http://www.spacewar.com/reports/Inv...uts_second_to_none_jamming_equipment_999.htmlRussia's most advanced electronic warfare systems, Borisoglebsk-2 and Rtut-BM, add significantly to the country's defense capabilities, according to the Russian news network Zvezda. The modernization of the Russian Armed Forces has included the development of electronic warfare, the Russian news network Zvezda reported, referring to the state-of-the-art Borisoglebsk-2 and Rtut-BM systems.
The Borisoglebsk-2 is a multi-purpose electronic warfare system developed by Russia's United Instrument Manufacturing Corporation for the Russian Armed Forces. Its development started in 2004 and its evaluation testing was completed successfully in December 2010. The system was initially introduced to the Russian army in 2014.
The Borisoglebsk-2 merges four types of jamming stations into a single system with a single control console which allows the operator to take decisions within seconds. The system is mounted on nine MT-LB armored vehicles and is designed to suppress mobile satellite communications and satellite-based navigation signals.
Compared to previous jamming units, the Borisoglebsk-2 has a wider range of radio surveillance and suppression, hi-speed frequency scanning, a longer operative range and more precise radio wave emission source spatial localization.
United Instrument Manufacturing Corporation spokesman Mikhail Artyomov touted the Borisoglebsk-2 as the best electronic warfare system in the world.
"The system's combat characteristics are not just on a par with the best foreign analogues, they considerably surpass them in terms of a number of parameters. At present, our system is able to jam all modern radio communications," he said.
The Rtut-BM is another advanced Russian electronic warfare system, which is designed to protect troops and military hardware from artillery rockets and shells equipped with proximity fuses which are programmed to cause them to detonate when they are 3-5 meters from the ground.
The Rtut-BM affects the proximity of radio-controlled explosive devices, prompting them to explode at higher altitudes in order to keep troops and equipment safe. Also, the system can neutralize radio frequencies employed by the enemy's communications.
The Rtut-BM is deployed on an MT-LB armored vehicle fitted with a television antenna which provides coverage for an area of about 50 hectares (500,000 square meters) or a semi-sphere with a 400 meter radius. This system requires a crew of two men and it can be ready for jamming within 10 minutes.
Over the past three years, domestic manufacturers have supplied 22 such systems to the Russian Armed Forces, and 21 more are due to be delivered before the end of this year. As far as the Borisoglebsk-2 is concerned, more than ten such units were supplied to the Russian army between 2014 and 2015.
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
ELSO (elektroninen sodankäynti) radiotaajuuksilla: radiotiedustelu, taajuushäirintä, EMP etc
- Viestiketjun aloittaja Pyllyvaltteri
- Aloitus PVM
http://www.armyrecognition.com/armi...va-1_electronic_warfare_systems_12003161.htmlRussia’s Radio-Electronic Technologies Group (KRET) will deliver Krasukha-4 electronic warfare and Moskva-1 radio reconnaissance systems to the Russian Armed Forces in 2016, KRET First Deputy CEO Igor Nasenkov said on Friday, March 18, 2016.
The KRET Enterprise is a subsidiary of Russia’s state hi-tech corporation Rostec.
"This is classified information and these are classified contracts but I can say that we will deliver several systems," Nasenkov said at a meeting of the KRET board.
"As for the Krasukha and Moskva deliveries, we are working ahead of the schedule for the presidential order to increase the proportion of advanced military hardware in the Russian Armed Forces to 70% by 2020," he added.
According to the first deputy CEO, the KRET Enterprise has virtually accomplished the task assigned by the Russian president to deliver ground-based electronic warfare systems to the Armed Forces.
The 1RL257 or Krasukha-4 is a Russian-made mobile electronic warfare system designed and manufactured by the Company Bryansk Electromechanical Plant (KRET). The Krasukha-4 is intended to neutralize Low-Earth Orbit (LEO) spy satellites, ground-based radars and airborne radars (AWACS) at ranges between 150 to 300 kilometers.
The Moskva-1 electronic reconnaissance and control system carries out airspace radio intelligence at a distance of up to 400 km. The Moskva-1 system can accommodate more than seven electronic warfare components at once. The reconnaissance of targets takes place in a passive mode.
http://www.dn.se/nyheter/sverige/twitterkonto-hetaste-sparet-efter-attack/Yesterday, at 19:30 CET, an unprecedented DDOS attack shut down both Swedish government sites and all major news outlets, including www.aftonbladet.se, www.expressen.se, www.svd.se, www.dn.se, www.di.se and others. The attack was announced in advanced in a tweet stating 'The following days attacks against the Swedish government and media spreading false propaganda will be targeted'. A large amount of traffic was detected from Russia. Tension between Russia and Sweden has slowly but steadily intensified during the latest years, causing Swedish relocation of military forces to strategic location and increased cooperation with NATO.
Fencer
Kenraali
14.4.2016 klo 11:14
http://yle.fi/uutiset/epaily_ruotsi...komyrsky_olikin_venajan_kyberhyokkays/8810607
"Epäily: Ruotsin lentoliikenteen seisauttanut aurinkomyrsky olikin Venäjän kyberhyökkäys?
Nato-lähteet kertovat norjalaiselle AldriMer-sivustolle, että Ruotsi uskoi olevansa kyberhyökkäyksen kohteena, kun tutkajärjestelmän häiriöt seisauttivat lentoliikenteen Etelä-Ruotsissa marraskuun alussa.
