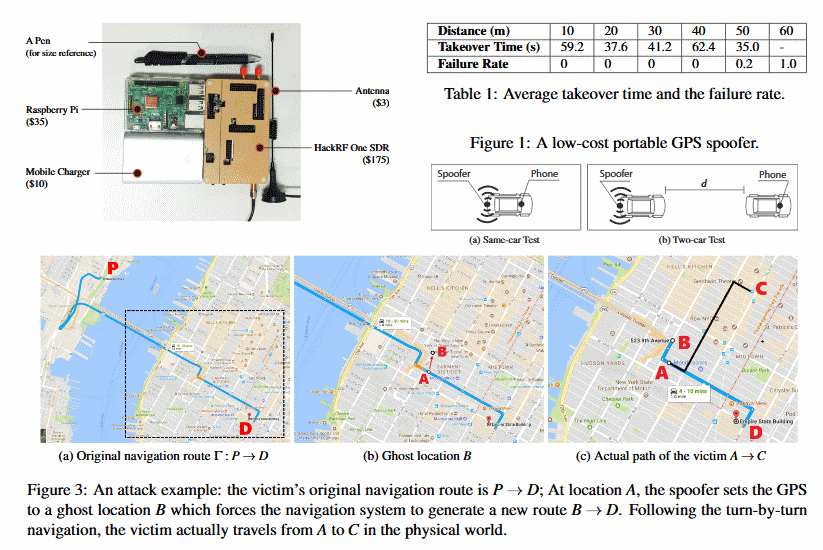
At issue is the fact that critical ship control systems, including IP-to-serial converters, GPS receivers or the
Voyage Data Recorder (VDR), tend to be easily compromised; some on-board devices for instance still run Windows XP and Windows NT, and converters rarely have their admin passwords changed.
Those that do have non-default credentials will likely have such out of date firmware that they’re easily exploited anyway: Munro pointed out that many of the Moxa device servers commonly found aboard vessels were recently found to be vulnerable to a firmware downgrade attack that allowed trivial compromise.
“It’s a low-skill attack,” Munro told Threatpost. “Password security and patch management are so poor at sea that compromise does not require significant expertise. There’s a documented case of a kid finding a mobile drilling platform control system using Shodan and clicking buttons to see what happened. I believe they unintentionally took the dynamic positioning system offline.”
These easily hacked devices communicate with a raft of control systems via a standardized messaging system, called NMEA 0183 messaging (it’s a superset of the messaging format that GPS devices use). These include autopilot systems, propulsion control, dynamic positioning, engine control, ballast control and digital compasses – everything that’s needed to steer a ship off-course or cause catastrophe.
“The messages are usually exchanged using RS485 serial datacomms, either directly or encapsulated over IP networks,” Munro said in
a posting. “In some cases, CAN is used as a bridge between IP and serial. Any point where serial meets IP is a point where the hacker can potentially access the messaging system.”
Once the hacker is able to reach the control systems, it would for instance be possible to replay the
Hoegh Osaka incident, where a car carrier’s ballast tanks weren’t properly filled, which resulted in the ship developing a heavy list during a tight turn out of the port. It narrowly avoided capsize, thanks only to a favorable wind blowing.
“Modern ballast control systems provide remote monitoring and operation from the bridge, usually running on a PC,” Munro explained. “So, the attacker would simply send the appropriate serial data to the ballast pump controllers, causing them all to pump from port to starboard ballast tanks. That change in trim alone could cause a capsize.”
He added, “If the change in ballast wasn’t enough to sink the vessel by itself, when a list had started to develop, send a NMEA message to the autopilot, commanding a turn to starboard. Or, send a helm message commanding the same turn direction. The list, combined with the change in stability when turning, is likely to cause a capsize.”
Access to the control systems could be remote or local, depending on the attacker. PTT has done
prior research on remote attacks over satcoms; and
serial network attacks can be carried out remotely via the satcom connection, or by physically locating the convertors.
“Any half-decent attacker can happily abuse these operating systems all day long and still cover their tracks effectively,” Munro said.
Previous research has shown that other concerning attacks are possible as well, such as
forcing a ship off-course or causing collisions. The issue with remediating the dismal state of maritime security is a lack of clearly defined responsibility for security, according to the researcher.
“It’s a lack of awareness,” he told Threatpost. “Ship owners are rarely the ship operator, charter parties are rarely interested in security. When responsibility and liability for security incidents is unclear, it’s hard to determine who should take control of patching and cyber-risk management. Clarity is urgently required; several organizations such as the [International Maritime Organization]
are taking action, though it will take time for processes to change.”