRig be an unprecedented hacking coup, it would also promise to make the already formidable job of attribution—the term given by researchers for using forensic evidence found in malware and servers to pin a hack on a specific group or nation—considerably harder.

Tämä kirja kertoo ainutlaatuisella tavalla Venäjän turvallisuuspoliittisen eliitin maailmankuvasta ja suurstrategisesta ajattelusta Krimin palauttamisen jälkeen. Maapallo on siirtynyt informaatiovastakkainasetteluun, jossa valtioiden informaatiosuvereniteetti korostuu. Hybridisota on valtioiden välisten suhteiden uusi muoto, jossa sodan ja rauhan välinen raja häviää. Lontoosta johdettu hybridisota sai aikaan Venäjän imperiumin hajoamisen 1917 ja Neuvostoliiton romahduksen 1991. Nyt länsimaat uhkaavat Venäjää värivallankumouksilla, terrorismilla ja informaatiovaikuttamisella. Venäjän on kehitettävä informaatiopuolustustaan ja kansainvälisen yhteisön säädeltävä hybridisodankäyntiä sekä edistettävä informaatioaseistariisuntaa. Kirjoittaja on laatinut suomalaiselle lukijalle esipuheen, jossa käsitellään Suomen ja Venäjän suhteiden erityispiirteitä.
Professori, akateemikko Igor Panarin (s. 1958) on Venäjän johtava informaatio- ja hybridisodan tutkija, psykologian ja valtiotieteen tohtori. Panarin valmistui Neuvostoliiton turvallisuuskomitean (KGB) viestitoiminta-akatemiasta 1976 ja siirtyi 1991 Venäjän hallituksen viestintälaitoksen (FAPSI) palvelukseen, tehtävänään informaatiovirtojen strateginen analyysi. Panarin on kehittänyt Venäjän strategista informaatiopuolustusta ja toiminut Venäjän hallituksen luottamustehtävissä.
Kirjailija: Igor Panarin
Alaotsikko: Historia, teoria ja käytäntö
Kieli: Suomi
Julkaistu: 2019-01-01
Kääntäjä: Armas Mashin
ISBN: 9789525412765
Kustantaja: Johan Bäckman Publications
Sivumäärä: 380
Paino: 570 grammaa
https://www.wired.co.uk/article/russia-facebook-atlantic-council-disinformationResearchers have uncovered a network of likely Russia-based fake profiles promoting disinformation on online forums and social platforms as recently as last month. The accounts spread forged documents and false rumours, including about an anti-Brexit plot to murder Boris Johnson.
The Atlantic Council’s Digital Forensic Research Lab (DFRLab) started an investigation following Facebook’s removal of a small cluster of 16 suspected Russian fake accounts in early May 2019. After a closer analysis of the banned accounts, the researchers unearthed a much wider operation – across 30 social networks and blogging platforms, and nine languages – aimed at influencing online conversations about topics including Brexit, Northern Ireland, the European elections, immigration, UK-US relations, the turmoil in Venezuela and other foreign policy issues.
According to a DFRLab report on the investigation, the operation “was run by a persistent, sophisticated, and well-resourced organization, possibly an intelligence agency”, but its posts failed to catch on online, achieving only limited reach in all but one case. Unlike previous influence operation, the big social networks were a sideshow to a campaign conducted mostly on blogging sites, subreddits, and online forums.
“Most of the operations we’ve seen so far focused on Facebook and Twitter. This operation was almost entirely posted on other platforms, and barely used the main platforms,” says Ben Nimmo, a senior fellow for Information Defence at the DFRLab. “It also made heavy use of forged documents and outright falsehoods. Other operations have focused on half-truths, and biased or divisive content. The sheer volume of fakery in this operation was remarkable.”
Some of the false stories felt almost blatantly far-fetched. In one egregious instance in August 2018, fake accounts alleged that Spanish intelligence agencies had discovered a remainer plot to assassinate Brexit-backing Conservative politician – and probable next UK prime minister – Boris Johnson.