Ruotsin viranomaiset varoittivat sotilasliitto Natoa käynnissä olevasta kyberhyökkäyksestä, kun suuri osa maan lentoliikenteestä seisahtui marraskuun 4. päivänä, kertoo norjalainen puolustussivusto AldriMer.no. Kaikki lentoliikenne Etelä-Ruotsista keskeytyi noin tunnin ajaksi tutkajärjestelmän häiriöiden vuoksi. Ruotsin ilmailuviraston mukaan voimakas aurinkomyrsky aiheutti häiriöt.
Ruotsi varoitti Natoa kyberhyökkäyksestä
Nimettöminä pysyttelevät Nato-lähteet kertovat AldriMerille, että Ruotsi antoi Natolle kaksi varoitusta kyberhyökkäyksestä. Ruotsi uskoi, että hyökkäystä johti hakkeriryhmä APT (Advanced Persistent Threat), joka on aiemmin yhdistetty Venäjän sotilastiedustelupalvelu GRU:hun.
Ruotsin varoitukset Natolle antoi joko Ruotsin puolustusvoimien radiosignaalitiedustelulaitos (FRA) tai tiedustelu- ja turvallisuuspalvelu (MUST). FRA, MUST tai Nato eivät kommentoi tietoja AldriMerille eivätkä sanomalehti Aftonbladetille, joka myös kirjoittaa asiasta.
Nato havaitsi Venäjän elektronista sodankäyntiä
AldriMer kertoo lisäksi, että samaan aikaan, kun Ruotsi uskoi olevansa kyberhyökkäyksen kohteena, Nato havaitsi Venäjän elektronista sodankäyntiä Itämerellä. Siihen olisi AldriMerin lähteiden mukaan kuulunut lentoliikenteen viestintäyhteyksien häirintää.
Signaali jäljitettiin suureen radiomastoon Venäjän Kaliningradissa, kertoo AldriMer.
Avaruustutkija epäilee aurinkomyrskyselitystä
Avaruustutkija piti Ruotsin ilmailuviraston selitystä tutkahäiriöiden syystä epätodennäköisenä jo marraskuussa, sillä aurinkomyrsky ei vaikuttanut mihinkään muihin maihin.
– Selitystä vastaan puhuu se, että se vaikutti vain Ruotsiin. Se ei myöskään ollut suuri avaruussäätapahtuma, vaan keskinkertainen, sanoi avaruusfyysikko Urban Brändström Avaruusfysiikan tutkimuslaitoksesta Kiirunasta Ruotsin radiolle.
– Avaruussäävaroituksia annetaan viisiasteisella mittarilla, eikä keskiviikon myrsky yltänyt edes yhteen asteeseen.
Ruotsin ilmailuvirasto aloitti selvityksen tutkajärjestelmän häiriön syystä. Se ei ole vielä valmistunut."
http://yle.fi/uutiset/epaily_ruotsi...komyrsky_olikin_venajan_kyberhyokkays/8810607
"Epäily: Ruotsin lentoliikenteen seisauttanut aurinkomyrsky olikin Venäjän kyberhyökkäys?
Nato-lähteet kertovat norjalaiselle AldriMer-sivustolle, että Ruotsi uskoi olevansa kyberhyökkäyksen kohteena, kun tutkajärjestelmän häiriöt seisauttivat lentoliikenteen Etelä-Ruotsissa marraskuun alussa.
Ruotsin viranomaiset varoittivat sotilasliitto Natoa käynnissä olevasta kyberhyökkäyksestä, kun suuri osa maan lentoliikenteestä seisahtui marraskuun 4. päivänä, kertoo norjalainen puolustussivusto AldriMer.no. Kaikki lentoliikenne Etelä-Ruotsista keskeytyi noin tunnin ajaksi tutkajärjestelmän häiriöiden vuoksi. Ruotsin ilmailuviraston mukaan voimakas aurinkomyrsky aiheutti häiriöt.
Ruotsi varoitti Natoa kyberhyökkäyksestä
Nimettöminä pysyttelevät Nato-lähteet kertovat AldriMerille, että Ruotsi antoi Natolle kaksi varoitusta kyberhyökkäyksestä. Ruotsi uskoi, että hyökkäystä johti hakkeriryhmä APT (Advanced Persistent Threat), joka on aiemmin yhdistetty Venäjän sotilastiedustelupalvelu GRU:hun.
Ruotsin varoitukset Natolle antoi joko Ruotsin puolustusvoimien radiosignaalitiedustelulaitos (FRA) tai tiedustelu- ja turvallisuuspalvelu (MUST). FRA, MUST tai Nato eivät kommentoi tietoja AldriMerille eivätkä sanomalehti Aftonbladetille, joka myös kirjoittaa asiasta.
Nato havaitsi Venäjän elektronista sodankäyntiä
AldriMer kertoo lisäksi, että samaan aikaan, kun Ruotsi uskoi olevansa kyberhyökkäyksen kohteena, Nato havaitsi Venäjän elektronista sodankäyntiä Itämerellä. Siihen olisi AldriMerin lähteiden mukaan kuulunut lentoliikenteen viestintäyhteyksien häirintää.
Signaali jäljitettiin suureen radiomastoon Venäjän Kaliningradissa, kertoo AldriMer.
