Täähän se paljon isompi ongelma on kuin lavettien puute, muutama sivu takaperin joku jo laskeskeli että olemassaolevillakin laveteilla Ukraina pystyisi ampumaan ihan mielettömän määrän rakettia jos niitä olisi tuhlattavaksi asti.Näinköhän riittäisi rakettejakaan noin monen laukaisualustan aktiiviseen ja tehokkaaseen käyttöön... GMLRS-raketit ei varsinaisesti ole ehtymätön luonnonvara...
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Ukrainan konflikti/sota
Tyrsky
Eversti
venäjän horinoiden mukaan jo yli kolmesti tuhotut Ukrainan ilmavoimat ovat suorittaneet kuusi ilmaiskua. Näissä on satona korjattu yli 50 örkin päätä, kolme vanhaa mutta paksua vaunua, kolmikko holtittomia raketinheittimiä, yksi tykki sekä panssoituja ja panssaroimattomia ajoneuvoja.
Ai niin ja tietty kirsikkana pohjalla vielä yksi ammusvarasto! Sanoisin että aika hyvin 'haamuilmavoimilta' näin yhden päivän hyviksi töiksi...
Ai niin ja tietty kirsikkana pohjalla vielä yksi ammusvarasto! Sanoisin että aika hyvin 'haamuilmavoimilta' näin yhden päivän hyviksi töiksi...
Antares
Respected Leader
Tämän mukaan taas olisi kuulunut iskuja Daryivkan suunnalta, siellä on yksi Ingulets-joen ylittävä silta. Ehkä isketty sitä vastaan, odotetaan vahvistusta:
Tämä olisi ainakin toinen isku samaa siltaa vastaan, DefMon kirjoitti eilen näin "Today we received information about the bridge in Dar'ivka has been damaged and earlier in the week we have seen damage on the Antonovskiy Bridge" LÄHDE
DefMon eilisestä viestiketjusta yleiskuva, johon on merkitty Inhulets-joen ylittävät sillat: LÄHDE
Dar'ivkan sijainti kartalla, tämä on tärkeän M14 valtatien silta:
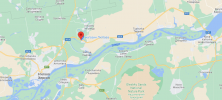
Tämä olisi ainakin toinen isku samaa siltaa vastaan, DefMon kirjoitti eilen näin "Today we received information about the bridge in Dar'ivka has been damaged and earlier in the week we have seen damage on the Antonovskiy Bridge" LÄHDE
DefMon eilisestä viestiketjusta yleiskuva, johon on merkitty Inhulets-joen ylittävät sillat: LÄHDE

Dar'ivkan sijainti kartalla, tämä on tärkeän M14 valtatien silta:

Sodan päivä 150, lyhyt katsaus:
Meritopolissa (kuulemma) junanraiteet poksautettu.
Tämä ( ):
):

Brittimodin päivän katsaus:
Meritopolissa (kuulemma) junanraiteet poksautettu.
Tämä (
 ):
):
Brittimodin päivän katsaus:
Viimeksi muokattu:
Isoalaviiva
Eversti
Kyllä noi pienemmätkin toimivat, kunhan osumaa siirtää oikeaan kohtaan esim.Juu siihen tarvitaan joko ballistisia ohjuksia tai maanjäristyspommeja. Bunker busterit menisivät läpi ja räjähtäisivät pohjassa. Ellei niitä voi säätää herkiksi. Tosin jenkit tuskin MOAB tai Massive ordnance penetrator pommeja Ukrainalle antonivien kannettavaksi.
Noihin kantaviin palkkeihin, itse kansihan ei kanna yhtään mitään.
Liitteet
Poisto: sekoilua…
Sodan päivä 150, lyhyt katsaus:
Meritopolissa (kuulemma) junanraiteet poksautettu.
Tämä ():

Brittimodin päivän katsaus:
Eikös tuolla Transnistriassa ollut joku valtava Varsovan liiton aikainen asevarikko ? Onko ryssät päässeet sen jo tyhjentään ? Tuohan olisi mainio saalis Ukrainalle.