A Spanish-speaking Facebook account initiated the hoax on August 8, sharing a forged letter in which Spain’s foreign minister – whose name was misspelled in the signature – detailed the assassination plot. The rumour was later reposted on six subreddits and three Spanish-language forums, before being translated into English and repurposed for blogging platform Medium on August 13. The article, and a related meme juxtaposing the Spanish “letter”, an image of Johnson in the crosshairs and a photoshopped image of a dejected Johnson in a red jumper saying “Guess I’ll die”, was again shared on several online forums Facebook – but failed to spread online.
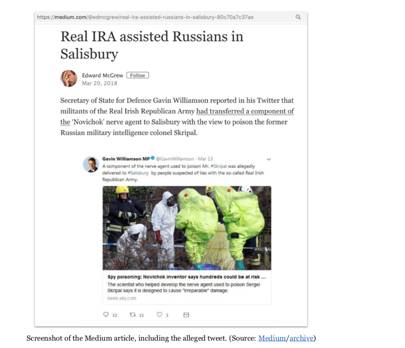
The Johnson assassination hoax followed a template typical of the entire operation. A false story would be planted by newly-created burner accounts sharing forged documents, and then amplified and expanded by accounts in multiple languages, in hopes that it would find its way to the mainstream media. Beside the Boris Johnson case, information operations targeting Northern Ireland followed a similar pattern. In August 2018, some accounts shared a screenshot of a false email exchange between the leader of the Democratic Unionist Party, Arlene Foster, and the EU chief Brexit negotiator, Michel Barnier, in which the two appeared to engage in a secret negotiation behind Theresa May’s back. Other Northern Ireland-focused disinformation bouts alleged that the IRA had helped Russia carry out the Salisbury poisoning, and that the (Catholic) Real IRA was recruiting “Islamic radicals” among its ranks.
A fraudulent letter also featured in the network’s attempts to influence the European Parliament elections in May 2019. On May 21, users on blogging platforms Medium, canalblog, and meinbezirk.at posted articles in French, German, and broken English claiming that “liberal forces” in the European Union had launched a “war against the right.” The articles were centred on a screenshot of a letter allegedly written by Italian-Swedish MEP Anna Maria Corazza Bildt. The forged letter – written in poor, non-native Swedish – called for “resolute and united” cooperation between European liberals and conservatives against the far right and praised the “well-organized work of the German media” against a far-right politician in that country.
Citing the letter, the blogs attacked a “desperate and oftentimes unlawful informational war […] being made against the forces that try to defend national interests of European countries.”
All three articles sourced the “letter” to a separate Medium post, dated May 16, and published by a user account called “Tom Welch.” The account posted only once and wrote in broken English, using language formulations common to Russian.
A scan of the three articles using the online tool BuzzSumo showed that none of them were shared online. That was despite the fact that one Twitter account linked to the operation posted it 16 times, tagging politicians from Germany’s far-right AfD party in order to elicit a reaction.
The operation's overall failure to get traction, according to Nimmo, was mostly a result of its painstaking attempts to cover its tracks.
“The great irony is that this operation tried so hard to hide that it hid its own stories. Almost every post was made by a single-use account that was created that day, posted once, and then abandoned. That’s completely contrary to the way you work on social media, where the whole point is to develop a personality and a track record,” he says.
“On the down side, it means that taking down these accounts will have less impact on the operation, because the operators have effectively burned them already. But on the plus side, it means that most of their stories crashed before they even took off.”
One notable exception was a story targeting Germany, alleging that an Arabic-language forum had published a “guide for migrants” training immigrants to get away with crimes including “sexual molestation of German women.” The hoax caught the eye of German far-right news website Journalistenwatch, which picked up the story and boosted its diffusion online.