Avaruustutkija epäilee aurinkomyrskyselitystä
Avaruustutkija piti Ruotsin ilmailuviraston selitystä tutkahäiriöiden syystä epätodennäköisenä jo marraskuussa, sillä aurinkomyrsky ei vaikuttanut mihinkään muihin maihin.
– Selitystä vastaan puhuu se, että se vaikutti vain Ruotsiin. Se ei myöskään ollut suuri avaruussäätapahtuma, vaan keskinkertainen, sanoi avaruusfyysikko Urban Brändström Avaruusfysiikan tutkimuslaitoksesta Kiirunasta Ruotsin radiolle.
– Avaruussäävaroituksia annetaan viisiasteisella mittarilla, eikä keskiviikon myrsky yltänyt edes yhteen asteeseen.
Ruotsin ilmailuvirasto aloitti selvityksen tutkajärjestelmän häiriön syystä. Se ei ole vielä valmistunut."
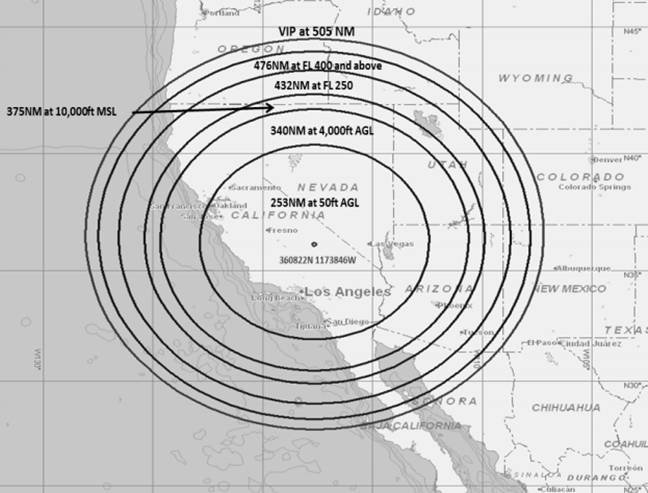
http://www.theregister.co.uk/2016/06/07/us_military_testing_gps_jamming/The US Federal Aviation Authority (FAA) is warning aircraft to stay a few hundred miles away from the Naval Air Weapons Station at China Lake, California, because the military is testing a new gizmo that disrupts GPS – and may also mess with flight control systems.
OldSkool
Kapteeni
Testialusta, lentokone-asennettu. Näin jutussa arvellaan. Eli kun asettelen foliohattua päähäni niin mutu on että jatkossa sotatoimissa lanataan koko sotilasläänin alueelta gps:t pimeiksi. Siihen vielä laajaspektrinen mobiiliverkon häirintä ja tietenkin mil tutkien ja it:n.
Eli näppituntumalla, häirintäkoneita ja tankkereita on 10x se mitä hyperhäivepommittajia. Sadassa vuodessa ilmasota on hieman muuttunut.
China Lakessa on noita "GPS Interference" testejä tehtä pitkään. Tämä ei siis ole ensimmäinen kerta eikä suinkaan mitään erityisen salaista, vaan normaalia testausta. Siellä on ainakin maa-alustalla olevia testikäyttöön tarkoitettuja GPS häirintä simulaattoreja, joilla luodaan todentuntuisia tilanteita testiammuntoja varten esim. JDAM ja JSOW asejärjestelmille. Kyseessä voi hyvin siis olla testejä joilla todennetaan GPS-laitteiden häirinnnän sietoa, eikä niinkään häirintälaitteiden testausta ja kehitystä.
Kannattaa käydä vilkuilemassa paikallisia maalilaitteita. Siellä on ainakin SA-6 ja SA-10 IT-järjestelmiä (voivat olla mock-uppejakin) ym.
GPS voidaan häiritä. Kriittiset järjestelmät käyttävät myös muita paikannuskeinoja ja häirinnällekin on vastatoimensa. Taloudellista vahinkoa on helppo tehdä, mutta todelliset kriisiajan vahingot jäävät huomattavasti pienemmiksi. Tähän pätee se sama kuin näihin "Suomi polvillaan 15 min" juttuihin eli ei ole mitään merkitystä jos se sun autonavigaattoris ei saakaan sitä sijaintia sieltä satelliitista.
Kannattaa käydä vilkuilemassa paikallisia maalilaitteita. Siellä on ainakin SA-6 ja SA-10 IT-järjestelmiä (voivat olla mock-uppejakin) ym.
GPS voidaan häiritä. Kriittiset järjestelmät käyttävät myös muita paikannuskeinoja ja häirinnällekin on vastatoimensa. Taloudellista vahinkoa on helppo tehdä, mutta todelliset kriisiajan vahingot jäävät huomattavasti pienemmiksi. Tähän pätee se sama kuin näihin "Suomi polvillaan 15 min" juttuihin eli ei ole mitään merkitystä jos se sun autonavigaattoris ei saakaan sitä sijaintia sieltä satelliitista.
Samses
Ylipäällikkö
Joku "asiantuntijaksi" väitetty venäläinen sanoo Iltikselle, että Hibinyä ei edes voi asentaa Fenceriin....
En osaa arvioida tämän informaation uskottavuutta, mutta joka tapauksessa kiinnostava artikkeli Donald Cook -tapaus nro 1:stä.
http://www.iltasanomat.fi/ulkomaat/art-2000001223784.html
En osaa arvioida tämän informaation uskottavuutta, mutta joka tapauksessa kiinnostava artikkeli Donald Cook -tapaus nro 1:stä.
http://www.iltasanomat.fi/ulkomaat/art-2000001223784.html
Nenialas Idook
Kapteeni
Joku "asiantuntijaksi" väitetty venäläinen sanoo Iltikselle, että Hibinyä ei edes voi asentaa Fenceriin....