Antares
Respected Leader
Viron entinen presidentti Ilves on vetänyt taas sanansäilänsä esiin ja nyt hän on ottanut kohteekseen Orbanin Unkarin - ja ihan aiheesta! Vaikka Unkarilla ei tosiaan olekaan rannikkoa, jonne voisi parkkeerata LNG-terminaalia jne, niin pitää myös muistaa että ihan yhtä hyvin he olisivat voineet rakentaa vaikkapa ydinvoimaloita mutta ovat ihan itse päätyneet lussuttamaan energiaansa venäjän kaasunisästä.
Lisäksi on Suomenkin kannalta hyvä että näitä Unkarin ja Orbanin epämääräisiä toimia kritisoidaan valtionpäämiesten taholta - vaikkakin tässä tapauksessa entisen sellaisen, mutta kyllä entisilläkin huippupoliitikoilla on kovin kuuluva ääni. Suomen kannalta tämä on hyvä siksi että jos meinaavat Unkarissa yhtään heittäytyä Suomen ja Ruotsin NATO-jäsenyyden ratifioinnin osalta poikkiteloin, niin voidaan helposti lyödä pöytään aiempaa tuoretta syntilistaa ja koska Unkarilla ei ole edes mitenkään strategisesti merkittävä sijainti tai muuta korvaamatonta tarjottavaa niin niin 'do the math'...
Tämä erittäin laadukas artikkeli laitettiin tänne eilen, mutta lainaan siitä pari pätkää jotka kertovat miten vakavia vaikutuksia ryssän asiamiehillä voi olla laajempaan turvallisuuteen: LÄHDE
The large-scale Russian TeamSpy attack was discovered not by the counterintelligence of Western countries, but by experts at the cyber defence center of the Hungarian National Security Authority (NBF), according to a cyber security expert familiar with the incident. The Hungarian center, called the Cyber Defence Management Authority (CMDA), set up in 2011, gathered expertise and cyber defence capabilities over ministries and state agencies, and were so successful that one of their Hungarian experts was elected to head NATO’s cyber defence task force.
According to a cyber security expert familiar with the incident, the Hungarians responded to the TeamSpy attack with an aggressive counterattack. They hacked into the Russian attack infrastructure, identified Russian hackers operating from Russian and Ukrainian Internet cafes, among others, and obtained the target list of TeamSpy attacks. In a joint operation with NATO partners, by accessing the victims’ computers around the world, they simultaneously shut down infected devices, cutting off Russian hackers from a wealth of information. Such an operation requires serious organisation and expertise, which, according to several Direkt36 sources familiar with the case and involved in cybersecurity, shows how advanced Hungarian cyber defence was at the time.
It was in the early 2010s that Russian intelligence services – mainly the Russian Federal Security Service (FSB) and the Russian military intelligence (GRU) – really started to get into hacking. “For Russia, cyber warfare is part of a permanent information warfare. This warfare is based on the perception that the Western world wants to undermine Russia’s position of power and is ultimately engaged in a comprehensive and continuous effort to subjugate the country,” AH’s (AH = Constitution Protection Office) former senior national security officer Péter Buda told Direkt36.
Since the Russians see NATO simply as a military tool of the United States, Buda said, their cyber espionage “is mainly aimed at detecting information and conflicts of interest that could disrupt the unity of the NATO alliance, in addition to the continuous monitoring of capabilities and intentions”. The cyber espionage method, also used by the Russians, called Advanced Persistent Threat (APT), does not aim at immediate, visible damage, like a simple hacker attack, but at a persistent presence within the targeted IT system.
While Prime Minister Viktor Orbán was already advertising his pivot towards Russia and China, Russian hackers of the GRU and FSB – hacking groups known as APT28 and APT29 – treated Hungary as an enemy and attacked it just as they did other EU and NATO member states. An official of the Orbán government at the time, said that in 2012-2014, in addition to the Hungarian Ministry of Foreign Affairs, the Ministry of Interior and even the Ministry of Defence were compromised by hackers. Based on their digital footprint and intelligence sharing with NATO/EU partners, they were also very likely Russians.
-
Former Cyber Defence Management Authority (CDMA) head Ferenc Frész said in a 2015 presentation that much of their work was about addressing these vulnerabilities. But by then the CDMA had virtually ceased to exist. In his presentation, Frész claimed that Hungarian cyber defence had been dismantled in a way that had completely eliminated Hungary’s defence capabilities, and that “it was all done under Russian economic pressure”. He did not elaborate on what basis he made this claim, and when contacted by Direkt36 he declined to comment on his statement at the time.