DFRLab
The DFRLab, like Facebook, is confident that the operation originated in Russia. Many of the topics around which the network spread disinformation – Ukraine, Armenia, opposition to NATO – are traditionally aligned with Moscow’s foreign policy goals; several language errors spotted in the shared posts, such as the omission of articles or the usage of non-standard idioms, suggest that they might have been poorly translated from Russian texts. The researchers also spotted parallels between the network’s modus operandi and that of “Operation Infektion” a disinformation campaign orchestrated by the KGB in the 1980s, which accused the US of creating the AIDS virus. “[Operation Infektion] planted the fake story in distant media before amplifying it through Soviet channels: it ultimately spread through genuine news media,” the report says.
According to the DFRLab, while it seems confirmed that the operation works out of Russia, it does not necessarily follow that it is backed by the Kremlin. “There is, of course, a significant difference between operating from Russia and having any association with the Russian state. There is insufficient open-source evidence to make a definitive attribution at this stage,” the report says.
“The sheer scale and ambition of the operation, however, mean that it is unlikely to have been attempted by a small or ad hoc group. [The operation has ] significant resources, not only in terms of manpower and time, but in terms of skills.”
At the time the report was released, the operation was still ongoing.
Onkos tuo se sama kirja, jonka jokin iso suomalainen kauppaketju juuri poisti myynnistä? Joku oli vihjaissut heille.Hupskeikkaa, mikäs se sieltä pilkahtaa, etteikö olisi Bäckmanilaista vaikuttamista parhaimmillaan: https://www.adlibris.com/fi/kirja/hybridisodat-9789525412765
Törmäsin tähän Facebook-mainoksen kautta, joten tätä taidetaan puskea tähän suuntaan varsin paljon.
Hupskeikkaa, mikäs se sieltä pilkahtaa, etteikö olisi Bäckmanilaista vaikuttamista parhaimmillaan: https://www.adlibris.com/fi/kirja/hybridisodat-9789525412765
Törmäsin tähän Facebook-mainoksen kautta, joten tätä taidetaan puskea tähän suuntaan varsin paljon.


https://www.newscientist.com/articl...-radiation-leak-traced-to-facility-in-russia/The source of a gigantic, mysterious leak of radioactive material that swept across Europe in 2017 has been traced to a Russian nuclear facility, which appears to have been preparing materials for experiments in Italy.
The leak released up to 100 times the amount of radiation into the atmosphere that the Fukushima disaster did. Italian scientists were the first to raise the alarm on 2 October, when they noticed a burst of the radioactive ruthenium-106 in the atmosphere. This was quickly corroborated by other monitoring laboratories across Europe.
Georg Steinhauser at Leibniz University Hannover in Germany says he was “stunned” when he first noticed the event. Routine surveillance detects several radiation leaks each year, mostly of extremely low levels of radionuclides used in medicine. But this event was different.
“The ruthenium-106 was one of a kind. We had never measured anything like this before,” says Steinhauser. Even so, the radiation level wasn’t high enough to impact human health in Europe, although exposure closer to the site of release would have been far greater.
The Institute for Radioprotection and Nuclear Security in Paris soon concluded that the most probable source of the leak was between the Volga river and Ural mountains in Russia. This is where Russia’s Mayak facility is located. The site, which includes a plant that processes spent nuclear fuel, suffered the world’s third most serious nuclear accident in 1957.
At the time of the 2017 leak, Russian officials denied the possibility of the facility being the source, saying there were no radioactive ruthenium traces in the surrounding soil. Instead, they suggested the source may have been a radionuclide battery from a satellite burning up during re-entry into the atmosphere.
Steinhauser and his colleagues decided to investigate more thoroughly by forensically analysing 1300 measurements from hundreds of monitoring stations across Europe. They found that radiation levels in the atmosphere were between 30 and 100 times higher than those measured after Fukushima. “This was indeed quite alarming,” says Steinhauser.
Eliminate the impossible
The team excluded Romania as the source of the accident, despite the country’s high radiation levels. Each station in the country detected the radioactive plume simultaneously, which indicated the source was far enough away for it to have grown to the width of Romania.
They also excluded a satellite as the cause because space organisations didn’t report any missing at the time. The pattern of radiation through the atmosphere didn’t match the spread of radiation from a satellite’s reentry either.