En osaa arvioida tämän informaation uskottavuutta, mutta joka tapauksessa kiinnostava artikkeli Donald Cook -tapaus nro 1:stä.
http://www.iltasanomat.fi/ulkomaat/art-2000001223784.html
Laitoin saman uutisen Uutisia Venäjältä -ketjuun. Uutisessahan itse asiassa kerrotaan asiantuntijan sanovan, että "tällä hetkellä sitä" ei voi siihen asentaa.
Mutta tässä toisesta lähteestä tuon UUS Donald Cookin lamauttamisen debunkkaus, kret.com:
(Lihavointi minun.)Russia and India Report decided to lift the veil of secrecy and selected five most effective EW systems
Khibiny: Terror of the destroyers
This relatively small container in the shape of a torpedo is mounted on the wingtips of the aircraft and makes the sky machines invulnerable to all modern means of defence and enemy fighters. After the crew receives missile attack alert, Khibiny comes into action and covers the fighter with radio-electronic protective hood, which prevents the missile from reaching the target and makes it deviate from the course. Khibiny increases the survivability of the aircraft by 25-30 times. According to deputy general director of concern KRET (developer and manufacturer of this EW system) Vladimir Mikheev, all the fighters that Russia lost in Georgia were naked, ie. without the installed EW means, and this fact has caused the loss of the Russian military equipment.
By the way, nowadays Khibiny is being installed on Su-30, Su-34 and Su-35, so the famous April attack in the Black sea on USS Donald Cook by Su-24 bomber jet allegedly using Khibiny complex is nothing but a newspaper hoax. The destroyer's buzzing did take place. This EW system can completely neutralise the enemy radar, but Khibiny are not installed on Su-24.
http://spectrum.ieee.org/telecom/se...ofers-is-critical-to-the-future-of-navigationJust hours before U.S. president Barack Obama delivered his final State of the Union speech in January, two U.S. Navy patrol boats wandered into Iranian waters. The Iranian military intercepted the vessels and captured 10 U.S. sailors, making for an awkward moment as the president took the stage.
Without a clear explanation, the incident prompted speculation that Iran had sent false GPS signals to lure the sailors onto another course. It would not have been easy for the Iranians to hijack the GPS system—military GPS signals are heavily encrypted—but the idea wasn’t inconceivable. In 2011, Iran boasted that it had captured a highly classified drone belonging to the CIA by fooling its GPS to make it land in Iran rather than Afghanistan.
Three years before the drone’s capture, one of us (Humphreys) had developed the only publicly acknowledged GPS spoofer that could perform such a feat. A spoofer transmits false GPS signals, which to a navigation system are indistinguishable from real ones. Meanwhile, the other of us (Psiaki) was hard at work on detectors to catch spoofers in the act.
Prodded by the Iranians, the U.S. Department of Homeland Security decided to investigate spoofing soon after the drone incident. The agency invited Humphreys’s group at the University of Texas at Austin to attack a helicopter drone at White Sands Missile Range, N.M., in June 2012. The team’s mission was to force the hovering aircraft to land by sending false positional data to its GPS. The spoofer told the drone it was climbing, causing it to automatically adjust—and nearly crash into the sand.
An operator averted disaster by manually overriding the spoofed autopilot before impact. Still, the White Sands drone hack made national news and rattled lawmakers. Soon after, Humphreys appeared before a U.S. congressional committee concerned with drone safety.
Since then, GPS spoofing has continued to pose a dangerous but poorly understood threat to the trustworthiness of critical navigation systems.
To prevent spoofing, we need to understand how antagonists can corrupt GPS signals in the first place. With that knowledge, we must act quickly to develop ways to alert GPS users to these false signals.
The drone demonstration starkly indicated GPS’s vulnerabilities, but we believe that other targets are far more worrisome. Cellphone towers, stock exchanges, and the power grid all rely at least partly on GPS for precise timing. A well-coordinated spoof could interrupt communications, confuse automated financial traders, and inflict crippling power outages. In a worst-case scenario, a spoofer’s operator could overtake airplanes or ships to induce a crash, facilitate a heist, or even kidnap a VIP.

The White Rose is a 65-meter (213-foot) superyacht that relies on GPS to safely navigate the high seas. The US $80 million vessel, which boasts paintings by old masters and marble-and-gold bathrooms, belongs to a U.K. real estate tycoon. Schofield, the ship’s captain, was offering to take Humphreys out to sea to test whether his trusted ship could be spoofed.
After months of planning, the White Rose set sail in June 2013 from Monaco to Rhodes, Greece. Atop the yacht were two GPS antennas feeding received signals to a pair of standard GPS receivers on the bridge. Also on board was Humphreys’s spoofer [pdf], which contains about $2,000 worth of software and hardware, including a radio-frequency receiver, transmitter, and digital signal-processing chips.