The spectacular pro-Russian turn in Hungarian politics came in 2014, after Orbán and Putin announced their agreement on the Paks2 nuclear power plant expansion. Then Péter Szijjártó, who already had extensive Russian connections, took over the leadership of the MFA (MFA = Ministry of Foreign Affairs and Trade). In November 2014, the head of the National Security Authority was fired, the institution was brought under the Ministry of Interior, and a few months later the staff of the Cyber Defence Management Authority was laid off as part of a “reorganisation”.
According to a cybersecurity expert familiar with the case, the Orbán government began to see Hungarian cyber defence as a linchpin of the Hungarian-Russian rapprochement, and the agreement on the Paks nuclear expansion, among other things, brought a negative turn. Another cybersecurity expert added that CDMA’s staff have also isolated themselves by revealing to various ministries, in an unvarnished style and “without much diplomacy”, what critical vulnerabilities they had found in government networks.
Under the third Orbán government, cyber defence tasks were taken over by agencies under the Ministry of Interior, primarily the Special Service for National Security (SSNS). However, after the abolition of the Cyber Defence Management Authority, in fact, all the intelligence and state agencies started to do a little bit of cyber defence. According to a former official of the Orbán government, the consequence of this include that the various agencies regularly point fingers at each other or wait for each other, operate in isolation from each other and sometimes there is even outright rivalry between them.
The next big wave of Russian attacks instantly showed the weaknesses of the new set-up.
-
"Hyvien suhteiden ylläpitämiseksi" on siis ajettu alas oman maan selvästi toimiva cyber-puolustus. Se on nimellisesti olemassa, mutta hajautettu usean eri organisaation alle. Voisi sanoa "hajota ja hallitse", tosin tässä yhteydessä hallitsija on ryssä ja heidän tiedustelupalvelunsa. Toki kun tilanne on tämä, sen varmasti tiedostavat myös muiden maiden tiedusteluviranomaiset, joten yhteydet Unkariin pyritään minimoimaan jottei sieltä olisi kanavia mitä pitkin tunkeutua syvemmälle. Artikkelissa kirjoitetaan että osa Yhdysvaltain vaaleihin puuttuneista hyökkäyksistä tuli Unkarin verkosta, joten selvästi työtä riittää.
Orbanilla ei varmasti ole mitään halua puuttua tähän. Aikaisemmin joku kirjoitti siitä, miten Unkarilla ei ole pääsyä merelle ja siten kaasun laivaaminen ei ole mahdollista. On siis sidottu väistämättä ryssän kaasuun, mikä ohjaa kaikkea tekemistä. Totta sinänsä, mutta EU:n sisällä on sovittu kaasun siirroista eri maiden varantojen välillä. Ainakin teoriassa tämän pitäisi onnistua, en ole varma kuinka yleistä se on käytännössä. Muistaakseni tästä sovittiin viimeistään 2014 tapahtuneen Krimin valtaamisen jälkeen, ellei jo aikaisemmin.
Viimeksi muokattu:
Tyrsky
Eversti
Tässä kuvassa on jotain käsin kosketeltavaa karua kauneutta. Tällaiset kuvat ovat niitä jotka paistuvat ihmisten muistikuvien raidoille, koska sisältävät niin ristiriitaisia asioita mutta tästä huolimatta ovat kuvassa täydellisessä harmoniassa.
Kuva todellakin kertoo siitä Ukrainan normaalin ihmisen kekseliäisyydestä, viitseliäisyydestä sekä tilanteeseen mukautuvuudesta. Itselleni tuskin olisi tullut pieneen mieleenikään käyttää vaunun runkoa kompostina, upottaa tykkitornia maisemaan tekemällä kukkapenkki putken suuntaisesti sekä tehdä pois paikoiltaan poksahtaneen tykkitornin ja vaunun väliin vieläpä kaalimaa!
Karuudessaan kaunista!
Kuva todellakin kertoo siitä Ukrainan normaalin ihmisen kekseliäisyydestä, viitseliäisyydestä sekä tilanteeseen mukautuvuudesta. Itselleni tuskin olisi tullut pieneen mieleenikään käyttää vaunun runkoa kompostina, upottaa tykkitornia maisemaan tekemällä kukkapenkki putken suuntaisesti sekä tehdä pois paikoiltaan poksahtaneen tykkitornin ja vaunun väliin vieläpä kaalimaa!