Combining these findings with information on air movements and concentration levels from monitoring data, the team found clear evidence that the release happened in the Southern Urals, which is where the Mayak nuclear facility is located.
The leak was unusual because the release was limited to radioactive ruthenium. “If there is a reactor accident, one would expect the release of radioactive isotopes of many different elements,” says Steinhauser. Exactly why such a specific element was released remained a mystery until Steinhauser learned that an Italian nuclear research facility had ordered a consignment of cerium-144 from Mayak before the incident. “There are several indications that the release of ruthenium-106 was linked to this order,” he says.

Historiassa on yksi hieno tapaus kun tupolevin pommittaja päätti vetää merenpinnassa minimivauhdilla lentotukialuksen vierestä, ja upposi mereen31 vuotta sitten meni näin
https://arstechnica.com/information...hackers-using-iot-devices-to-breach-networks/Hackers working for the Russian government have been using printers, video decoders, and other so-called Internet-of-things devices as a beachhead to penetrate targeted computer networks, Microsoft officials warned on Monday.
“These devices became points of ingress from which the actor established a presence on the network and continued looking for further access,” officials with the Microsoft Threat Intelligence Center wrote in a post. “Once the actor had successfully established access to the network, a simple network scan to look for other insecure devices allowed them to discover and move across the network in search of higher-privileged accounts that would grant access to higher-value data.”
The officials continued:
After gaining access to each of the IoT devices, the actor ran tcpdump to sniff network traffic on local subnets. They were also seen enumerating administrative groups to attempt further exploitation. As the actor moved from one device to another, they would drop a simple shell script to establish persistence on the network which allowed extended access to continue hunting. Analysis of network traffic showed the devices were also communicating with an external command and control (C2) server.
Microsoft researchers discovered the attacks in April, when a voice-over-IP phone, an office printer, and a video decoder in multiple customer locations were communicating with servers belonging to “Strontium,” a Russian government hacking group better known as Fancy Bear or APT28. In two cases, the passwords for the devices were the easily guessable default ones they shipped with. In the third instance, the device was running an old firmware version with a known vulnerability. While Microsoft officials concluded that Strontium was behind the attacks, they said they weren’t able to determine what the group’s ultimate objectives were.

Ja ei kun vastaamaan soittajalle, että heti pois Ukrainan itäisiltä alueilta ja Krimiltä.Eiköhän tämä tänne kuulu. Melko röyhkeää käytöstä ryssiltä jos pitää paikkansa, ovat soitelleet hollantilaisten F-16 lentäjien vaimoille ja tyttöystäville uhkaavia puheluita 2017 kun Alankomaiden ilmavoimat suorittivat ilmatilavalvontaa Balteissa.
Kääntäjän kautta:
"The Military Intelligence and Security Service (MIVD) says it is familiar with the practices, but does not want to say anything about it. As a result, it is unclear whether, just as in 2017, when F-16s of the Royal Netherlands Air Force were active in the Baltic states, relatives of Dutch soldiers deployed are still being harassed.
At present, the air force is no longer active in Eastern Europe, but there are still 270 soldiers of the Royal Netherlands Army in Lithuania.
Unpleasant questions
Suddenly in early 2017 women and girlfriends of Dutch F-16 pilots rang the phone. On the other side of the line was someone who asked unpleasant questions about their presence in the Baltic states. For soldiers, harassment of family members is an absolute horror.
From sources within the kite community De Telegraaf understands that the phone calls started after the soldiers called home with their own device. Wives and girlfriends then received a call from someone with a Russian-sounding accent who asked what their husband was doing there? What did they think of it? And whether it would be better if he left there? Calls were called back several times."

’Russen’ intimideren vrouwen Nederlandse F-16-vliegers
Partners van Nederlandse jachtvliegers die actief waren bij de bewaking van het Baltische luchtruim zijn thuis lastiggevallen. Ze kregen herhaalde, onprettige telefoontjes van mensen met een…www.telegraaf.nl