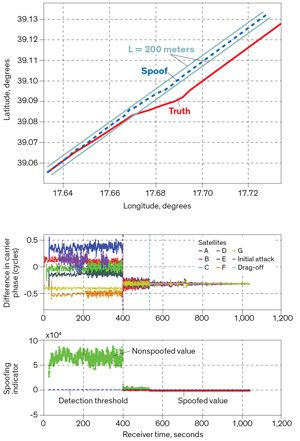
For the first portion of the trip, the yacht’s GPS receivers dutifully logged location information from several dozen satellites, as they would on any voyage. Then, on day two of the cruise, Humphreys’s team replaced the signals being received on the bridge with spoofed ones indicating that the ship was drifting 3 degrees to the left.

How did they do it? In normal operation, GPS receivers deduce their position by calculating their distance from several satellites at once. Each satellite carries an atomic clock and broadcasts its location, the time, and a signature pattern of 1,023 plus and minus signs known as a pseudorandom noise code (or PRN code). These codes identify a signal as originating from, say, satellite A versus satellite B, which is necessary because all GPS satellites broadcast civilian signals on the same frequency.
The patterns that make up PRN codes also repeat over time, and their distinctive arrangements of pluses and minuses enable GPS receivers to use them to determine the signal-transmission delay between a satellite and the receiver. A receiver uses these delays, along with the satellite positions and time stamps, to triangulate its precise location. To get a good fix, a receiver must receive signals from four or more satellites at a time—it can figure coordinates based on just three, but it needs the fourth to synchronize its inexpensive, drift-prone clock with the constellation’s precise atomic clocks.
To attack civilian receivers such as those aboard the White Rose, a spoofer’s operator figures out which GPS satellites will be in the vicinity of the target at a given time based on the satellites’ orbits. The spoofer then fabricates the PRN code for each satellite using formulas available in the public database. Next, the spoofer broadcasts faint signals carrying the same codes as all of the nearby satellites at once. The GPS receiver registers these weak signals as though they were part of the stronger, true signals transmitted by those satellites.
Then comes the delicate art of the “drag-off,” in which attackers must gently override the true signals. To do this, the spoofer’s operator gradually increases the power of the false GPS signals until the receiver catches onto these new signals. If the signal increase is too abrupt, the receiver or even the ship’s human navigators might detect something amiss. Once the receiver has latched onto the false signals, the operator can adjust the spoofer and receiver to a new set of coordinates and leave the true signals behind.
Back on the White Rose, crew members noted the apparent—but not actual—3-degree leftward drift that Humphreys’s team had fooled the ship’s receivers into recording at the start of the attack. However, the shift was so slight that the crew assumed it was due to natural forces such as water currents and crosswinds, so they adjusted the vessel slightly to the right. In reality, this corrective maneuver actually took them off course.
Earlier this year, GPS manufacturer U-blox released the first commercially available spoofing defense for consumer GPS receivers in a firmware update to its M8 line of navigation systems. The company, based in Switzerland, did not announce details about the detection method it has deployed. However, we’re pretty sure that it is distortion detection because that approach is easiest to implement through a firmware update, requiring only some additional signal-processing algorithms.
But distortion-based methods may miss attacks that they fail to catch early. Cryptographic methods are very effective (just ask the U.S. military) but require either substantial changes in how GPS signals are broadcast or an additional high-bandwidth communications link. Architects of Europe’s new global navigation satellite system [pdf], called Galileo, have embraced this approach and have tested the broadcasting of digitally encrypted signals for civilians over their system. Unfortunately, such a system would still be vulnerable to a meaconing attack.
Direction-of-arrival sensing is our method of choice, but it is typically more expensive to implement than distortion detection. The process itself is most effective when executed by multiple antennas, but large arrays can’t easily fit on handheld devices. And partial spoofing can dupe it: If a spoofer targets only one or two GPS signals instead of all signals from every satellite within range, some variance in the carrier-phase difference will persist even after the attack.
In the end, we think the strongest spoofing defenses will probably combine distortion detection and direction-of-arrival sensing. Distortion detection will help during the initial attack phases, while direction-of-arrival sensing provides a second line of defense.
However, we can’t guarantee that any such combination of solutions will be affordable for the average user. Commercial developers must amortize costs over a large number of sales, but most consumers do not need spoofing protection. It’s a safe bet that Iranian agents aren’t interested in frustrating the efforts of U.S. motorists to find trendy new restaurants or drive their children to baseball games.
For those like Schofield who have deep pockets and face real risks, at least one manufacturer already sells a two-antenna receiver that could easily be upgraded to include direction-of-arrival algorithms. That manufacturer might soon be able to market a spoofing-resistant product on the order of $10,000 per unit. Operators of commercial airliners, large ships, and automated stock traders should be willing to pay that kind of money to lock the barn without even knowing whether horse thieves lurk in the neighborhood.
In the meantime, the good news for Schofield is that in order to pull off a spoof, an attacker must be close enough to the target to determine its precise location, log the GPS satellites that the target sees, and transmit false signals to it on a direct line of sight. Fortunately, no vessels beyond the White Rose’s horizon could have executed this hack.
All of this work is just one piece of the larger challenge that faked physical signals pose to cyberphysical security. Might a hacker send a false radar signal to the automatic braking system of a high-end car and bring it screeching to a halt on a packed freeway? The possibilities are significant, growing, and alarming. We think the red-team/blue-team development strategy, in which the red team attacks a system and the blue team defends it, could be useful to others leading missions that deal with sensor deception, as we have found it to be in our work. We will be rooting for the blue teams.