Karuudessaan kaunista!
Antares
Respected Leader
Eikös tuolla Transnistriassa ollut joku valtava Varsovan liiton aikainen asevarikko ? Onko ryssät päässeet sen jo tyhjentään ? Tuohan olisi mainio saalis Ukrainalle.
Varaston tarkat koordinaatit: 47°45'36.3"N 29°12'15.5"E
Löytyy myös ainakin Google Mapsista ihan vain jos hakee "Cobasna ammunition depot" ja löytyy ihan hyviä kuvia myös, ei sinänsä siis mikään super salainen paikka.
Se on kylmän sodan aikaisen 14. Kaartin Armeijan vanha varasto, väitetysti 20 000 tonnia "Soviet-era weapons" - tosin tietyissä kirjoituksissa tuo kääntyy muotoon 20 000 tonnia räjähteitä.
Olen nähnyt aikaisemmin spekulaatiota että tuon ison ammusvaraston muodostama uhka olisi näitä puheita pienempi: yli puolet varastoidusta ampumamateriaalista käyttökelvotonta / varastoiän takaraja ylitetty JA toisaalta sanovat että kaksi kolmasosaa kaikesta Transnistrian sotavälineistä ("military equipment in Transnistria") on joko osaksi tai kokonaan käyttökelvottomassa kunnossa. Toki näitä puheita ja spekulaatioita on mahdoton todentaa.
Ukrainan MoD tiedotti pari kuukautta sitten että Venäjällä olisi Transnistriassa ainoastaan 300 sotilasta / "rauhanturvaajaa" ja nämäkin olisi sidottu tuon ammusvaraston vartiointiin, tosin välillä näkee arvioita joiden mukaan määrä olisi jopa 2 000.
Transnistrialla itsellään on "militia" tyylisiä joukkoja tai kai ne virallisesti ovat "sotajoukkoja". Vilkaisin wikipediasta, mitä heidän asevoimista kirjoitetaan siellä (en ehdi parempaa lähdettä tähän hätään, suolan kanssa siis "tiedot"):
As of 2007, the armed forces and the paramilitary of Transnistria were composed of around 4,500–7,500 soldiers, divided into four motorised infantry brigades in Tiraspol, Bender, Rîbnița, and Dubăsari.[106] They have 18 tanks, 107 armoured personnel carriers, 73 field guns, 46 anti-aircraft installations, and 173 tank destroyer units. The airforce is composed of 9 Mi-8T helicopters, 6 Mi-24 helicopters, 2 Mi-2 helicopters, and several fixed-wing aircraft, including, An-2, An-26 and Yak-18 types
Active personnel: 5 500
Reserve personnel: 20 000
Tässäkin voi miettiä, mikä määrä tuosta listatusta kalustosta on pidetty käyttökelpoisessa kunnossa. Ne ovat pitkälti Neuvostoliiton jäämistöä, ehkä Venäjä on toimittanut sen jälkeen jotain kalustoa, ehkä ei. En olisi kovin huolissaan heidän kalustosta, toki muutamalla panssarivaunulla ja tykillä saa pahaa jälkeä aikaan jos osuu sopivasti.
Vuoden 1992 isompien kahinoiden aikaan Transnistrian militia joukkojen kooksi on arvioitu 12 000, tosin numerolle ei ole varmuutta. Epäilen tuota määrää, kuolleiden määräksi arvioitu molemmin puolin muutamia satoja, kuitenkin enimmilläänkin alle tuhat. Venäläisten vapaaehtoisten määräksi arvioitu mitä tahansa 200 - 3 000 väliltä. Lisäksi tuon kahinan aikaan Transnistriassa oli 14. Kaartin Armeija ja sen 14 000 miestä varusteineen. Heistä osa osallistui ihan avoimesti: T-64 vaunuja oli käytössä, samoin raskasta tykistöä ja jos ei muuten, niin kahinan päättänyt iso tykistökeskitys tuli heiltä.
Jos siis tuolla seudulla alkaisi oikea kahina, niin se tulisi varmasti keskittymään muutaman suuremman asutuskeskuksen alueelle. Arvatenkin Cobasna, joka sijaitsee alueen pohjoisosassa olisi yksi näistä. Alueen "pääkaupunki" Tiraspol olisi varmasti toinen, kuvaan merkityt pari muuta suurempaa kaupunkia olisivat myös jossain vaiheessa.