http://www.armyrecognition.com/ausa...-meter_troposcatter_antenna_at_ausa_2016.htmlCubic Corporation (NYSE: CUB) today announced that its subsidiary GATR Technologies (GATR), which operates within the Cubic Mission Solutions (CMS) business division, will introduce its inflatable 4-meter GATR TropoTM antenna for the first time to the satellite communications (SATCOM) industry at the 2016 AUSA Annual Meeting and Exposition in Washington, D.C. from October 3 – 5.
The extremely portable, four-meter GATR Tropo can be packed into five cases weighing less than 620 pounds total and is fifty to eighty percent less in volume and weight than the current rigid troposcatter antennas. Troposcatter antennas transmit and receive microwave signals at beyond-line-of-sight distances, as far as 200 miles without SATCOM, by bouncing radio signals off layers of the Earth's atmosphere (troposphere).
“The debut of the four-meter GATR Tropo at AUSA is an exciting time for us as we’re introducing the most portable troposcatter antenna in the SATCOM industry,” said Paul Gierow, president of Cubic | GATR. “These antennas will better enable other types of communications for diverse missions.”
The new inflatable GATR Tropo antenna, which is available in 2.4- and four-meters, can lower operating costs for its customers as it drastically reduces shipping expenses and power requirements compared to portable, rigid tropo terminals. GATR Tropo antennas are also very reliable in extreme environments as they are able to receive tropo signals over diverse terrains when the antennas are elevated to 12 feet. The antennas can be set up and link-ready in less than 60 minutes, without the need of special tools. In addition, the modular design and dual-use parabolic antenna is mission capable for both troposcatter and standard SATCOM operations. The GATR Tropo antennas are available in C-band frequency.
“GATR’s inflatable Tropo antennas will impact satellite communications for not only the U.S. Army, but also other military forces who use troposcatter communications to transmit voice and data without the use of satellites,” said Mike Twyman, president of Cubic Mission Solutions. “The addition of GATR Tropo antennas into CMS’ communication solutions will strengthen our offerings by providing lightweight, man-portable and ruggedized command, control, communications, computers, intelligence, surveillance and reconnaissance (C4ISR) systems to our customers worldwide.”
Laitan tänne, mutta uskoisin että sopisi uav joukoille mukaan yhteyksien luomiseen sotalueella.
Viimeksi muokattu:
http://www.theregister.co.uk/2016/10/20/gps_spoofing_can_put_yik_yak_in_a_flap/A little machine learning can de-anonymise Yik Yak users, according to researchers from American and Chinese universities.
Yik Yak is an anonymous messaging app that raised US$70 million, acts like a location-aware Twitter and has become a preferred tool of trolls on US College campuses.
The researchers didn't attack the Yik Yak protocol. Rather, they applied themselves to the question of localising the users to messages they sent.
From the paper's abstract:
“We show that we can accurately predict the locations of messages up to a small average error of 106 meters. We also devise an experiment where each message emanates from one of nine dorm colleges on the University of California Santa Cruz campus. We are able to determine the correct dorm college that generated each message 100% of the time.”
In this New York University Tandon School of Engineering release, computer science boffin Keith Ross explains: “At this stage, we can narrow down a location to a building, which when combined with other side information could potentially de-anonymise the author of any given yak.”
The researchers spoofed GPS locations in smartphones to deploy Yik Yak in a couple of university campuses for the test, and then did the same to their own smartphones, to “place” them in different locations in the campuses.
Because Yaks are localised to smartphones in the vicinity of where they're posted, the researchers found it easy to work out which messages were available in different locations, and use that to train their AI to work out which dormitories might be associated with the postings.
As Ross put it: “It wouldn’t be difficult for a professor to figure out the dorm from which a derogatory yak was posted, then couple this information with student housing information to de-anonymise the yak, and that’s concerning.”
Yik Yak has been advised of the issue, and the researchers have suggested that what users can view be less localised
KorpiSISSI
Kenraali
Hybridisodankäynti luennot 19.11.2016 Museo Militariassa.
OHJELMA
klo 10.00 – 12.00 Hybridisota
Luento valottaa tähän mennessä tunnistettuja hybridisodankäynnin eri muotoja ja niiden yhteisvaikutusta. Tietopaketti kansankielellä: mitä- miksi- milloin periaatteella.
klo 12.00 – 12.45 lounas
Museokierros
Hybrisodan historiaa. Vai onko sillä historiaa?
klo 14.30 – 14.50 iltapäiväkahvi
Elektroninen sodankäynti
Perustietopaketti elektronisesta sodankäynnistä.
klo 16.00 Päätös
Kurssin hinta: 30€ (sis. opastettu museokierros, lounas ja kahvi)
Linkki ilmoittautumiseen
https://www.mpk.fi/Default.aspx?tabid=1054&id=90115
Kurssinjohtaja Pekka Wallenstjärna
puh. 040-6861333
OHJELMA
klo 10.00 – 12.00 Hybridisota
Luento valottaa tähän mennessä tunnistettuja hybridisodankäynnin eri muotoja ja niiden yhteisvaikutusta. Tietopaketti kansankielellä: mitä- miksi- milloin periaatteella.
klo 12.00 – 12.45 lounas
Museokierros
Hybrisodan historiaa. Vai onko sillä historiaa?
klo 14.30 – 14.50 iltapäiväkahvi
Elektroninen sodankäynti
Perustietopaketti elektronisesta sodankäynnistä.
klo 16.00 Päätös
Kurssin hinta: 30€ (sis. opastettu museokierros, lounas ja kahvi)
Linkki ilmoittautumiseen
https://www.mpk.fi/Default.aspx?tabid=1054&id=90115
Kurssinjohtaja Pekka Wallenstjärna
puh. 040-6861333
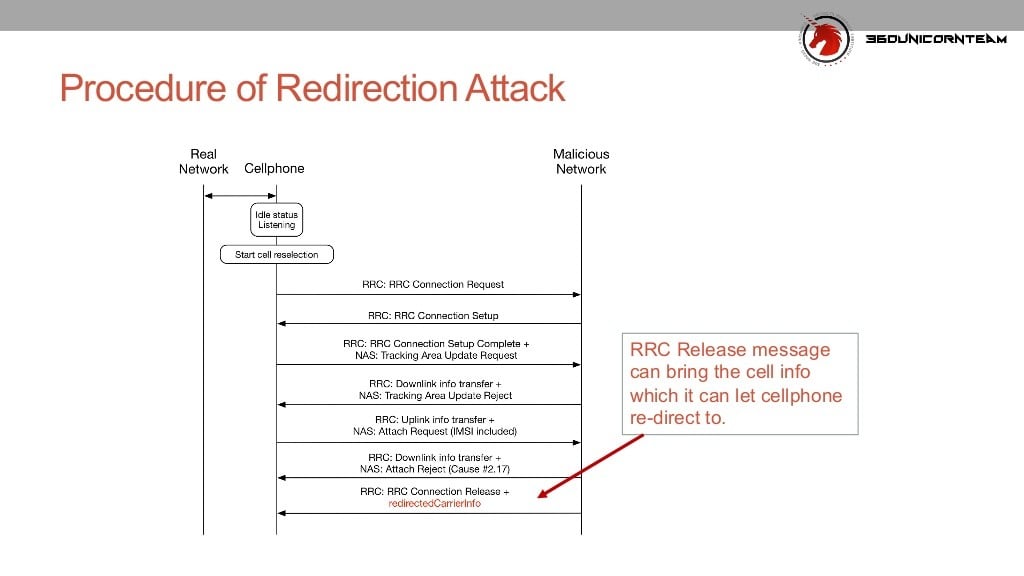
http://www.theregister.co.uk/2016/1..._can_be_intercepted_blacked_out_hacker_finds/Hacker Wanqiao Zhang of Chinese hacking house Qihoo 360 has blown holes in 4G LTE networks by detailing how to intercept and make calls, send text messages and even force phones offline.
The still-live attacks were demonstrated at the Ruxcon hacking confab in Melbourne this weekend, with the demo offering a recording of the hack perpetrated in part on a live network. It exploits fall-back mechanisms designed to ensure continuity of phone services in the event of overloads.
The tested Frequency Division Duplexing LTE network is more popular than TDD-LTE and operates in Britain, the US, and Australia. The competing Time Division Duplexing (TDD) LTE network is more common in Asian countries and in regions where population densities are higher.
Zhang conducted further tests after The Register inquired whether the attacks would work against TDD-LTE and found all LTE networks and devices are affected.
"I asked my colleagues to test TDD-LTE yesterday and it works well, so it really can work against all LTE devices," Zhang says.
"This attack exists [and] it's still reasonable."
The attacks work through a series of messages sent between malicious base stations spun up by attackers and targeted phones.
It results in attackers gaining a man-in-the-middle position from where they can listen to calls or read SMS, or force phones back to 2G GSM networks where ony voice and basic data services are available.
The attacks are not just fit for laboratories. At this year's DEF CON hacker confab one reasearcher used IMSI catcher detection tools to find words
Zhang says the attacks are possible because LTE networks allow users to be handed over to underused base stations in the event of natural disasters to ensure connectivity.
“You can create a denial of service attack against cellphones by forcing phones into fake networks with no services,” Zhang told the conference.
“You can make malicious calls and SMS and … eavesdrop on all voice and data traffic.”
The Third Generation Partnership Project (3GPP) telco body has known of the hack since at least 2006 when it issued a document describing Zhang’s forced handover attack, and accepts it as a risk. The 3GPP’s SA WG3 working group which handles security of LTE and other networks proposed in a May meeting that it would refuse-one-way authentication and drop encryption downgrade requests from base stations.
Three of the fail-over emergency features can be abused for specific attacks, Zhang says; global roaming features allow IMSI capture, battery energy saving for denial of service, and load balancing for redirection.
http://www.theregister.co.uk/2016/10/24/cracking_2g_gsm/The crypto scheme applied to second generation (2G) mobile phone data can be hacked within seconds, security researchers have demonstrated.
The work by researchers from the Agency for Science, Technology and Research (A*STAR), Singapore shows that breaking the A5/1 stream cipher used by 2G is possible using commodity hardware.
Security experts have known the A5/1 was breakable since 2009, so what the Singapore team has done is illustrate the ease with which this is now possible, re-emphasizing the need to update remaining 2G-based mobile communications networks.
"GSM uses an encryption scheme called the A5/1 stream cipher to protect data," said Jiqiang Lu from the A*STAR Institute for Infocomm Research. "A5/1 uses a 64-bit secret key and a complex key-stream generator to make it resistant to elementary attacks such as exhaustive key searches and dictionary attacks."
Weaknesses in the ageing A5/1 cipher, combined with the improved performance of number-crunching hardware, have rendered the crypto system crackable.