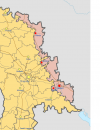
Riippuu siitä, millaisella innolla paikalliset tarttuisivat aseisiin, mutta voisi olla hyvinkin suuria miestappioita puolin ja toisin. Toinen vaihtoehto on tietysti Irakin 2003 kaltainen romahdus: paikallisia ei kiinnosta osallistua muutaman hullun sotaan, joten alue vallattaisiin kohtuullisen nopeasti. En epäile etteikö Ukrainalla olisi kykyä lähettää muutama kymmenen tuhatta miestä varusteineen Transnistriaan, jos siis näin päätetään. Alue on pieni suikale muodoltaan, joten taistelut siirtyisivät varmasti nopeasti asutuskeskuksiin.
Jos en muista väärin, niin alue ei ole vuoristoista mutta kumpareita ja mäkiä on. Alueen länsirajan muodostaan Dnestr-joki, joten Moldovan suunnasta tuleva hyökkäys on huomattavasti helpompi torjua. Ukrainan suuntaan ei juurikaan ole maastonesteitä eikä alueella on paljoa syvyyttä missä puolustaa: arvioin karkeasti että Ukrainan rajalta on kohdasta riippuen 5-15 km Dnestrin rantaan. Tällaisen alueen puolustaminen johtaisi melko väistämättä puolustuksen keskittymiseen kaupunkien alueelle, ei ole juuri muuta vaihtoehtoa.
Viimeksi muokattu:
tulikomento
Supreme Leader
Ryssän viihdytyskiertue siellä jossain. Yleisöä paikalla suorastaan valtavasti ja kaikilla näyttää olevan kivaa.
Ukrainan presidentin neuvonantajan Oleh Ustenkon mukaan Ukrainassa on tällä hetkellä valtavat määrät viljaa, jota Ukraina haluaisi kuljettaa maailmalle Mustanmeren satamien kautta.
Ustenkon mukaan Ukrainan siiloissa on viljaa lähes 10 miljardin euron edestä.
Ukrainassa on tällä hetkellä 20 miljoonaa tonnia viljaa siiloissa ja uuden sadon myötä viljaan määrä moninkertaistuu.
Ustenkon arvion mukaan uusi sato tuottaa noin 40 miljoonaa tonnia lisää viljaa.
Niin suuren viljamäärän viemiseen Mustanmeren satamien kautta vaatisi lähes vuoden normaalioloissa, mutta sotatilanteen vuoksi vienti on hidastunut.
Ellei satamien toimintaa saada turvattua, viljan kuljetukseen menisi 20–24 kuukautta, eli noin kaksi vuotta, arvioi Ustenko.
Yle uutisten seuranta Venäjän hyökkäyksestä siirtyi toiseen artikkeliin
Tästä artikkelista löytyvät sodan tärkeimmät tapahtumat aikaväliltä 12.2.–28.12.2022.
Ainakin 358 lasta on kuollut ja yli 684 haavoittunut Venäjän hyökkäyssodassa, uutisoivat verkkojulkaisu The Kyiv Independent ja uutiskanava Al Jazeera.
Tieto perustuu Ukrainan valtakunnansyyttäjänviraston lausuntoon.
Todelliset luvut ovat todennäköisesti huomattavasti korkeammat, virasto huomauttaa medialähteiden mukaan.
Viraston mukaan lisäksi yli 220 oppilaitosta on tuhoutunut ja lähes 2200 vaurioitunut Venäjän hyökkäyksessä.
Kyberhyökkäysten määrä Suomessa on pysynyt normaalina Venäjän hyökkäyssodasta huolimatta, kerrotaan liikenne- ja viestintävirasto Traficomista.
Traficomin kyberturvallisuuskeskuksen tietoturva-asiantuntija Matias Mesiän mukaan Suomessa suojaudutaan edelleen samankaltaisilta uhkilta kyberturvallisuuden osalta kuin aiemminkin.
Iso osa kyberturvallisuuskeskukseen tulevista tietoturvamurtojen ilmoituksista liittyy sosiaaliseen mediaan. Keväällä sometietomurroista tuli keskukselle parhaimmillaan kymmeniä ilmoituksia päivässä, ja edelleen niitä tulee päivittäin.