The approach adopted by the Singapore-based researchers is more sophisticated than a vanilla brute force (try every possible combination) attack. By harnessing two security weaknesses, the boffins were able to compute a look-up table using commodity hardware in 55 days. Armed with this 984GB rainbow table, determining the secret key used to encrypt communications is possible in as little as nine seconds.
"We used a rainbow table, which is constructed iteratively offline as a set of chains relating the secret key to the cipher output," Lu explained, phys.org reports.
"When an output is received during an attack, the attacker identifies the relevant chain in the rainbow table and regenerates it, which gives a result that is very likely to be the secret key of the cipher."
The researchers used a cracking rig made up of a general-purpose graphics processing unit computer with three NVIDIA GeForce GTX 690 cards, costing about $15K.
More details of the research can be found in a white paper entitled Time–Memory Trade-Off Attack on the GSM A5/1 Stream Cipher Using Commodity GPGPU in the journal Applied Cryptography and Network Security.
tutkielma http://link.springer.com/chapter/10.1007/978-3-319-28166-7_17
gsm on ollut pitemmän aikaa murrettavissa kuin heidän väittämä 2009, mutta tuo melkein teratavun kokoinen rainbow taulu on jotain mitä kaikilla ei ole. Kuitenkin ymmärrättävissä että sitä käyttämällä melkein kaikki on avattavissa minuuteissa ellei nopeammin.
http://www.spacedaily.com/reports/R...ommunication_system_for_military_use_999.htmlRussia has started the development and engineering of a unified satellite communication system for military use; when completed the system will give the country's Ground Forces considerable superiority over the communication technologies of the ground forces of leading foreign states, according to Gen. Maj. Alexander Galgash.It will be a multi-echelon system, Galgash told Life Zvuk radio broadcaster.
The major echelons will be space, aerial and ground. He further explained that while the ground forces are involved in operations on the ground, the communication services, taking into account the physics of the process, use all the echelons from the ground to aerial and space.
There is currently development and engineering work going on within these echelons, which will provide ground forces with a unified third generation system of satellite communication in the space echelon (the system currently in use is of the second generation, the Gen. Maj specified).
There will also be orbital and ground groups which will provide communication in any part of the world. In the aerial echelon it will be provided by rebroadcasting transmitters which will be mounted on various flying and lifting devices including unmanned aerial vehicles (UAV), helicopters and aircraft. By using the physics of allocation process and radio-wave transmission they will increase the transmission range and ensure the command of troops operating in different areas.
The ground echelon is the basis of the field component in the operative strategic system, Galgash said. It will consist of mostly "Redoubt" mobile communication complexes, a basic set of hardware connections and hardware communication control tools.
"Redoubt" allows a combination of different means of communication in a single radio network. The complex provides a reliable and uninterrupted communication with a wind speed of 30 m/s and at a temperature from -50 degrees C to +55 degrees C with remote antenna control, automatic control system, communication security and information protection. "Redoubt" is equipped with an efficient life-support system, which makes its use more comfortable for the crew of the complex.
The complexes will provide communication for high ranking officials, successfully blocking the network from external unauthorized use, videoconferencing, telephone communication, data transmission and automated command of troops.
According to Galgash, this would bring up the percentage of cutting-edge communications technology in the Ground Forces to 45 percent, which is scheduled to go further up to 70 percent by 2020.
http://www.gpsdaily.com/reports/Swarm_reveals_why_satellites_lose_track_999.htmlSatellite engineers have been puzzling over why GPS navigation systems on low-orbiting satellites like ESA's Swarm sometimes black out when they fly over the equator between Africa and South America. Thanks to Swarm, it appears 'thunderstorms' in the ionosphere are to blame.
Launched in 2013, the Swarm trio is measuring and untangling the different magnetic fields that stem from Earth's core, mantle, crust, oceans, ionosphere and magnetosphere - an undertaking of at least four years.
As with many satellites, ESA's three Swarm satellites carry GPS receivers as part of their positioning system so that operators keep them in the correct orbits. In addition, GPS pinpoints where the satellites are making their scientific measurements.
However, sometimes the satellites lose their GPS connection. In fact, during their first two years in orbit, the link was broken 166 times.
A paper published recently describes how Swarm has revealed there is a direct link between these blackouts and ionospheric 'thunderstorms', around 300-600 km above Earth.
http://www.defensetech.org/2016/11/04/31507/BAE Systems announced today it is expanding its work on Cognitive Electronic Warfare Development for the Pentagon’s research agency.
BAE’s Adaptive Radar Countermeasure, or ARC, project is being developed to help airborne electronic warfare systems counter new, unknown and adaptive radars in real time.
“Current electronic warfare systems are limited in their ability to quickly adapt to new and advanced threats because they rely on a database of known threats with predefined countermeasures,” according to the release.
To ensure mission success in future anti-access/area denial environments, electronic warfare systems will need to isolate unknown hostile radar signals in dense electromagnetic environments, and then rapidly generate effective electronic countermeasures, BAE officials maintain.
The cognitive electronic warfare technologies developed for the ARC program employ advanced signal processing, intelligent algorithms, and machine learning techniques, the release states.
Under the contract modification, for Phase 3 of the ARC program, BAE Systems will perform work that includes the planned completion of algorithm development, advanced readiness testing, and key milestones for transitioning the ARC technologies to critical airborne warfare platforms, such as fifth-generation fighter jets, the release states.