Barely 12 hours after Moscow signed a deal with Ukraine to allow monitored grain exports from Ukraine’s southern ports, Russia targeted the country’s main port of Odesa – through which grain shipments would take place – with cruise missile strikes.
The attack raised new doubts about the viability of the deal, which was intended to release about 20m tonnes of grain to ward off famine in parts of the developing world.

Between port bombings and air raid sirens, life in Odesa goes on
The new grain deal should help the Black Sea port’s economy – but existence has been hollowed out by the pressure of war
“Ideologically, Putin views Odesa as the heart of his ‘Novorossiya’ strategy,” wrote Christine Karelska for the Visegrad/Insight website last week. “He is entrapped by the illusion that Odesa’s residents are waiting for the Russian occupiers to ‘liberate’ them.
“From a geopolitical point of view, Odesa is vital for other regional players. A hypothetical invasion of this city will destabilise much of the region and open up neighbouring countries for an attack. Moldova will undoubtedly be next if Odesa falls.”
In the meantime life, as in other Ukrainian cities one step removed from the immediate frontline, continues but in an attenuated fashion.
fulcrum
Greatest Leader
Jos siis tuolla seudulla alkaisi oikea kahina, niin se tulisi varmasti keskittymään muutaman suuremman asutuskeskuksen alueelle. Riippuu siitä, millaisella innolla paikalliset tarttuisivat aseisiin, mutta voisi olla hyvinkin suuria miestappioita puolin ja toisin. Toinen vaihtoehto on tietysti Irakin 2003 kaltainen romahdus: paikallisia ei kiinnosta osallistua muutaman hullun sotaan, joten alue vallattaisiin kohtuullisen nopeasti. En epäile etteikö Ukrainalla olisi kykyä lähettää muutama kymmenen tuhatta miestä varusteineen Transnistriaan, jos siis näin päätetään. Alue on pieni suikale muodoltaan, joten taistelut siirtyisivät varmasti nopeasti asutuskeskuksiin.
Visegradilla on taipumus hiukan keulia jutuissaan: tuskin kellään paikallisella on haluja jäätyneen konfliktin sulattamiseen väkivallalla. Moldova ja Transnitria eivät elä sotatilassa.
Isänmaan puolesta
Majuri
putinin haaveilemien nyky pioneeri nuorten perustamisen haasteista.
Siinä ja kinttaalla kuuluuko tähän ketjuun, mutta äkkiä tapahtuvan venäjän yhteiskunnallisen autoritäärisen muutoksen vuoksi... Muutosta joka alueella

 www.is.fi
www.is.fi
Siinä ja kinttaalla kuuluuko tähän ketjuun, mutta äkkiä tapahtuvan venäjän yhteiskunnallisen autoritäärisen muutoksen vuoksi... Muutosta joka alueella


Putin turvautui Neuvostoliiton keinoihin – yrittää nyt manipuloida nuoria
Venäjän presidentti Vladimir Putin on hyväksynyt joukon lakeja, jotka pönkittävät hänen valtaansa. Ideologinen vaikuttaminen porautuu syvemmin myös kouluihin, joissa opettajat jo valvovat nuorten poliittisia mielipiteitä.
Antares
Respected Leader
Visegradilla on taipumus hiukan keulia jutuissaan: tuskin kellään paikallisella on haluja jäätyneen konfliktin sulattamiseen väkivallalla. Moldova ja Transnitria eivät elä sotatilassa.
En minäkään usko sotaan tuolla seudulla. Sama tilanne Valko-Venäjän osalta: puhetta ja rinnan pöyhistelyä riittää, mutta halua todelliseen sotaan ei ole.
Moskova on varmasti käskenyt pitämään meteliä, jotta se sitoisi edes pienen osan Ukrainan joukoista näille rajoille.
There was no fear, no defeat in the eyes of Valentina (not her real name) – only quiet determination. She spoke calmly about the Russian soldiers, her younger son’s age, who raped her and her friend in a small village outside of Kyiv. When her friend’s husband tried to stop them, they shot him dead. I asked whether she wanted to pursue the case in court, and she did not hesitate. “To be able to live, I need to see him either dead or behind bars,” she said.
I have been documenting war crimes in different parts of the world for more than two decades, and every time I agonise about how to ask survivors whether they want to pursue justice. At what is probably the most traumatic moment of their lives, offering up an abstract concept like justice as a solution seems insensitive. But, every time, people like Valentina prove me wrong.

Victims of war crimes in Ukraine have an unprecedented chance to seek justice | Anya Neistat
The principle of ‘universal jurisdiction’ is gaining ground, a real boon for survivors
Now, Ukrainian survivors of horrendous crimes committed during the Russian invasion have a unique and unprecedented opportunity to pursue justice on multiple fronts. The Ukrainian prosecutors have opened thousands of cases, and the office of the prosecutor of the international criminal court, supported by dozens of ICC member countries, moved swiftly to launch an investigation.
Ukrainians can also file criminal complaints in many other countries under the principle of universal jurisdiction, which allows countries to prosecute the most serious crimes regardless of where they have been committed or the perpetrator’s nationality. This principle has been developing since the Second World War as a mechanism to pursue justice for the survivors of mass atrocities. There are more than 150 other countries where cases can be brought under this principle – but so far, only a handful, mainly in western Europe, have used it.
It has never been simple. Legal requirements for bringing cases under universal jurisdiction principles vary and often require the presence of the perpetrator or some other “link” to the country. Foreign prosecutors are sometimes reluctant to open investigations, knowing that they may not have access to countries where crimes have been committed and will receive no cooperation from the authorities. The witnesses and victims may be far away, making it difficult to put a case together. And finally, the political will to go after members of the foreign military forces or officials is often lacking.
Another benefit of bringing these universal jurisdiction cases forward, especially while the war rages on, is the clear message it sends: Russian soldiers and Russian commanders are on notice. For now, they think they are invincible – largely because Russian forces have not faced justice for similar crimes in Chechnya, Georgia or Syria. But today there’s a new playbook.
Ukrainian President Volodymyr Zelensky has accused Russia of "barbarism" after a missile attack on the port of Odesa.
A landmark deal to resume Ukraine's grain exports - signed hours before the strike - now hangs in the balance.
Kyiv has said preparations are still under way to resume the grain exports despite the apparent breach.
Russia has said it carried out the strike but said they were targeting a Ukrainian naval vessel.
Ukrainian military officials have admitted that a ship was hit but have not said whether it was a military or civilian vessel.
In his comments, President Zelensky said the strike showed that Moscow cannot be trusted to stick to the deal.
The BBC's Paul Adams says Moscow presumably argues - but has not so far said - that the attack did not represent a violation of the agreement signed in Istanbul on Friday.
The text says parties have undertaken not to attack merchant and other civilian vessels and port facilities engaged in the transportation of grain.

Ukraine war: Zelensky accuses Russia of 'barbarism' over Odesa attack
A landmark grain deal is in doubt after missiles hit the port of Odesa in a widely condemned attack.
www.bbc.co.uk
Antares
Respected Leader
putinin haaveilemien nyky pioneeri nuorten perustamisen haasteista.
Siinä ja kinttaalla kuuluuko tähän ketjuun, mutta äkkiä tapahtuvan venäjän yhteiskunnallisen autoritäärisen muutoksen vuoksi... Muutosta joka alueella

Putin turvautui Neuvostoliiton keinoihin – yrittää nyt manipuloida nuoria
Venäjän presidentti Vladimir Putin on hyväksynyt joukon lakeja, jotka pönkittävät hänen valtaansa. Ideologinen vaikuttaminen porautuu syvemmin myös kouluihin, joissa opettajat jo valvovat nuorten poliittisia mielipiteitä.www.is.fi
Ei mitään uutta auringon alla sinänsä: https://en.wikipedia.org/wiki/Nashi_(youth_movement)
Moniko muistaa että Nashi lakkautettiin virallisesti vuonna 2019, tosin todellinen jäsenkato ja hajaannus alkoi jo vuosia ennen tätä?
Nashia edelsi "Walking Together" joka oli jo unohtunut minultakin: https://en.wikipedia.org/wiki/Walking_Together
Näitä vastaavia järjestöjä heillä varmasti riittää, tässä vielä yksi: https://en.wikipedia.org/wiki/Young_Guard_of_United_Russia
United Russia eli Putinin puolueen nuorisojärjestö. Minä olen jo aikaa sitten laittanut kaikki nämä "Putinjugendin" alle, päämäärä on sama vaikka jotain teoreettisia sävyeroja olisikin.

